While the Cloud offers an excellent chance for organizations to host their web services online, it comes with its fair share of disadvantages as well.
In the latest, it has been found by researchers at cybersecurity firm Intezer that a malicious group named TeamTNT is using a third-party tool named Weave Scope to attack 4 cloud-based platforms, namely Docker, Kubernetes, Distributed Cloud Operating System(DCOS), and AWS Elastic Compute Cloud (ECS).
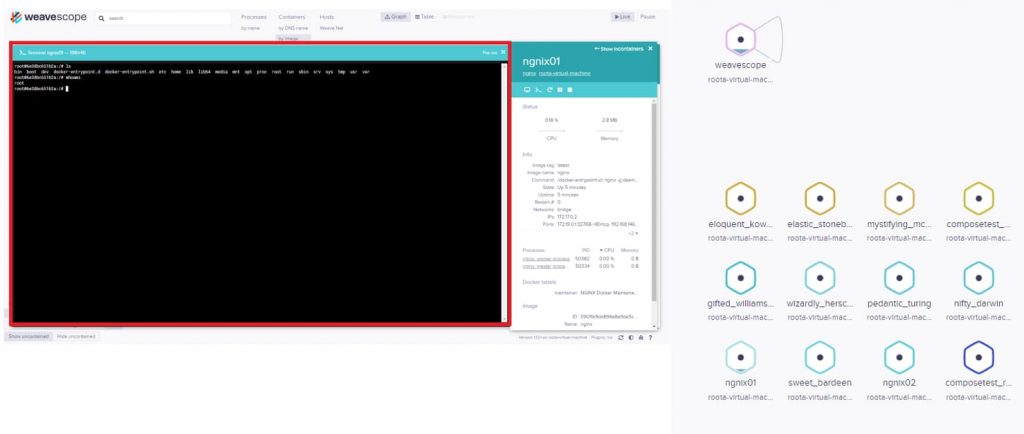
To understand how they do this, you need to know that Weave Scope allows users to view their cloud applications including hosts, services, processes, and much more in real-time.
Furthermore, it allows one to control them with the help of a command line as well. Therefore, to gain access to the user’s cloud-based assets, the attackers simply install this tool making it do everything for them automatically.
Describing the installation process, the researchers state in their blog post that,
To install Weave Scope on the server the attackers use an exposed Docker API port and create a new privileged container with a clean Ubuntu image. The container is configured to mount the file system of the container to the filesystem of the victim server, thus gaining the attackers access to all files on the server. The initial command given to the container is to download and execute several cryptominers.
The attackers then attempt to gain root access to the server by setting up a local privileged user named ‘hilde’ on the host server and use it in order to connect back via SSH.
Once this is done, the tool is simply downloaded and installed with the help of a few commands opening up access to its backend for the attackers through Port 4040 by using HTTP.
The motive behind the attack seems to be centered around earning money via cryptocurrencies. This is evident from the fact that the very first command that is executed after the attackers gain access is to install crypto miners consistent with its history of cyberattacks.
To conclude, in order to be safe, users should not only make sure that unused ports are closed but also “block incoming connections to port 4040” as it is used to ultimately gain access to Weave Scope.
Additionally, it is best to hire professionals to secure your cloud-based infrastructure as a simple mistake can cost you your security.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.