This chain of vulnerabilities is critical and has a cumulative CVSS score is 8.3/10.
Eclypsium security researchers have discovered four major security vulnerabilities in Dell SupportAssist’s BIOSConnect feature. In their report, researchers revealed that the bugs could allow attackers to carry out remote code execution within the BIOS of affected devices. The cumulative CVSS score given to the bugs was 8.3/10.
Researchers wrote that the flaws could be exploited to target the BIOS/UEFI level by impersonating Dell.com. The attacker can target around 129 models of Dell laptops, desktops, and tablets, including those having Secure Boot, enabled, or Secured-core PCs, and control the device’s boot process and undermine the OS level security controls.
Nearly 30 million Dell devices are vulnerable to exploitation.
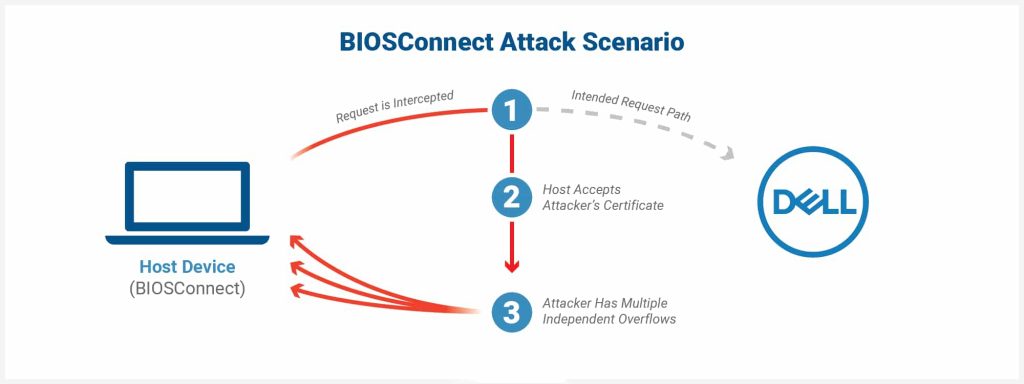
Attack Scenario
According to Eclypsium researchers, one bug leads to an insecure TLS connection from BIOS to Dell, whereas three are overflow vulnerabilities, classified as CVE-2021-21571, CVE-2021-21572, CVE-2021-21573, and CVE-2021-21574, respectively.
The first issue occurs when BIOSConnect connects to Dell’s back-end HTTP server. It accepts any valid wildcard certificate, letting an attacker deliver attacker-controlled content to the victim device under Dell’s guise.
Moreover, the researchers discovered HTTPS Boot configurations using the same verification code, which rendered them exploitable.
“When attempting to connect to the backend Dell HTTP server, the TLS connection from BIOSConnect will accept any valid wildcard certificate. This allows an attacker with a privileged network position to impersonate Dell and deliver attacker-controlled content back to the victim device,” says the report.
Regarding the three other independent vulnerabilities, which researchers described as overflow bugs, one impacts the OS recovery process, and the third was found in the firmware update mechanism. These vulnerabilities can allow a privileged network attacker to get arbitrary code execution within the machines’ BIOS.
The technical details of these bugs weren’t disclosed as the company stated it would reveal them at the upcoming DEFCON in August.
About SupportAssist
Dell states that the SupportAssist software comes preinstalled on a majority of Dell devices running Windows OS. The BIOSConnect feature facilitates remote firmware updates and OS recovery, troubleshooting features. To do so, it connects to Dell’s cloud infrastructure to get the requested quote transferred to the device.
Update BIOS Immediately
Dell has provided BIOS/UEFI updates for affected models. Eclypsium researchers wrote that users need to update their system to BIOS/UEFI and avoid using SupportAssist’s BIOSConnect feature until it is updated.
No additional action is required for CVE-2021-21573 and CVE-2021-21574 since the company already addressed them from the server side in May 2021. For CVE-2021-21571 and CVE-2021-21572, updating the system is mandatory.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.