Cybersecurity researchers are confident that the targeted organizations are “still compromised” by “two prominent Chinese APT” groups.
Palo Alto Networks’ Unit 42 cybersecurity researchers have discovered that Chinese APT groups could be involved in a long-term espionage campaign against Cambodian government organizations using infrastructure masqueraded as cloud backup services.
According to the Unit 42 report, researchers noted network connections—specifically inbound connections—primarily originating from 24 Cambodian government organizations.
The researchers also believe that these organizations are ‘still compromised’ by ‘two prominent Chinese APT’ actors due to the infrastructure’s characteristics and the enduring persistence of these connections over several months.
It is worth noting that the certainty about the involvement of two Chinese APT groups stemmed from monitoring telemetry data, which established a clear link with these groups.
“We assess that these organizations are likely the targets of long-term cyberespionage activities that have leveraged this infrastructure for persistent access to government networks of interest,” said the Santa Clara, California-based cybersecurity giant.
These organizations were communicating regularly with the infrastructure between September and October 2023. Many of these organizations provided critical services to the following industries.
- Politics
- Commerce
- Human rights
- National defense
- Election oversight
- Natural resources
- Telecommunications
- National treasury and finance
The research emerged just days after Canada banned the Chinese WeChat app from all government devices due to spying concerns, prompting employees to promptly uninstall the application.
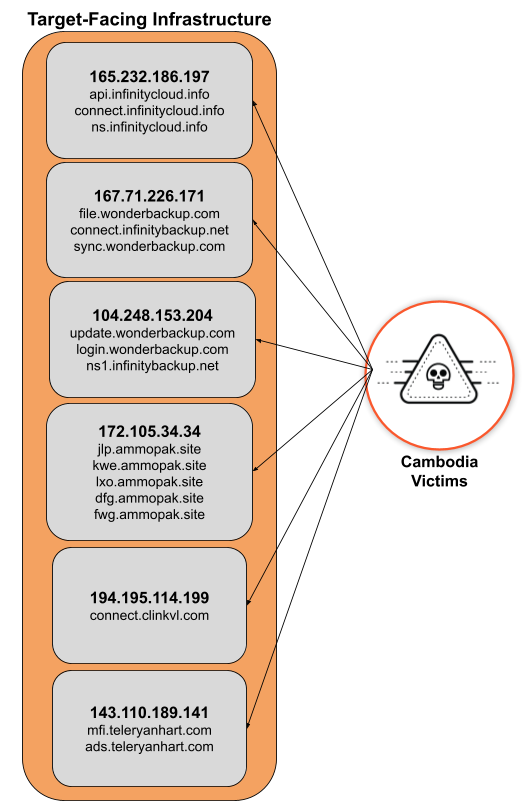
Researchers noted that organizations in these sectors could be targets of interest because of storing vast amounts of sensitive information, including financial data, classified government data, and PII (personally identifiable information) of citizens. They discovered at least six target-facing IP addresses used in the campaign, each hosting numerous subdomains.
These domains were masqueraded as cloud storage services, which is the perfect alibi to create a sense of legitimacy to the unusually high traffic the server may observe during “high activity levels from the actor, such as data exfiltration from the victim network,” researchers wrote in their blog post.
Moreover, they had “high confidence” that these IP addresses served as the C2 infrastructure for the actor, and running the Cowrie honeypot on port 2222. Most likely, this honeypot was a cover to trick network defenders and security researchers investigating the “anomalous activity.”
In addition, they observed IP filtering on this infrastructure. It was used for blocking connections from IP ranges from known Palo Alto Networks several Big Tech and cybersecurity firms, and a number of VPS and cloud hosting providers.
These C2 ports open only when the actor is active (between 08:30 and 17:30 UTC +08:00 (China Standard Time) on weekdays (Monday to Friday)) and remain closed otherwise. This means the actor is filtering connections to the malicious infrastructure to reduce the risk of C2 profiling by IP scanners or to evade detection.
“This pattern might indicate the actor is attempting to avoid detection by blending into regular Cambodian business hours which are UTC +07:00.”
However, between September 29-October 8 2023, during China’s Golden Week and Special Working Days, the APT actors ceased their activity. This suggests that the attackers are based in China and following the country’s regular working hours, thus, validating Unit 42’s assessment regarding the attackers.
It is worth noting that Cambodia is among the signatories of the Chinese Belt and Road Initiative. The countries share strong economic and diplomatic relations. China has made significantly high investments to modernize Cambodia’s Ream Naval Base, despite that the project sparked concerns within the West. After completion, this base will become China’s first overseas outpost in Southeast Asia. This indicates that Cambodia is an important ally of China.
RELATED ARTICLES
- Who Killed the IoT Zombie Mozi Botnet – China or India?
- Chinese Scammers Use Fake Loan Apps for Money Laundering
- Chinese Silent Skimmer Attack Hits Businesses in APAC and NALA regions
- Chinese Hackers Stole 60,000 US State Department Emails from Microsoft
- Chinese Smishing Triad Gang Hits US Users in Extensive Cybercrime Attack
- Chinese Hackers Stole Microsoft’s Signing Key to Breach Outlook Accounts