There has been no confirmation from any of the universities whether their cyberinfrastructure was breached or the Cl0p ransomware gang demanded any ransom money to extort the data.
In a recent update, the infamous Cl0p ransomware group claimed to gain access to financial documents and passport information that allegedly belonged to students and staff from six top universities in the United States.
SEE: Cl0p ransomware gang hits Aviation giant Bombardier
The group began posting the alleged stolen data online on the 29th of March. The universities included the following:
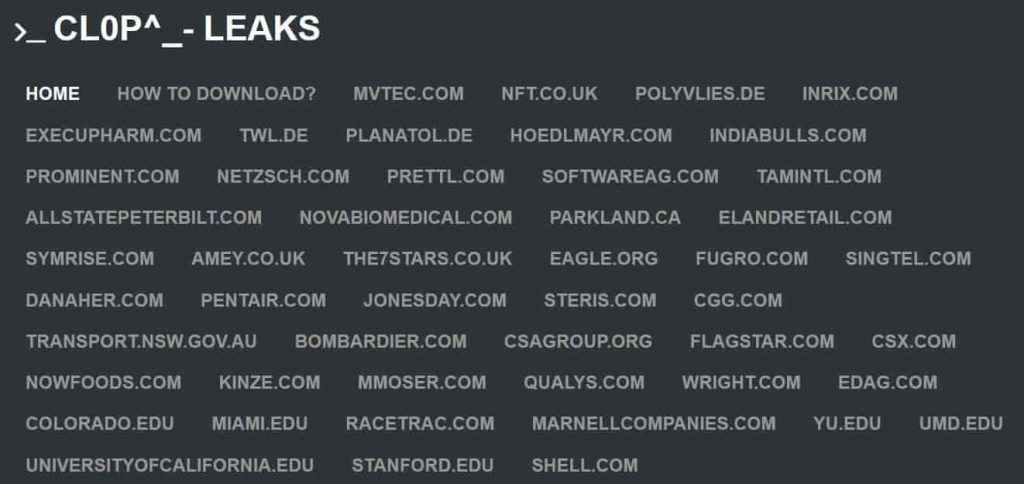
- The Yeshiva University
- The Stanford University
- The University of Miami
- The University of Maryland
- The University of Colorado Boulder
- The University of California, Merced
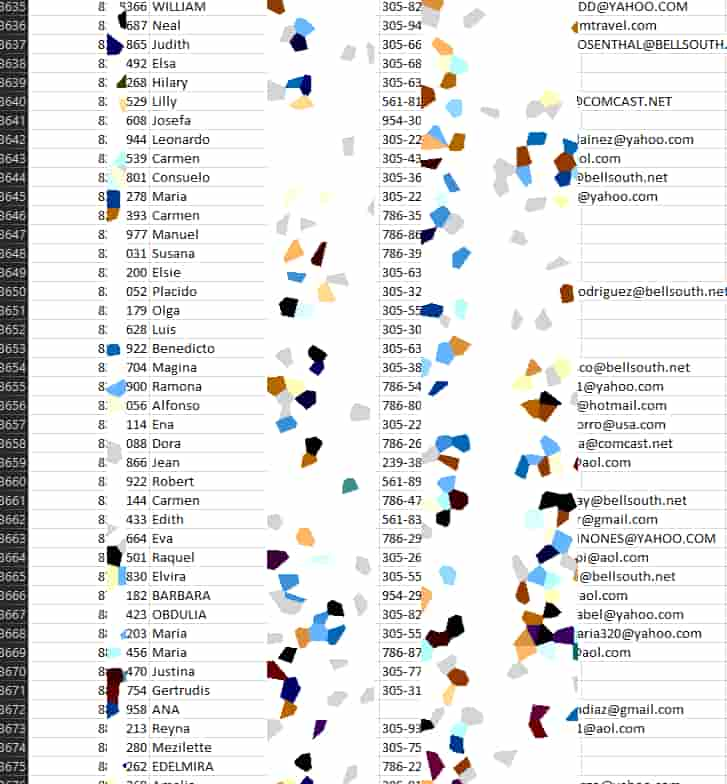
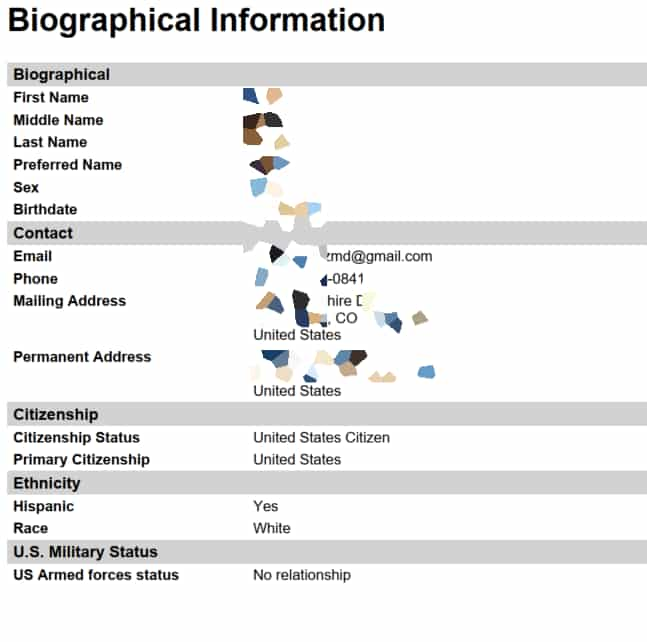
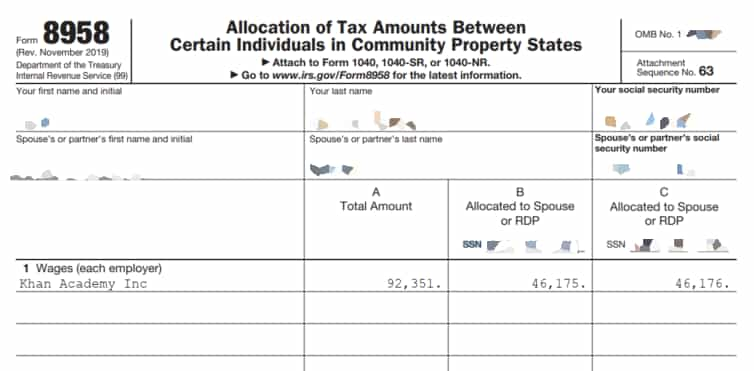
The records leaked by Cl0p ransomware and extortionist gang included screenshots revealing federal tax documents, requests for tuition remission paperwork, applications for the Board of Nursing, passports, and tax summary documents.
