One of the biggest cyber attacks in Europe has been identified by the researchers. All this started in 2007 according to the researchers and attacked many leading infrastructural websites of the country which included: embassies, oil and gas institutes and nuclear station. The way of attack was the same i.e. by sending malware in the system. The malware attacked the encrypted and deleted files in the system. The deleted files were restored by the malwares themselves. One of the IT experts described this particular attack as ‘insignificant’ and said: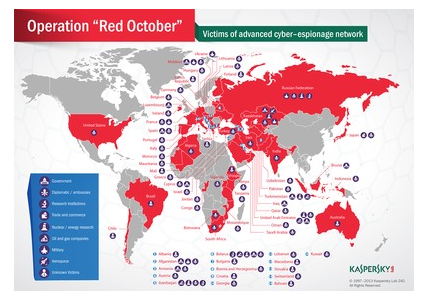
“It appears to be trying to suck up all the usual things – word documents, PDFs, all the things you’d expect,” said Prof Alan Woodward, from the University of Surrey.
“But a couple of the file extensions it’s going after are very specific encrypted files.”
The main target of this attack was to get sensitive information from all around Europe the researcher while giving briefing regarding the path of the attacks said:
“The primary focus of this campaign targets countries in Eastern Europe, former USSR Republics, and countries in Central Asia, although victims can be found everywhere, including Western Europe and North America.
“The main objective of the attackers was to gather sensitive documents from the compromised organizations, which included geopolitical intelligence, credentials to access classified computer systems, and data from personal mobile devices and network equipment.”
Furthermore, the chief malware researchers gave light to some salient features of this malware and were quite interesting:
“It was discovered in October last year, “We initiated our checks and quite quickly understood that is this massive cyber-attack campaign.
“There were a quite limited set of targets that were affected – they were carefully selected. They seem to be related to some high-profile organizations.”
These cyber attacks are named as Red October which is linked to a novel of same name. The novel is about some high-profile attacks under-water, which relates to disastrous malware attacks on the system. Each module of this particular attacks has been defined its own function. While telling about one of the special modules the malware expert said:
“There is a special module for recovering deleted files from USB sticks,”
“It monitors when a USB stick is plugged in, and it will try to undelete files. We haven’t seen anything like that in a malware before.”
One of the salient features of these attacks is explained by a professor in these words:
“Also unique to Red October was its ability to hide on a machine as if deleted”
“If it’s discovered, it hides.
“When everyone thinks the coast is clear, you just send an email and ‘boof’ it’s back and active again.”
Other modules of the malware are used to pick out the encrypted files from the system; this system in the malware is known as “Cryptofiler”. Though, this system, nowadays, is not in use only NATO uses this system for keeping privacy to some sensitive information.
Like other attacks, in this particular attack too the attackers haven’t left behind any clue regarding the malwares, some clues have been found by the researchers but they are thought to be disguising. Regarding the clues Kaspersky’s Mr Kamluk said:
“We’ve seen use of the word ‘proga’ – a slang word common among Russians which means program or application. It’s not used in any other language as far as we know.”
Prof Woodward added to it: “In the sneaky old world of espionage, it could be a false flag exercise. You can’t take those things at face value.”
During a test check of this malware 55000 target connected targets were found in the enclosed area, which means a large number of systems were affected due to these hacks. A detailed report regarding these attacks would be published later.
