Researchers forced 28,000 printers worldwide to print out guidelines on printer security.
A majority of users are concerned about the security of their laptops, desktops, and mobile phones. They use the most reliable antivirus tools and VPN software to ensure optimum privacy while surfing the net.
However, when it comes to securing our printers, we tend to turn a blind eye. This ignorance may have detrimental repercussions. To highlight this crucial aspect, CyberNews’ researchers decided to warn printer owners worldwide about the need to strengthen printer security.
The attack started with researchers scanning the IoT search engine Shodan to locate unprotected printers and discovered over 800,000 printers connected to the internet. Shodan is used to identify exposed or at-risk surveillance devices, databases, solar devices, wind turbines, unprotected networked printers, etc.
The researchers decided to target 50,000 of those printers and sent printing requests using a customer printing script. Around 27,944 devices accepted this command and printed out a message the researchers instructed the devices to print. The message read:
“This printer has been hacked.” It was followed by a comprehensive set of instructions on how to protect internet-connected printers.
A full preview of the printout can be seen below:
The researchers noted that contrary to public perception, the threat is real and unprotected printers can lead to exploitative scenarios. An unsecured IoT device is open to all sorts of abuses. If they can exploit such a large number of printers so quickly, an attacker with nefarious objectives could have done much more.
Such convenient access to printers connected to the internet, just like IoT devices, can allow a remote threat actor to exfiltrate other printing requests to obtain classified or sensitive data. Also, an attacker can plant botnets to use the device in DDoS attacks or install a crypto-miner to raise your electricity bills.
According to the blog post, the guidelines sent out by the researchers entailed four steps to secure the printers. These included:
- To appropriately configure the network settings so that the printer accepts commands from specific ports only. Such as setting the IPPS protocol through SSL port 443.
- To set up up a firewall to filter out dubious incoming remote access requests.
- To check and install the latest firmware version and updates.
- To set unique and strong passwords for IoT devices.
Not for the first time
This however is not the first time when a feat like this has been carried out. A couple of years back, hackers took over thousands of printers and sent alerts to users about their vulnerability.
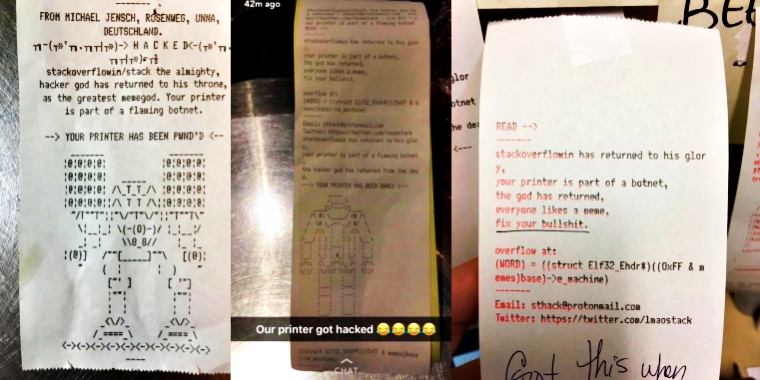
In two separate incidents, a hacker who happened to be a fan of popular YouTuber PewDiePie hacked 100,000 and then 50,000 printers to promote the already popular YouTuber. Here’s how is looked like:
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.