Lately, Apple users including celebrities have been targeted by cybercriminals with malware and phishing scams — This phishing scam is also after iCloud accounts.
Recently IT security researcher Mehrdad noticed Apple users reporting that they couldn’t access their iCloud accounts. He then did some social engineering but didn’t find anything until one of his clients mentioned that they had received an email from Apple several days ago. It claimed his iCloud account has been blocked and asking them to click on a link in the email.
Upon looking at the email, it seemed legit but after tracing header of the email he discovered two things:
1. The email wasn’t sent from apple
2. The link in the email body doesn’t belong to the official website of iCloud and redirect to somewhere else!
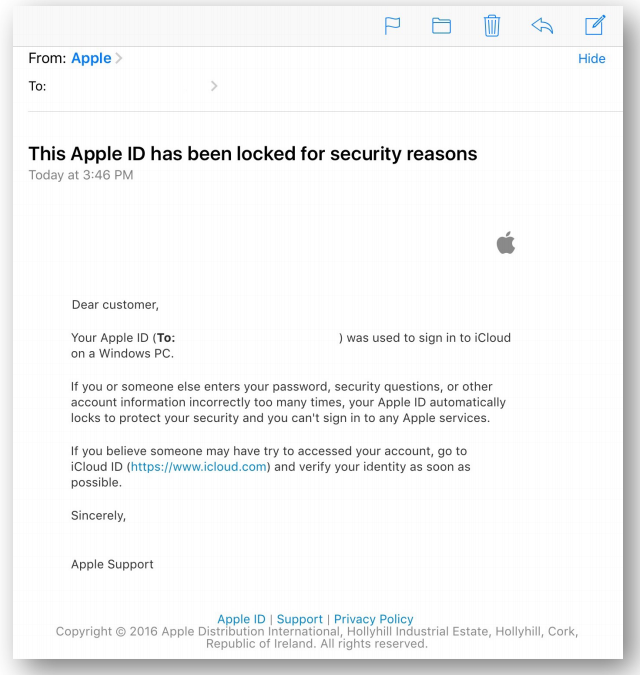
➢ Sender: [email protected]
➢ URL: www (dot) cityjoinery (dot)com/iCloud
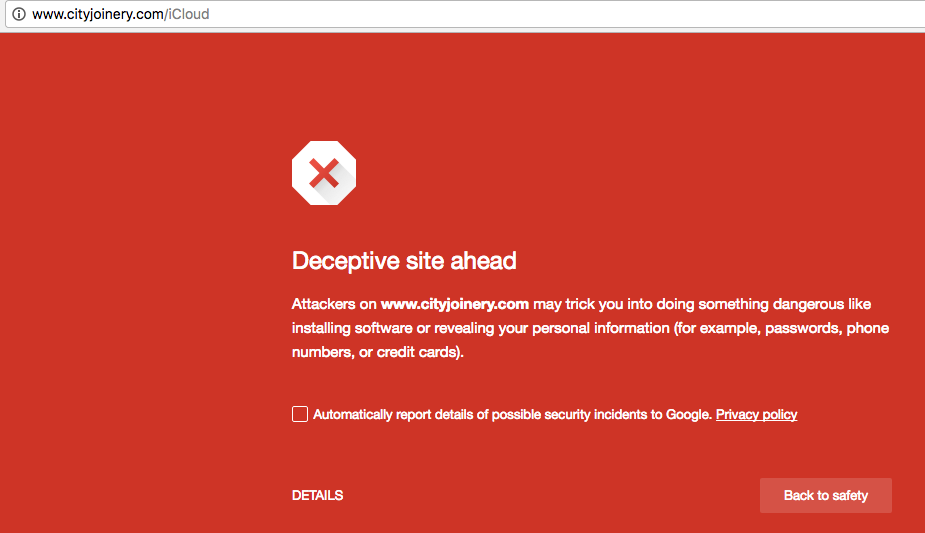
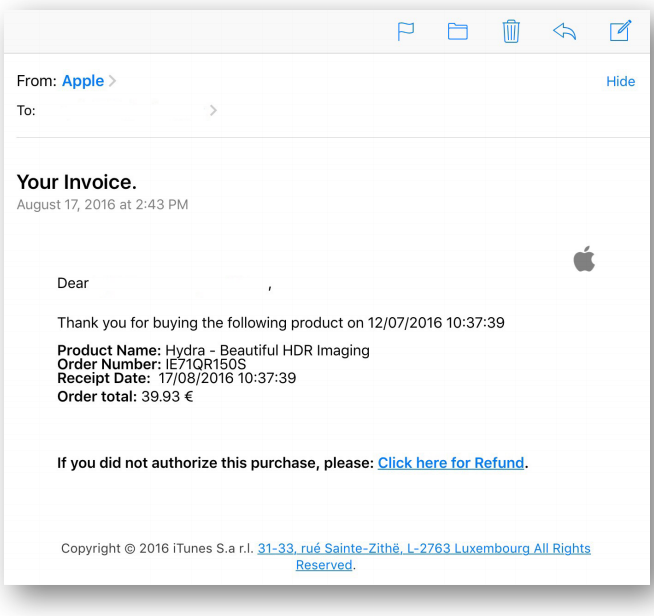
This is an old trick which you may already know as “phishing” but even today it’s a growing threat and one of the most successful ways to steal someone’s data. Here is another email that Mehrdad found encouraging users to confirm that they had made a purchase from Apple
➢ URL: http://manageid.yahoo.com.265.hounderbounder.com/id/.
