Browsing Category
NSA
67 posts
Download NSA’s reverse engineering tool GHIDRA
Recently we informed that the National Security Agency’s (NSA) plans to release GHIDRA, the famous reverse engineering tool…
March 6, 2019
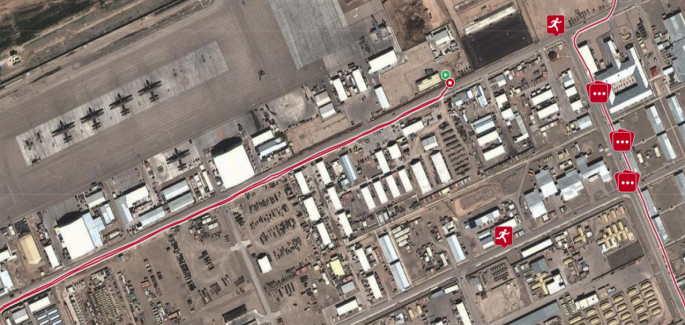
Polar fitness app exposed location data of users in military & airbases
Polar Flow, an app developed by Polar, a Finland based sports gadgets manufacture has been found exposing personal and…
July 9, 2018
Fileless WannaMine Cryptojacking Malware Using NSA Exploit
Forget WannaCry and welcome WannaMine, a fileless cryptojacking malware using leaked NSA exploit called EternalBlue. We cannot ignore the…
February 2, 2018
New Cryptocurrency Mining Scheme Uses NSA Exploits EternalBlue & EternalSynergy
Due to the unprecedented and unexpected increase in the value of cryptocurrencies like Bitcoin, there has been a…
December 20, 2017
Unprotected S3 Cloud Bucket Exposed 100GB of Classified NSA Data
Another day another massive trove of sensitive NSA data exposed online – This time, security firm UpGuard’s Cyber…
November 29, 2017
Kaspersky Investigators Reveal How NSA Hacking Tools Were Stolen
In its latest report, Kaspersky Lab revealed the findings of its internal investigation, which was launched to dispel…
November 17, 2017
NSA rocked after The Shadow Brokers Breach
National Security Agency or the NSA as we know it is America’s most influential intelligence agency. Previously fairly anonymous…
November 14, 2017
Israel hacked Kaspersky to inform US about Russia stealing NSA exploits
Israeli Spies Hacked Kaspersky and Found Russian Hackers Exploiting the Antivirus software to Obtain US Intelligence Secrets. We…
October 11, 2017
Report Claims Russia Stole NSA Tools Using Kaspersky Software
The Wall Street Journal has reported that Russian government-sponsored hackers have managed to steal extremely sensitive information about…
October 6, 2017
New NSA Data Dump: ShadowBrokers Release UNITEDRAKE Malware
The ShadowBrokers is a group of hackers known for leaking exclusive information about the National Security Agency –…
September 7, 2017