This meant that several individuals were affected because the leaked data snapshots exposed sensitive information which included:
- Photos
- Dates of birth
- home addresses
- Passport numbers
- Immigration status
- Names of individuals
- Social Security numbers
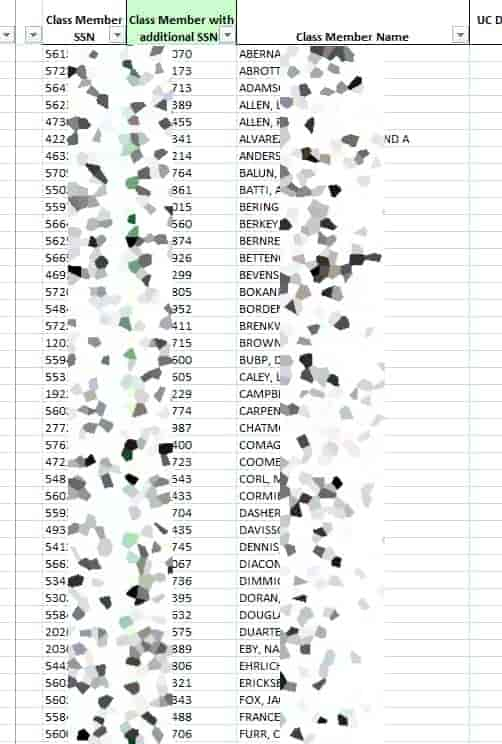
On the other hand, Hackread.com saw several more screenshots that were posted by the group including lists of individuals and their Social Security numbers, retirement documentation, and 2019/2020 benefit adjustment requests.
Not only this, but the leaked data also appears to include late enrollment benefit application forms for employees and the UCPath Blue Shield health savings plan enrollment requests.
It is worth noting that this is not unusual for the Cl0p ransomware group since they have already been linked to a string of cyberattacks against various businesses.
Clop is one of the many cybercriminal groups that use a ‘double-extortion’ tactic where the ransomware is deployed on a compromised machine first, and then the threat actors threaten to post the corporate or sensitive stolen datasets on a leak site unless the blackmail demands are met.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.