At the time of publishing, the phishing scam on the above-mentioned link was removed however here is a preview of the phishing email.
Must Read: 11 easy tips to secure your Mac against hackers
Technical details:
When an SMTP email is sent, the initial connection provides two pieces of address information:
* MAIL FROM – generally presented to the recipient as the Return-path: header but not normally visible to the end user, and by default, no checks are done that the sending system is authorized to send on behalf of that address.
* RCPT TO – specifies which email address the email is delivered to, is not normally visible to the end user but may be present in the headers as part of the “Received:” header.
Together these are sometimes referred to as the “envelope” addressing, an analogy based on the traditional paper envelope, and unless the receiving mail server signals that it has problems with either of these items, the sending system sends the “DATA” command, and typically sends several header items, including:
* From: Joe Q Doe <[email protected]> – the address that is visible to the recipient; but again, by default no checks are done that the sending system is authorized to send on behalf of that address.
* Reply-to: Jane Roe <[email protected]> – similarly not checked and sometimes:
* Sender: Jin Jo <[email protected]> – also not checked The result is that the email recipient sees the email as having come from the address in the From: header; they may sometimes be able to find the MAIL FROM address; and if they reply to the email it will go to either the address presented in the From: or Reply-to: header – but none of these addresses are typically reliable, so automated bounce messages may generate backscatter.
Phishing is the attempt to obtain sensitive information such as usernames, passwords, and credit card details (and sometimes, indirectly, money), often for malicious reasons, by masquerading as a trustworthy entity in an electronic communication.
The word is a neologism created as a homophone of fishing due to the similarity of using a bait in an attempt to catch a victim. Communications purporting to be from popular social websites, auction sites, banks, online payment processors or IT administrators are commonly used to lure unsuspecting victims. Phishing emails may contain links to websites that are infected with malware.Phishing is typically carried out by email spoofing or instant messaging, and it often directs users to enter details at a fake website whose look and feel are almost identical to the legitimate one.
Phishing is an example of social engineering techniques used to deceive users and exploits the poor usability of current web security technologies. Attempts to deal with the growing number of reported phishing incidents include legislation, user training, public awareness, and technical security measures. Many websites have now created secondary tools for applications, like maps for games, but they should be clearly marked as to who wrote them, and users should not use the same passwords anywhere on the internet.
Phishing is a continual threat, and the risk is even larger in social media such as Facebook, Twitter, and Google+. Hackers could create a clone of a website and tell you to enter personal information, which is then emailed to them. Hackers commonly take advantage of these sites to attack people using them at their workplace, homes, or in public in order to take personal and security information that can affect the user or company (if in a workplace environment). Phishing takes advantage of the trust that the user may have since the user may not be able to tell that the site being visited, or program being used, is not real; therefore, when this occurs, the hacker has the chance to gain the personal information of the targeted user, such as passwords, usernames, security codes, and credit card numbers, among other things.
Solution:
➢ Train people
➢ Use Anti-phishing software
➢ Browsers alerting users to fraudulent websites (like firefox and chrome)
Eliminating phishing email:
Specialized spam filters can reduce the number of phishing emails that reach their addressees’ inboxes, or provide post-delivery remediation, analyzing and removing spear phishing attacks upon delivery through email provider-level integration. These approaches rely on machine learning and natural language processing approaches to classify phishing emails. Email address authentication is another new approach.
Report the scam to anti-phishing teams:
Reporting phishing to both volunteer and industry groups, such as Cyscon or PhishTank.
RELATED: APPLE USERS HIT WITH LARGE-SCALE SMISHING SCAM
Legal response:
In the United States, cyber criminals who create a fake website to defraud consumers can be sent to prison for five years and pay a fine of $250,000.
Identify legitimate websites :
• Which site (exact URL)?
• Use SSL?
• Who is the authority?
If you suspect you are under phishing attack, you can analyze the header of that email on online email header analyzer like ‘What is my IP‘.
In case that you don’t know what is the email header and where to find it click here.
Did you enjoy reading this article? Kindly do like our page on Facebook, follow us on Twitter and Google + and help us grow.
