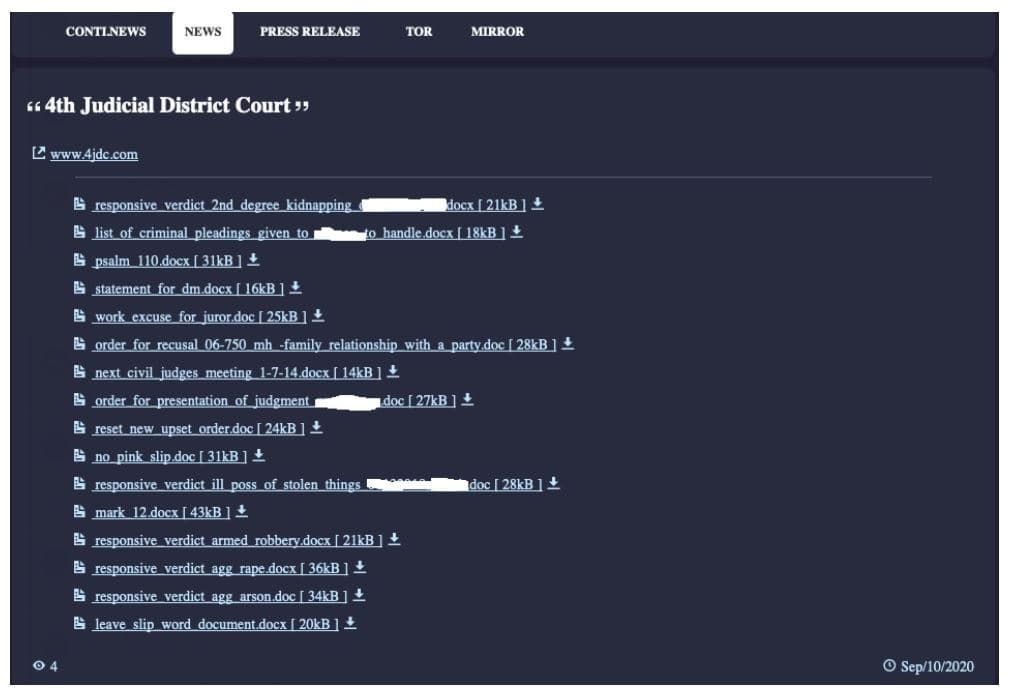
Conti ransomware operators attacked the Fourth District Court of Louisiana and posted proof of attack on their Dark Web site accessible through the Tor browser.
A US criminal court has become the victim of Conti ransomware strain, operated by a hacking group of the same name. The hackers have also published several court documents online.
Reportedly, the Fourth District Court of Louisiana’s website was targeted in the attack. After successfully stealing the court documents related to witnesses, jurors, and defendant pleas, the hackers posted proof of the hack attack on its Dark Web page.
Emsisoft’s threat analyst, Brett Callow told CBR that the Conti group is responsible for this attack. Callow noted that this group could be responsible for creating Ryuk, which means they are experienced cybercriminals and have a lengthy track record of attacking public sector organizations.
At the time of publishing this article, the Court’s website was offline.
Previous victims of Ryuk ransomware
It is worth noting that earlier this year, Florida’s Stuart Police Department computers were also hit by Ryuk ransomware. The attack caused Police to lose crucial evidence resulting in six suspects (alleged drug dealers) to walk free.
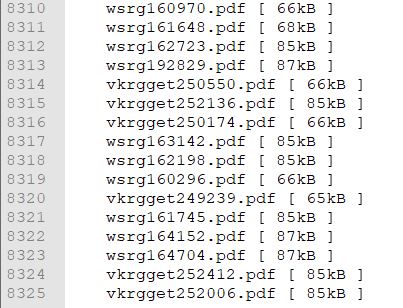
Furthermore, researchers believe that the attack against a German dealership of Volkswagen Group also involved the Conti ransomware group. In that particular incident, the attackers comprised the company’s service points’ systems and stole thousands of invoices, which they are gradually posting it on their data leaks portal. The hackers stole a total of 8,325 invoices in PDF format.
Full list of victims of Conti ransomware attack (72)
Neel Veterinary Hospital Adam Kutner Cares BostonCoach Horizon Controls Chris-Leef General Agency, Inc Star-Tam, Inc. Smith & McGhee, PC CB Masonry LindFast Solutions Group 4th Judicial District Court Allfasteners ThyssenKrupp Holding New Light Christian Christian Center News Réfrigération Noël Cambria County, Pennsylvania Beler Holdings Inc CCB Packaging Inc Pilkington Commercial Co., Inc. PanReac AppliChem ITW Reagents Division Our Lady of the Most Holy Rosary Catholic Community News a1fiberglass.com OCA Global M and M Merchandisers Adams County Memorial Hospital VUTEQ CORPORATION, LTD. Soloptical Sandream Impact LLC Marie Claire Boutiques Murray Engineering PTY Ltd & FSI Architecture PC JohnBear Bruckner Truck Sales Inc The Dobco Group Motta S.p.A Gestoria Auto Gestion Waldhoff gmbh Co Quality Resource Group City of Rocky Mount Romeo Engineering Inc Naman Howell Smith; Lee, PLLC Oil Company Greenville SC & the Upstate - Echols Oil Company, Inc Carbon Power and Light Filtration Group Pontotoc County Sheriff’s Office The Volkswagen Group Ventura Orthopedics National Wire Cable Corporation Precision Tandems Inc Aigües de Terrassa M3P Directional Services Visual Impressions Temgroupinc Peugeot Motocycles Westland Horticulture LH EVANS VIP Computers LLC Florida Chamber of Commerce LF ILLUMINATION LLC LHC Group Inc GAR Equipment Hershey Equipment Co Inc Sice Inc Image one electric gas industries association inc Hms Insurance Associates, Inc Marriott international inc Landmark resort hotel beach Yorkcontainer Joliet Park District McCloskey Mechanical Contractors Master Kid Inc Axxess International Inc
How Conti ransomware functions
Conti is a crypto-malware, discovered first in December 2019. Since then, it has become excessively common and mainly targets corporations and public sector institutions. It laterally spreads across the targeted network using various techniques to acquire domain admin credentials.
After gaining the necessary privileges, it deploys the ransomware and encrypts the devices attached to the network. It uses a range of techniques to evade security measures and can execute around 160 individual commands. Around 146 of these commands focus on blocking several Windows services.
Conti group is believed to be the Ryuk group’s successor and is operating as a private RaaS (Ransomware as a Service). According to Advance Intel’s Vitali Kremez, this new group boasts of a team of experienced hackers who receive a generous share from the ransom amount. Hence, there is a sudden increase in Conti infections.
Kremez stated that Conti ransomware is based on Ryuk’s code and uses the same ransom note template as Ryuk’s earlier versions. Moreover, Conti is using similar TrickBot infrastructure as Ryuk used in its ransomware attacks.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.









