Hackers hijacked subdomains of major brands like eBay and CBS to send spam emails disguised as legitimate messages – Learn how to protect yourself from these deceptive phishing attempts.
Guardio Labs is monitoring a campaign called SubdoMailing, which has been circulating spam and phishing emails since September 2022. The campaign, attributed to a threat actor called ResurrecAds, manipulates the digital advertising ecosystem by resuscitating dead domains associated with big brands – A malicious practice also known as Brand Hijacking.
The scam was detected after Guardio Labs’ email protection systems discovered unusual patterns in email metadata mainly related to SMTP servers that are authenticated as legitimate senders. This led Guardio to launch an investigation into the SMTP protocol, domain hunting, and DNS scanning tools.
The ResurrecAds incident mirrors a prior case where, in November 2022, cybersecurity researchers at Cyjax uncovered 42,000 phishing domains posing as well-known brands, distributing malware for ad revenue.
The team discovered an unprecedented subdomain hijacking operation, where thousands of hijacked sub-domains were used to send spammy and malicious emails, falsely authorized under international brands. The campaign uses the trust in these domains to circulate spam and phishing emails, bypassing security measures.
The emails can also circumvent the Sender Policy Framework (SPF), an email authentication method, and pass DomainKeys Identified Mail (DKIM) and Domain-based Message Authentication, Reporting and Conformance (DMARC) checks to prevent messages from being marked as spam.
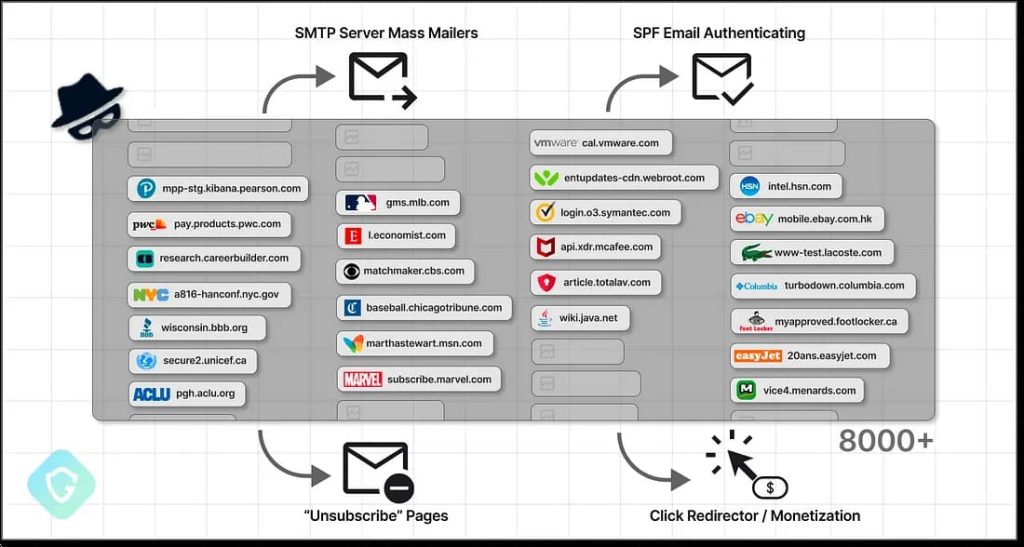
Guardio researchers discovered over 8,000 domains from renowned brands/institutions (MSN, VMware, McAfee, The Economist, Cornell University, CBS, Marvel, eBay). Researchers dubbed this activity “SubdoMailing,” which exploits users’ trust to circulate spammy phishing emails.
They called it a classic subdomain hijacking scheme because it involves scanning and enumerating domains for forgotten subdomains, registering them, and using SPF records to send malicious emails. This can lead to unauthorized access to SMTP servers and valuable assets for hackers.
The sample email researchers analyzed was disguised as an image to bypass spam filters, trigger click-redirects through various domains, targeting device type and location to display content tailored to maximize profit. This unique scheme raises questions about how it bypasses authentication and security checks with major email providers.
The evidence suggests a single threat actor, “ResurrecAds,” is responsible for a large-scale operation scanning the internet for “vulnerable domains, identifying opportunities, purchasing domains, securing hosts and IP addresses, and orchestrating email dissemination,” researchers noted.
Their strategy involves reviving domains affiliated with big brands, exploiting legitimate services and brands, and circumventing email protection measures, demonstrating their sophisticated technical sophistication.
The study revealed thousands of active cases of CNAME-takeover and SPF-takeover, which involve stealing abandoned domains of old email/marketing services. These attacks have been ongoing for at least two years, allowing attackers to easily inject their IPs into the domain’s SPF records using the main domain name as the sender.
“Given these sophisticated tactics, we’re clearly facing a formidable operation characterized by significant expenditure and substantial revenue.”
Researchers have launched a “SubdoMailing” checker website, enabling domain administrators and site owners to quickly identify and address any abuse detected, ensuring domain security.