
Today over at Resonance Security I am going to look at one of the more unusual ways in which your approach to computer security can lead to an increase in public awareness of your company.
There are many motivations for starting a company: becoming wealthy, doing something interesting and useful, and leaving some kind of legacy or mark on history are three of the main ones that spring to mind.
About that legacy: imagine having the name of your corporation attached to a file representing one of the most significant hacks of the 21st century!
That’s quite notable, but probably not what the founders of one particular company were looking for with their startup.
We won’t rock you
In the middle of the 2000s, RockYou, Inc. was doing well as a widget-maker for social media companies like MySpace and Facebook. However, back in 2009, it suffered a data breach in which a hacker discovered an SQL database server with an unpatched ten-year-old bug, the database containing over 32 million usernames and passwords for user accounts.
That’s right — 32 million usernames, and their associated passwords. For comparison, that’s about 10% of the active monthly users that Facebook had at the time.
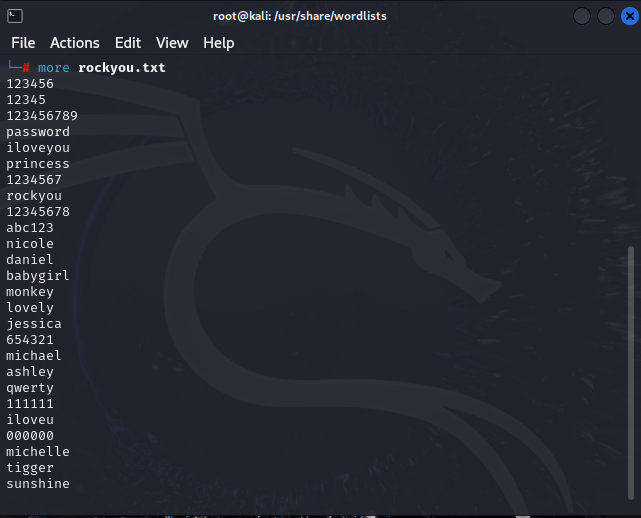
The passwords were stored in plain text.
Mud on your face, big disgrace
Not only did RockYou initially fail to notify their users, but it subsequently released a falsified official statement claiming that the breach was less severe than it was.
To be clear: it was a very, very serious breach.
A decade and a half ago, people were far worse at password security than they are now. Password managers were almost unheard of, for some unexplained bizarre reason some sites blocked the use of password managers for unspecified “security reasons”, and two-factor authentication was pretty much only affordable and available to business users.
Because people were told not to write down their passwords, this meant that most of the leaked credentials were being used on other websites. After all, who in their right mind is going to memorize twenty or thirty different random passwords? As a result, sites such as banks, online stores, health databases, social media, supposedly private online journals, and online games held accounts using the same passwords.
The legacy
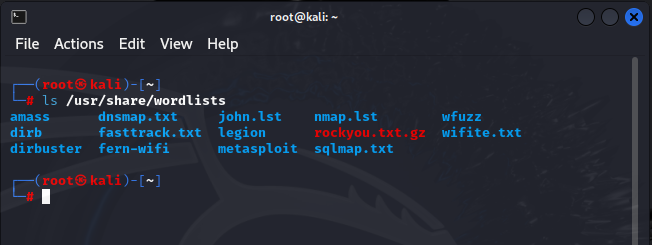
For years the full list of RockYou passwords has been available to download by anyone. It is typically found in a file called rockyou.txt , and there are plenty of GitHub repositories out there where you can find it.
In Kali Linux, a Linux distribution designed and produced specifically for penetration testing, the RockYou text file is included during the installation by default.
Conclusion
Just imagine — with a little bit of security carelessness, you too can take your modestly successful company and in the process of destroying it, allow its name to live on forever.
Have we learned anything since 2009? Not always.
For example: in 2017 it was revealed that an old social media site called LiveJournal, dating back to the 90s (but still running to this day), suffered a breach in which 26 million unique usernames, email addresses, and plaintext passwords were extracted. It took them until 2019 to admit to the breach.
That’s right — passwords were still being stored in plaintext in 2017, and I would bet good money on there being more sites out are doing the same, even though we are a decade and a half on from the original RockYou breach.
I predict that the leakage of passwords will only end once we stop using passwords, and start using improved systems such as security keys and self-managed identity for our authentication systems.
In the meantime, you have to assume that any password you provide to a website will eventually be leaked, therefore:
- use a password manager to generate long, random, unique passwords for your accounts,
- protect access to the password manager with two-factor authentication, and
- make sure the password you use for your password manager has never been used anywhere else.
Post-script
Don’t run off and look for a website that allows you to enter your password and see if it was ever revealed in a breach! I can guarantee it will be a phishing site. Instead, I recommend HaveIBeenPwned, where you can type in your email address, and retrieve a list of the companies and websites that have managed to leak your credentials to the dark web through bad security practices. Another option is the Resonance Data Leak Detector, which monitors if your credentials have been leaked 24/7 and automatically notifies you.
About Resonance Security
Resonance Security is a curated platform for end-to-end cybersecurity products and services. It functions as a concierge for your organization’s end-to-end cyber-security needs, aggregating valuable security offerings into one platform to spread awareness on what it takes to secure your technology stack end-to-end.
I’m Keir Finlow-Bates, often known as Blockchain Gandalf, and am primarily a blockchain researcher and inventor. I started on this journey in late 2010 by examining the original Bitcoin code, and have been obsessed with blockchain ever since.
I am also the author of two books on the topic: Move Over Brokers Here Comes The Blockchain, explaining blockchain, and Evil Tokenomics, illustrating through practical examples how web3 scams work. You can find more at my website: Thinklair.com

