Although, none of the databases contain LinkedIn users’ passwords; the data in the records is enough for cybercriminals to carry out a number of attacks including SIM Swapping, identity scams, phishing, and SMSishing, etc.
Just last week, a hacker leaked over 533 million Facebook users’ data that was collected from the social media giant using the web data scraping technique. Now, two different threat actors are selling LinkedIn data compiled as a result of data scraping as well.
It is worth noting that both databases are being sold on the same hacker forum. One of the sellers is offering 7 LinkedIn databases which, when merged together, makes 827 million users’ records. The price for all databases together is $7,000.
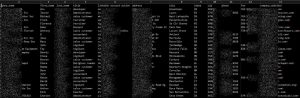
Hackread.com has seen sample data and after conducting an in-depth analysis it can be confirmed that the database with 827 million records includes the following:
- Job title
- Full names
- Company name
- Company website
- Email addresses
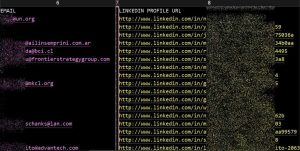
- LinkedIn profile links
- Job start date
- City
- State
- Country
- Zipcode
- Addresses
- Fax numbers
- Phone numbers
- Number of connections
Second LinkedIn database
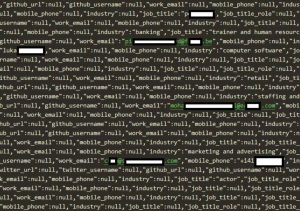
According to a sample dataset shared by CyberNews, the LinkedIn profile owners’ data leaked in this data breach includes:
- Usernames
- Full names
- Account IDs
- Email addresses
- Gender details
- Phone numbers
- Workplace information
- Social media account links.
Sample data
LinkedIn on the other hand has issued a statement addressing CyberNews’ report in which the company stated that private members’ data is safe, and its public members’ information is leaked as a result of data scraping.
“We have investigated an alleged set of LinkedIn data that has been posted for sale and have determined that it is actually an aggregation of data from a number of websites and companies,” LinkedIn’s statement read.
The company further claims that it is not a LinkedIn data breach. The dataset comprises publicly viewable information and also contains data from other companies/websites.
“We’re still investigating this issue…. Scraping our members’ data from LinkedIn violates our terms of service and we are constantly working to protect our members and their data.”
LinkedIn users watch out
Although, none of the databases contain users’ passwords; the data in the records is enough for cybercriminals to carry out a number of attacks including SIM Swapping, identity scams, phishing, and SMSishing, etc.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.

Como saber , se houve violação no meu LinkedIn? Aqui no Brasil?