According to researchers, cybercriminals are abusing legitimate challenge and response services like Google’s reCAPTCHA or deploying customized fake CAPTCHA-like validation.
Palo Alto Networks’ Unit 42 researchers have published a detailed report on how cybercriminals exploit CAPTCHA features including Google’s I Am Not A Robot Function dubbed reCAPTCHA to carry out their scams against unsuspected users.
These threat actors are launching all kinds of cyberattacks through fake CAPTCHA-like services, including phishing campaigns. If you are unaware of CAPTCHAs, these are challenges usually displayed before accessing websites to confirm that the user is a human and not a bot.
SEE: Android banking malware distributed with fake Google reCAPTCHA
According to the blog post, numerous malicious campaigns have been identified that abuse legitimate challenge-and-response services like reCAPTCHA or deploy customized fake CAPTCHA-like validation.
“Recent security blogs on phishing campaigns and cybercriminals using reCAPTCHA and research papers like PhishTime and CrawlPhish show an increasing trend of CAPTCHA-protected phishing pages. Hiding phishing content behind CAPTCHAs prevents security crawlers from detecting malicious content and adds a legitimate look to phishing login pages,” Units 42 researchers noted.
Over 7,572 Unique URLs Discovered in One Month
According to Palo Alto Networks’ researchers, using CAPTCHA to launch phishing campaigns is now new common. Last month, the company detected 7,572 unique malicious URLs on more than 4,088 pay-level domains at an average of 529 new CAPTCHA-protected URLs a day.
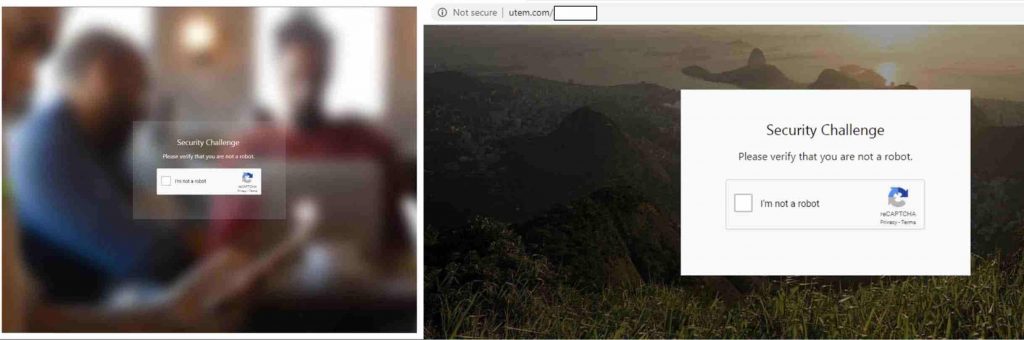
How can CAPTCHA be Abused?
A phishing attack isn’t the only way to exploit CAPTCHA, as it can be used to launch scams and evade CAPTCHA altogether through malicious gateways. Besides, it can be helpful to threat actors in deploying survey and lottery scams, which researchers noted are “some of the most common grayware pages.”
The user is promised a chance to win the lottery or fake payment in exchange for sensitive information such as the user’s address, annual income, date of birth, banking credentials, etc. Moreover, these URLs are used to deliver malware as well.
“For example, the URL davidemoscatocom serves a malicious JAR file that is hidden from security scanners by protecting the page with a CAPTCHA challenge,” researchers write in their blog post.
Detecting CAPTCHA-protected malicious URLs?
Unit 42 researchers spilled the beans on how CAPTCHA services are being exploited and provided exclusive details on how to detect such URLs. According to the researchers, users can detect phishing attempts through the association of CAPTCHA keys.
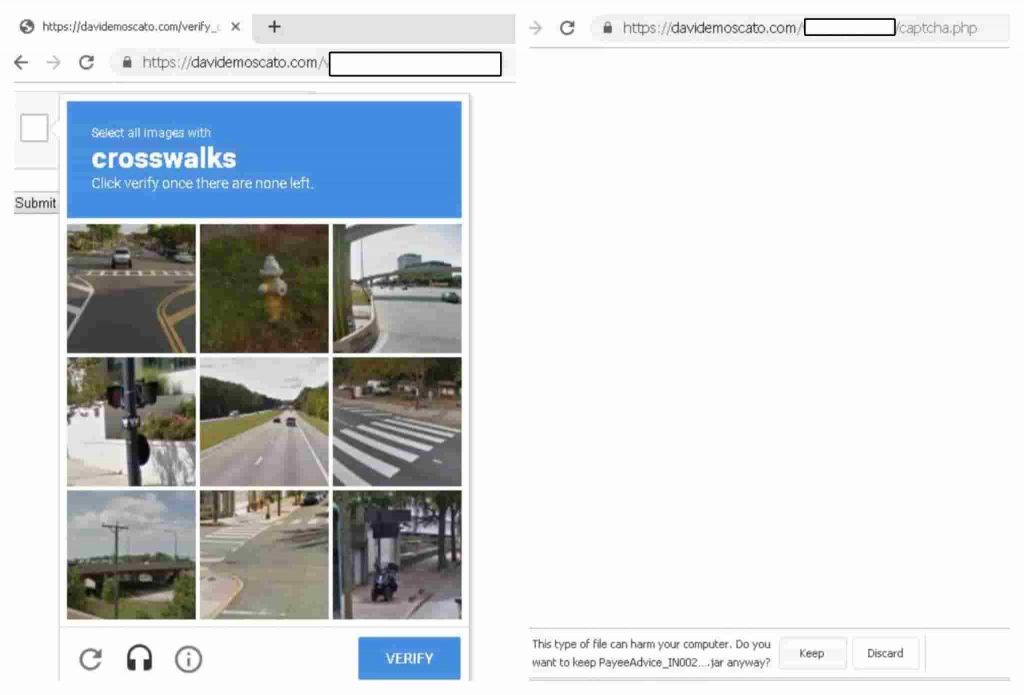
The CAPTCHA page will have sub-requests that could be parsed in HTML, revealing the reCAPTCHA API key used in the URL parameters. These identifiers can be parsed out or searched on other pages to verify the authenticity of the site.
“When malicious actors use infrastructure, services, or tools across their ecosystem of malicious websites, we have a chance to leverage these indicators against them. CAPTCHA identifiers are one great example of such detection by association,” researchers explained.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
