Akamai has published new research explaining techniques used by the operators of a cryptocurrency mining botnet campaign to evade detection in which cybercriminals are abusing Bitcoin transactions to carry out illegal crypto mining operations while staying under the radar.
The BTC blockchain transactions are exploited to hide the backup C&C server addresses so that the botnet could receive the attackers’ commands uninterruptedly.
Such servers are hunted continuously by security teams and law enforcement authorities to render these campaigns dysfunctional. However, due to backups, the takedown could become problematic.
According to Akamai researchers, this is a straightforward but ‘effective’ way of defeating takedown attempts through which operators have mined more than $30,000 in Monero to date.
Attach Chain Details
Akamai reports that the first step in the attack chain exploits RCE vulnerabilities (remote code execution) such as CVE-2015-1427 and CVE-2019-9082 (Hadoop Yarn and Elasticsearch) that impact software.
Instead of hijacking the system in some attacks, the RCEs are modified for creating Redis server scanners. Their purpose is to find additional Redis targets for crypto mining.
To trigger an RCE, a shell script is deployed on a vulnerable system to deploy Skidmap mining malware. This script can kill off existing miners, disable security features, or modify SSH keys.
How it Maintains Persistence
To keep distributing the malware and maintain Persistence, rootkits and time-bound job schedulers called Cron Jobs are used. But to re-infect targeted systems, static IP addresses and domains are used, which researchers explain are usually “identified, burned, and/or seized” by security teams.
This is why the operators have included backup infrastructure in this campaign so that failed infections can download and upload infection, update the infected device, and use new domains and infrastructure.
Uncensorable and Unseizable Method
According to Akamai’s analysis, in December 2020 the campaign operators added a BTC wallet address in the crypto mining malware’s new variant. They also added bash one-liners and a URL for a wallet-checking API, which indicates that the wallet data is fetched by the API used to calculate the IP address.
Later, this address is used to maintain persistence, obfuscate, and pile the blockchain’s configuration data. They transfer a small amount of Bitcoins into the wallet to recover the orphaned infected systems.
Researchers claim that this method of distributing configuration information is “effectively unseizable and uncensorable.”
Conversion of Satoshi Values
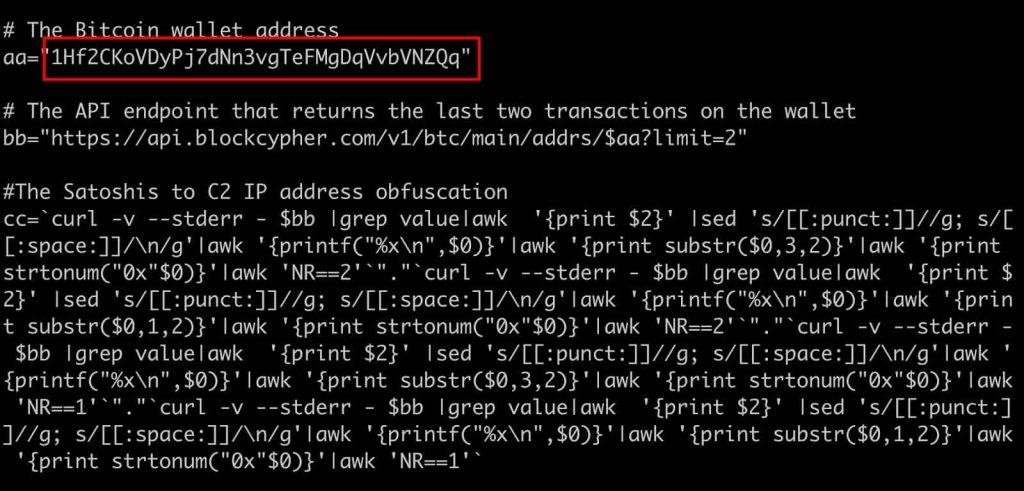
The operators use four bash one-liner scripts to convert wallet data into an IP address. These scripts send an HTTP request to the blockchain explorer API for the wallet and the Satoshi values of two of the most recent two transactions converted into the backup command & control IP.
Hence, the infection uses the wallet address as a DNS record while the transaction values are used as an A record.
“The variable aa contains the Bitcoin wallet address, variable bb contains the API endpoint that returns the latest two transactions used to generate the IP address, and variable cc contains the final C2 IP address after the conversion process is completed. To achieve this conversion, four nested Bash one-liners (one each, per-octet) are concatenated together. While the mess of cURLs, seds, awks, and pipes is hard to make sense of at first glance, it’s a fairly simple technique.”
Did you enjoy reading this article? Don’t forget to like our page on Facebook and follow us on Twitter!