A Twitter employee was tricked into phone phishing allowing hackers to access the company’s internal support tool and hack into verified accounts.
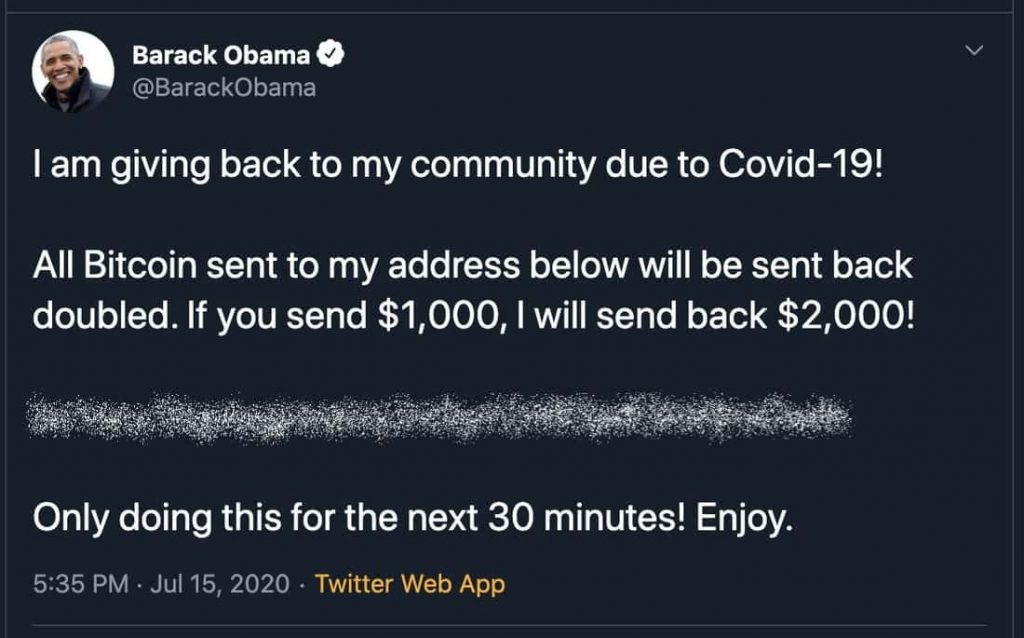
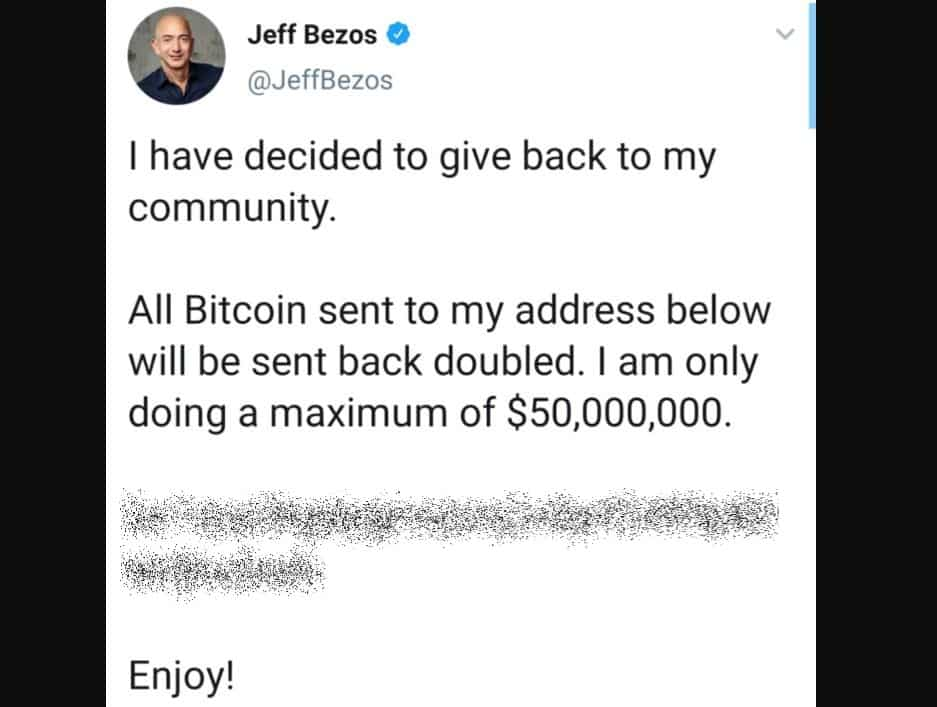
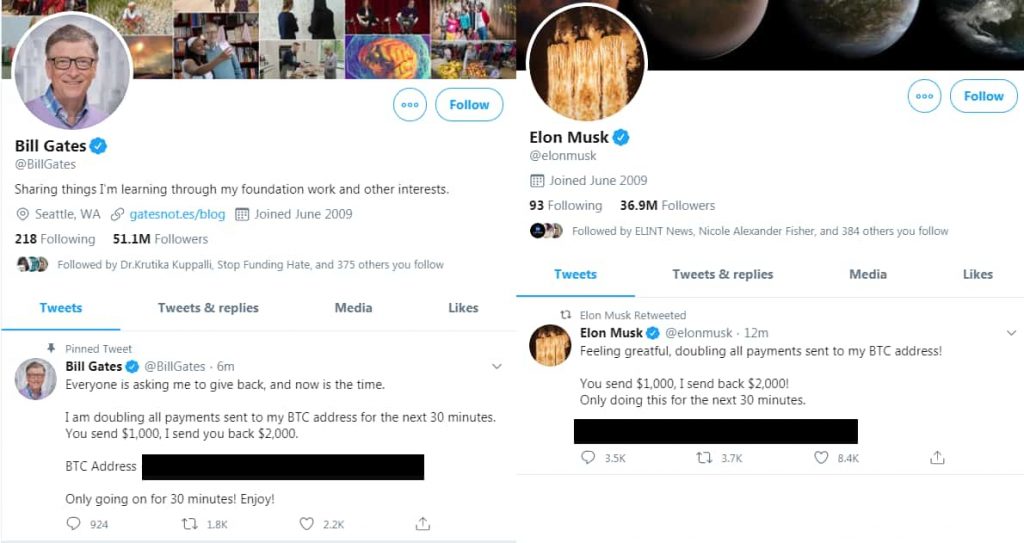
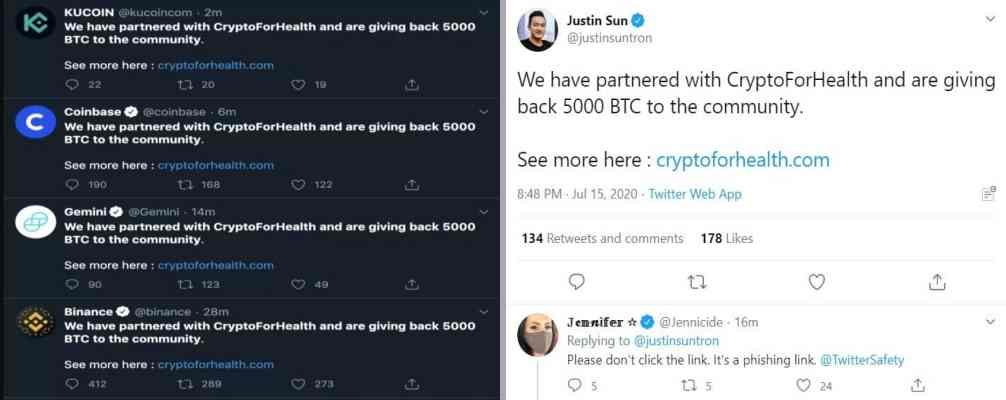
Earlier this month, we reported how Twitter accounts of celebrities, including Barack Obama, Kim Kardashian, Joe Biden, and Bill Gates, got hijacked by crypto scammers to launch a bitcoin scam. The scammers were able to rake in over £80,000/$100,000.
A more detailed analysis of the incident has revealed shocking new details about how the accounts were hacked at such a massive scale. Twitter posted this information in a blog post to confirm the cause of the incident:
“The social engineering that occurred on July 15, 2020, targeted a small number of employees through a phone spear-phishing attack. Using the credentials of employees with access to these tools, the attackers targeted 130 Twitter accounts, ultimately Tweeting from 45, accessing the DM inbox of 36, and downloading the Twitter Data of 7.”
Reportedly, a spear-phishing attack targeted against Twitter employees and humor errors were responsible for the mass hacking of major Twitter accounts, as the social networking giant itself has confirmed it.
The employees were targeted via their mobile phones. The attack allowed the scammers to post tweets from official, blue-ticked accounts of famous celebs as well as access their account’s direct messages section.
The entire incident highlighted how the company gives its employees extensive access to user accounts. The company has pledged to improve its permissions and processes to prevent similar events from occurring.
See: Apple co-founder Steve Wozniak sues YouTube over Bitcoin scams on his name
Twitter noted that just a small portion of its staff, who didn’t have access to its in-house support tools but could access its internal networks and systems, was targeted by attackers. After obtaining the credentials, the attackers could access Twitter’s internal network and executed the next stage of their plan, which involved targeting employees having access to account controls.
The company revealed that the attack, which started on July 16, was a well-planned hijacking campaign carried out by sophisticated scammers. Responding to claims that Twitter has given extensive access to its staff, the company stated that:
“Access to these tools is strictly limited and is only granted for valid business reasons. We have zero-tolerance for misuse of credentials or tools, actively monitor for misuse, regularly audit permissions, and take immediate action if anyone accesses account information without a valid business reason.”
The company claims to have “significantly limited” its employees’ access to its internal tools to ensure maximum security of user accounts. The investigation is still underway, and Twitter is continually investing in enhanced security protocols, mechanisms, and techniques.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.