A few months ago, United States General Vincent Brooks warned the Senate about the growing threat from North Korean cyber-attacks, saying, “While I would not characterize them as the best in the world, they are among the best in the world, and the best organized.”

In the past, the hermit kingdom has been called one of the “least network-ready and most isolated societies on the planet,” but now, it may actually be one of the biggest threats to international cyber security.
The country of 25 million people is still technically fighting the civil war that started more than 60 years ago. The regime has been imposed with heavy sanctions, and they do not provide an economy that allows most citizens to obtain the basic necessities to live. Reports say that electricity is sparse, and only lasts a few hours a day. The effect of this is obvious in NASA’s pictures of the country at night, where North Korea appears as the only dark land mass in the region.
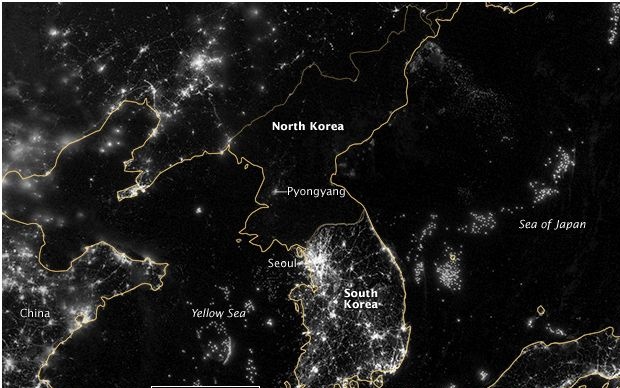
Even the few privileged citizens who can afford consistent electricity and a computer, are forbidden from accessing the Internet. Only tourists and citizens with permission can access the internet, everyone else needs to use the “Kwangmyong” Intranet, which is completely controlled and monitored by the state.
According to Jean H. Lee, the Associated Press bureau chief in Pyongyang, citizens are only allowed to have “access to the state media, information sources that are vetted by the government, and picked and pulled from the Internet and posted to their intranet site.”
So, it seems unlikely that North Korea, a country that can barely feed its own people, could be a threat to the most technologically advanced countries in the world. However as the U.S. Office of the National Counterintelligence has asserted, “development of the nation, rather than empowerment of the individual, appears to be driving DPRK efforts to develop domestic IT infrastructure and industry.”
It is estimated that North Korea spends one-third of its total revenues on its military, and around 10% to 20% that is spent on the IT divisions.
What is Bureau 121
One of the most important divisions of the DPRK’s militarized IT infrastructure is called Unit 121, an elite group of highly trained hackers, who are solely focused on cyber espionage and cyber crime. This unit is made up of the best and brightest minds, who have been handpicked from a very early age by the military to be trained in cyber warfare.

These select units are rewarded with some of the most privileged lives in the country. Professor Kim Heung-Kwang taught computer science in DPRK for 20 years before defecting in 2004, says, “it is a great honor for them. It is a white-collar job there and people have fantasies about it.” They are the only citizens that are allowed to access the Internet or leave the country.
Since they are cut off from the rest of the world, it is impossible to know just how big these divisions are growing, but South Korea claims that Unit 121 is now world’s third largest cyber unit (right behind the US and Russia). South Korea has taken the threat very seriously and is in the process of training 5,000 people to their own cyber army to defend against the attacks from Unit 121.
How North Korea started in Cyber Warfare
The first known cyber-attacks originating from North Korea started in the early 2000’s. At first, they wiped disks, spread malware attacks, and performed DDoS attacks, but quickly, they are learning how to breach more significant networks.
In 2013, the DPRK targeted South Korean media and financial institutions and knocked out 50,000 computers and servers in South Korea for several days at five banks and television broadcasters.
In 2014, they were able to target hydroelectric plants and nuclear power plants with a Stuxnet-style attack—an attack that can bring down power grids and other critical control systems and infrastructures. Professor Kim Heung-Kwang claims that these types of attacks could be catastrophic, “Although the nuclear plant was not compromised by the attack, if the computer system controlling the nuclear reactor was compromised, the consequences could be unimaginably severe and cause extensive casualties.”
What Really Happened with Sony?
Perhaps their most famous cyber-attack from North Korea was when they targeted Sony Pictures, before the release of “The Interview,” a film about two reporters (Seth Rogen and James Franco) who travel to North Korea to assassinate Kim-Jong Un.
The premise angered Korean officials so much, and they immediately condemned the film as, “the most undisguised terrorism and a war action to deprive the service personnel and people of the DPRK of their mental mainstay and bring down its social system.”
In retaliation, a team called the Guardians of Peace (GOP) breached the systems of Sony Pictures and stole large amounts of sensitive documents and information, which they posted online. Then, they made threats to the theaters that planned to show the film, warning, “we will clearly show it to you at the very time and places ‘The Interview’ be shown, including the premiere, how bitter fate those who seek fun in terror should be doomed to” and “Remember the 11th of September 2001.”
Under pressure, Sony decided not to release the film for several months.

There was a lot of doubt that North Korea was behind the attacks. Most likely, people thought that North Korea was not capable of such advanced infiltration. But, the evidence is fairly undeniable.
Director of the FBI, James Comey quickly cleared those doubts up when he said, “We could see that the IP addresses they used … were IPs that were exclusively used by the North Koreans. It was a mistake by them. It was a very clear indication of who was doing this. They would shut it off very quickly once they realized the mistake, but not before we saw them and knew where it was coming from.”
Since those IP addresses are only used in North Korea, and the citizens are not allowed to use them, it is obvious that the attacks were state-sponsored.
President Obama immediately accused North Korea of the attacks, saying, “I’m, for the first time, authorizing targeted sanctions against individuals or entities whose actions in cyberspace result in significant threats to the national security, foreign policy, or economic health or financial stability of the United States.”
This was unprecedented in US history, as no president had ever explicitly accused another country of mounting a cyberattack against the United States. However, it further substantiates the idea that North Korea was behind the attacks, as the Snowden leaks revealed that the US had been implanting “beacons” in several countries, which could pinpoint where an attack was coming from.
How North Korea is Attacking Now
Earlier this year, North Korean hackers attempted to steal nearly $1 billion dollars from the Bangladesh central bank. The hackers were thwarted from stealing it all by a few suspicious bankers in New York. However, they did manage to abscond with $81 Million dollars.
The bank was protected by the cyber security firm Swift network, which protects more than 11,000 banks and financial institutions, and handles as much $5 trillion daily. The cyber security company was previously thought to be secure from attacks, but as Eric Chien, the director of security response at Symantec said of North Korean hackers, “They’re showing skills that we haven’t seen before.”
Then, only a month ago, South Korean police reported that more than 140,000 computers from South Korean firms and government agencies, were hacked by North Korea. They also discovered malicious code was planted for a massive cyber-attack in the future.
This hack was started back in 2014, and they were only detected after they tried to steal defense-related material. North Korea was successful in obtaining more than 42,000 documents, 40,000 of which were defense-related. This included some blueprints for F-15 fighter jets.
What Will Future Attacks Look Like?
North Korea needs to be considered one of the greatest threats to our way of cyber life in the modern world. On the flip side, because of its isolation, the hermit kingdom is so isolated from everything, that it is virtually hack-proof, thereby confounding anybody bent on retaliation.
Now, cyber operations have become an extension of their international strategy. As Kim Jong-Un allegedly said, “Cyber warfare, along with nuclear weapons and missiles, is an ‘all-purpose sword that guarantees our military’s capability to strike relentlessly.”
Stephan/Flickr