It’s a decision tree that’s all about you (and your company). That’s a bit of an oversimplification, but the idea behind a Stakeholder-Specific Vulnerability Categorization (SSVC) is that you should prioritize addressing your vulnerabilities in a way that benefits you and your organization.
Once you’ve prioritized, there are things you can do to mitigate the risk from your most critical vulnerabilities. A WAF solution is one option, or you might consider other types of virtual patching to reduce your risk.
Why Categorize Vulnerabilities
If your company is like most, it faces overwhelming numbers of vulnerabilities from many different aspects. From human error to backdoors in open-source code embedded in your web apps, there’s no telling when you’ll be attacked or where the attack will come from. Unless you categorize.
Categorizing enables you to differentiate between low-risk vulnerabilities and critical threats. If you want to know which threat to neutralize first, categorization can help you sort that out. Many vulnerabilities don’t pose a threat or perhaps pose no immediate threat.
On the other hand, some of your weaknesses are highly susceptible to exploitation, and you need to remedy that as soon as possible.
It’s best to focus your limited resources on addressing threats that are likely to create a problem. Among other things, this might mean it’s easy or practical for an attacker to exploit them, it’s financially rewarding for an attacker (and thus devastating to your company), or your company can be used as a vector for a supply chain attack.
However, if you have vulnerabilities that are highly impractical to exploit, for example, this might be a lower risk to you, and so it can wait to be patched until you’ve addressed more critical issues.
What is SSVC?
Aside from being a way to categorize that is tailored to your company, SSVC originated as a way for government agencies and critical infrastructure organizations to assess their cybersecurity weaknesses, and it is now an effective way for private companies to do the same.
CISA’s executive assistant director Eric Goldstein explains that this methodology was designed to assess vulnerabilities, and it prioritizes remediation according to the status of exploitation, as well as the safety impacts and pervasiveness of the product within a singular system.
A singular system refers to the individual company (stakeholder), and the goal is to prioritize finding the vulnerabilities for that system rather than following a more general risk assessment’s recommendations. The newest guidelines focus on managing the number and complexity of vulnerabilities.
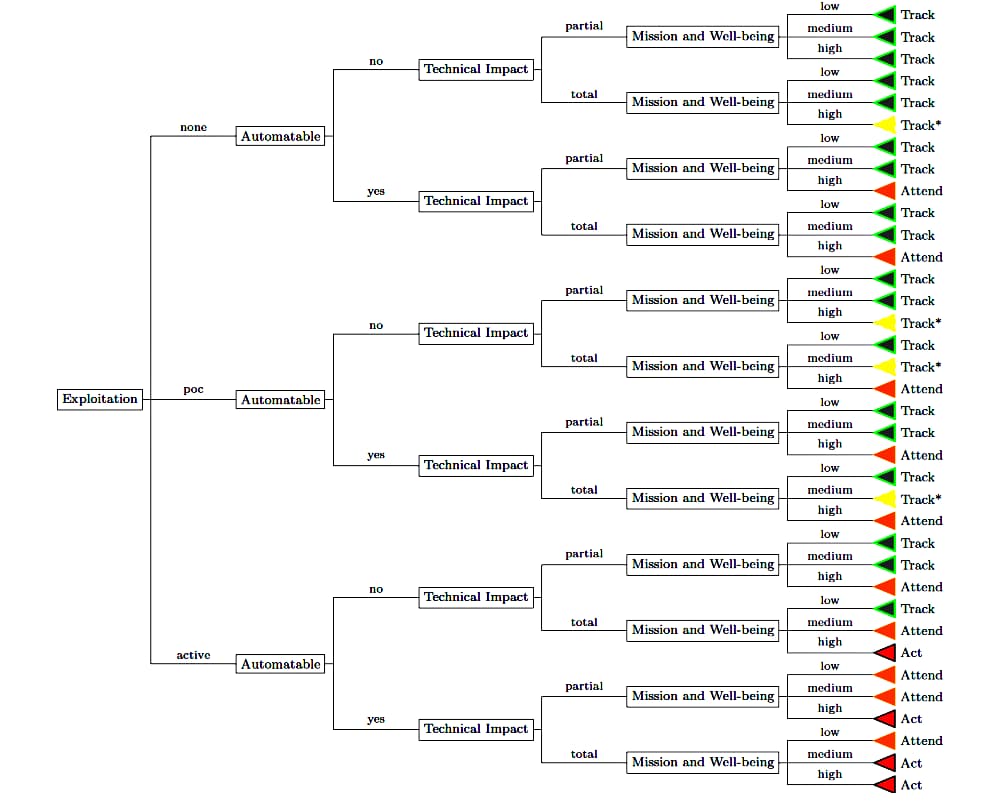
Here’s a summary of how the SSVC decision tree works, but to sum up – here are 4 possible decisions for each vulnerability:
- Track: Keep an eye on the vulnerability, but it doesn’t require immediate action.
- Track*: Monitor the vulnerability. Immediate action is not required, but you should find a fix by the time the next update rolls out.
- Attend: Supervisors need to pay attention to this vulnerability. They may need to seek help or information regarding the vulnerability. Depending on the severity, they may need to notify employees or consumers. This should be fixed before the next standard update.
- Act: Leadership must get help and information. They should notify employees and consumers regarding the vulnerability and create a response plan. This level of vulnerability must be fixed as quickly as possible.
To decide how to label each vulnerability, consider 5 factors:
- Exploitation status: Is the vulnerability currently being exploited?
- Technical impact: Would malicious actors be able to acquire credentials by exploiting this vulnerability? How much access would they have to the rest of the system?
- Automatability: How easy is it for an attacker to repeatedly exploit this vulnerability? Could the exploit be automated?
- Mission prevalence: Would an exploit of this vulnerability have an adverse and significant effect on your business operations? How much downtime would it cause you? How much money would you lose if consumers can’t access your products or services through your web app?
- Public well-being impact: Will an exploit cause physical, mental, emotional, or environmental harm? How will the public be affected adversely if an attack occurs? Will there be a financial loss for your consumers, or will you break compliance regulations?
If these factors are significant in a particular vulnerability, you should prioritize that vulnerability.
Prioritized Risk and Vulnerability Management
Once you’ve gone through the SSVC, you should have a pretty good idea of where to start patching. The remaining question, then, is how you should patch efficiently and effectively. If there is a major code issue, that should be updated as soon as possible. For less urgent, more difficult fixes, there are ways to help protect your system from external threats.
Virtual patching is often a good way to reduce the risk of lower-level threats or to get protection quickly while you take some time to address the code problems. A web app firewall (WAF) or a Web Application and API Protection (WAAP) protocol protect web apps from attack by securing data and filtering traffic.
You could use a cloud-based or a SaaS solution, depending on your company’s needs. Although this approach will not fix the vulnerabilities in your system, it can help keep attackers at bay.
Whatever method you choose, virtual patching can go a long way toward keeping your data safe while you sort out your vulnerabilities. Once you’ve prioritized those vulnerabilities with SSVC, you can begin to implement fixes first for the Act category, then for Attend, then for Track*, and finally for Track.
Organizing your resources this way will give you the best chance of fixing the most important issues while still protecting the less critical vulnerabilities.
