Unsecured Implementation of UDP Protocol Put Memcached Servers at Risk of DDoS Attacks.
According to the findings of popular content delivery network/CDN specialists Cloudflare, Akamai and security provider firm Arbor Networks, the implementation of the Memcached servers’ UDP protocol is flawed and anyone can launch a major Distributed Denial of Service (DD0S) attack without much ado.
This means, cybercriminals have managed to add a brand new and extremely effective technique to their already loaded cyber-weaponry that can twofold DDoS attacks by as much as 51 x 200x through exploiting misconfigured Memcached servers, which are easily accessible through the public internet connection.
Memcached servers are web-based memory caches that are quite huge and are used to boost the responsiveness of database driven websites as it can improve their memory caching system. These servers cache the data that is most frequently retrieved and stores it in its memory instead of retrieving it from the hard disk again and again. Memcache servers are a combo of open-source software as well as standard server hardware and just contain huge reserves of memory.
The findings were reported by the three CDN specialists on Tuesday and all have observed a sudden increment in DDoS attacks that are launched via User Datagram Protocol (UDP) packets. These packets were noticed to be amplified by Memcached servers over the last two days.
As per their findings , Memcached developers did not follow appropriate security measures while implementing support for the UDP protocol, which is why various DDoS attacks have been carried out through exposed servers lately.
Cloudflare engineer Marek Majkowski provided a technical explanation of the DDoS attacks in a blog post: “Over the last couple of days, we’ve seen a big increase in an obscure amplification attack vector — using the Memcached protocol, coming from UDP port 11211. Unfortunately, there are many Memcached deployments worldwide which have been deployed using the default insecure configuration.”
Akamai SIRT Alert stated in its post that it is not easy to determine the exact amplification factor of Memcached servers; however, Akamai noted that around 1Gbps per reflector was generated while other firms reported about 500 Gbps attacks using Memcached reflection.
Due to the inappropriate implementation of UDP protocol, hackers can easily send a byte-sized request to any exposed Memcached server, which will not respond with a similar tiny size packet but with thousand times bigger packets. If cybercriminals manage to prepare the attack well, they can launch an attack with lowest possible IP spoofing capacity, as low as 1Gbps, and successfully launch very large attacks that can reach up to hundreds of gigabits per second.
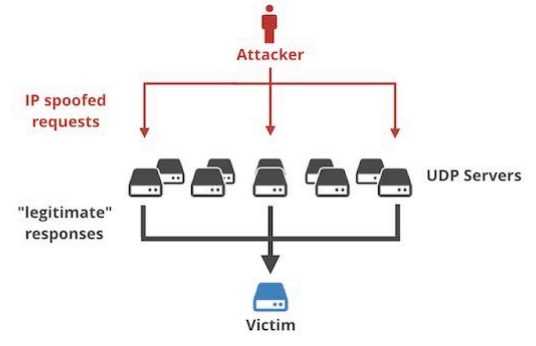
According to Cloudflare researchers, it is evident from the UDP protocol specification that “it’s one of the best protocols to use for amplification ever! There are absolutely zero checks, and the data WILL be delivered to the client, with blazing speed! Furthermore, the request can be tiny and the response huge.”
Cloudflare also reported about a recent DDoS attack that was launched against Cloudflare and attackers sent 15-byte packets which were responded to by Memcached servers with 750KB packets. Since the UDP protocol doesn’t need a source address in its header, therefore, the original IP address of the packets can be spooked very conveniently and cybercriminals can trick the Memcached server into sending larger response packets to the targeted IP address.
Furthermore, in their default configuration Memcached servers can expose their UDP port to external connections, which means the server without a firewall is an open gateway for abuse via DDoS. It is estimated that there are more than 88,000 misconfigured Memcached servers currently at risk of abuse and most of these servers are located in North America and Europe.
The problem can be fixed easily as well; Cloudflare reports that Memcached server users need to disable their UDP port and augment the servers’ security by putting them on firewalls and place them on private networks.
