A new USPS Delivery Phishing Scam has surfaced, in which scammers are exploiting Freemium Dynamic DNS and SaaS Providers to steal victims’ login credentials and other data.
Cybersecurity researchers at Bloster AI have uncovered a new USPS Delivery Phishing campaign that employs sophisticated techniques to target victims in the United States.
It comes as no surprise that cybercriminals are employing sophisticated techniques to exploit reputable services for scams, making it challenging for innocent consumers to enjoy the holiday shopping season. This pattern is evident in the ongoing scam attack against Booking.com customers.
According to Bloster AI, an automated digital risk protection service, Walmart is a prime target this season due to the higher volume of shipping needs during November and December in the USPS phishing attack. Bolster’s CheckPhish has already discovered over 3,000 phishing domains mimicking Walmart.
The extensive phishing campaign mimics USPS, tricking consumers into thinking they have failed deliveries and late payments. Threat actors have substantially improved their attack tactics, transitioning from deceptive/misleading messages to luring victims into downloading financial/banking data-stealing apps.
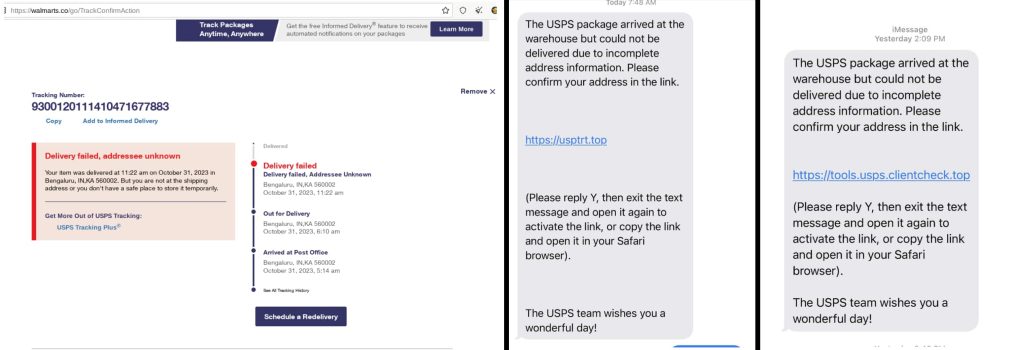
In their blog post, researchers noted that the domain walmartsco was active while they were writing the blog post. This domain mainly mimicked Walmart’s domain name and served USPS delivery tracking-related content and redirects to the authentic USPS portal to evade detection mechanisms.
Scammers distribute phishing links via email or SMS and use stolen data to lure victims into giving away sensitive banking data via social engineering techniques. Once a victim’s bank details are acquired, attackers can purchase, transfer money, or gain monetary benefits.
Phishing sites contain a site title such as USPS.com® – USPS Tracking® Results, and are designed to steal sensitive information like email addresses, names, phone numbers, residential addresses, and credit/debit card information. These sites cleverly redirect hyperlinks to legitimate USPS websites and use IP location to evade detection.
In some instances, hackers utilized personal information stolen in this scam, such as email address, phone number, or name, and sent emails/phishing scams pretending to be the victim. Such attacks involving social engineering are more successful if the email/SMS comes from a believable source.
Some phishing sites may also display tracking details as per the victim’s IP locations to appear authentic. Moreover, Bolster researchers noted that threat actors rely on these sites on pushed domains and exploit free hosting services.
These include DNS service hosting provider alviy.com and clear-cloud.com, an app hosting/deploying/maintaining tools provider. Attackers also host phishing sites using available domain names on now-dns.com and forumz.info, etc.
This campaign highlights the dangers of exploiting free hosting services and vulnerabilities in e-commerce platforms. Threat actors are focusing more on SaaS services and using AI technology, social media phishing, and brand impersonation scams to steal/lure customers from profitable sectors, such as finance, healthcare, and government agencies.
This phishing campaign primarily targets USPS customers in the US, but you may never know when attackers decide to expand the scope of this scam. It has impacted legitimate businesses’ reputations during the busy holiday shopping season. Proactive measures to identify and remove pre-malicious domains either manually or through automated takedown services are crucial to retaining consumer trust.
RELATED ARTICLES
- Scammers Leveraging Microsoft Team GIFs in Phishing Attacks
- Global CDN Service ‘jsdelivr’ Exposed Users to Phishing Attacks
- Phishing Scam Spoofs German Media, Broadband Conference Anga
- FBI: Silent Ransom Group Utilizes Callback Phishing for Network Hacks
- Hackers Aim at Crypto Wallets with Hacked Namecheap Phishing Emails