According to researchers, 103 GB worth of data belonging to New Jersy based Descartes Aljex Software was left exposed on a misconfigured AWS S3 Bucket.
During their routine server scans for potential vulnerabilities, the Website Planet Team discovered that a US-based software company that focuses on delivering transportation management software for multinational freight brokers was affected by a data breach that exposed a total of 103 GB of data.
Yet another misconfigured AWS S3 Bucket
This affected more than 4,000 people including not only their own customers but also the company’s employees, sales reps, and people working for third-party carriers.
The data, which belonged to New Jersy based Descartes Aljex Software, was exposed by a misconfigured AWS S3 Bucket which left it unsecured and vulnerable to intrusion. This meant that even users with no authorization could potentially gain access to the Bucket only by entering the correct URL.
SEE: Software firm leaks 25GB worth of subscription & Ancestry.com user data
It is important to understand that this is a fault on the side of whoever owns or administrates the database and did not set up proper authentication procedures.
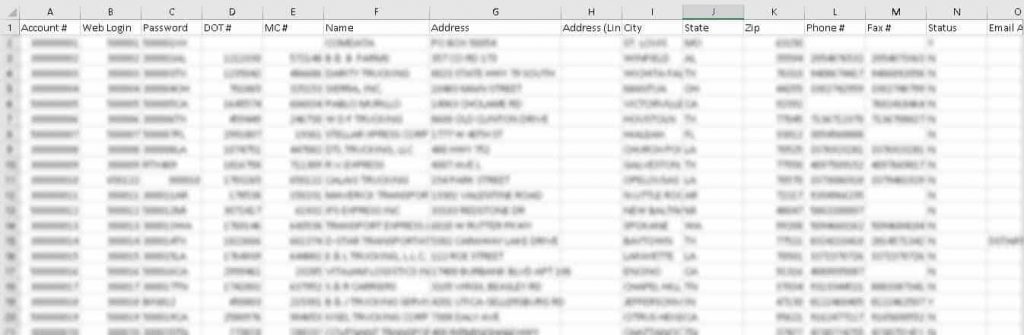
What data was exposed?
The impact on the customers was intense with a great load of Personal Identifying Information (PII) being exposed. When it came to the shipment details, shipment information, recipient’s consignee name, shipment origin and destination, addresses, and phone numbers were included in the data that was exposed.
Aljex clients’ account data that was exposed included full names, phone numbers, email addresses, Aljex usernames, and plaintext passwords. Carrier information, their full names and email addresses as well as their house addresses and phone numbers were compromised.
Lastly, Aljex clients’ sales representative details that were exposed included full names, corporate emails, Aljex usernames, and sales representative IDs.
Risks amid data breach
This data could be used by threat actors to assist in fraudulent identification across other platforms.
Additionally, phishing and malware scams could also be deployed via emails sent to people’s email addresses, including personalized “click-bait” to lure the target into clicking through to an unsecured website.
Rival businesses could migrate or target potential clients on Aljex’s user list as a form of corporate espionage and anti-competitive practices. Through leaked usernames and passwords, hackers could hijack the affected accounts and wreak severe damage to Aljex’s business operations which in turn could also affect their partners and carriers.
Data was secured upon reporting
According to Website Planet’s blog post, the breach was first detected on 24th December 2020 while Aljex was contacted by researchers six days later and Amazon Web Services (AWS) on 2nd January 2021 to inform them of their findings.
SEE: Marketing firm CallX exposed customers data including call recordings
Aljex claimed that the bucket did not belong to them and that they would “be making efforts to try to identify who this might relate to and let them know they have this open AWS S3 Bucket in their setup.” The bucket was secured a few hours later.
Did you enjoy reading this article? Don’t forget to like our page on Facebook and follow us on Twitter!