It has always been believed that Cisco routers being used in the enterprise environment could be hacked via installation of backdoor firmware, but it was always just a theory.
Now, security researchers over at Mandiant, an American cyber security firm and a FireEye company, have confirmed that hacking of Cisco routers through backdoor firmware installations is possible and the researchers have found its presence on fourteen routers being used in organizations based in four different countries, namely Philippines, Ukraine, Mexico and India.
The malware being used to infect the routers is codenamed SYNful Knock, which silently modifies the router’s firmware image that provides attackers with private backdoor access to the infected network. This malware is not only flexible but also has the capability to customize itself and can be updated once installed on the router.
The attack remains undetectable and can remain challenging to detect because it makes use of a non-standard packets as a form of pseudo-authentication.
SYNful Knock is actually used to modify the IOS image being used by the Cisco routers. The researchers found that Cisco 1841, 2811, and 3825 are the three known affected routers. These routers are widely used by businesses and organizations to provide networked services.
However, it is believed that other Cisco routers using similar IOS image and core functionality could also be vulnerable to the firmware backdoor attacks.
The attack method being used by the hackers to infect and install the malicious firmware in the router is not exploiting a zero-day vulnerability, rather, researchers found out that the login credentials of the affected routers were revealed by the attackers or set to default.
Furthermore, the router is being used as a hub in the network that controls all the connected devices and computers, so this makes it an ultimate target for the attackers to further infect the network.
What SYNful Knock Malware Is Capable Of:
The router implant, SYNful Knock, comprises of an amended Cisco IOS software platform that allows the hacker to remotely load various functional modules directly from the anonymity of the Internet. The infected firmware also lets the attacker access router unrestricted through a secret backdoor password.
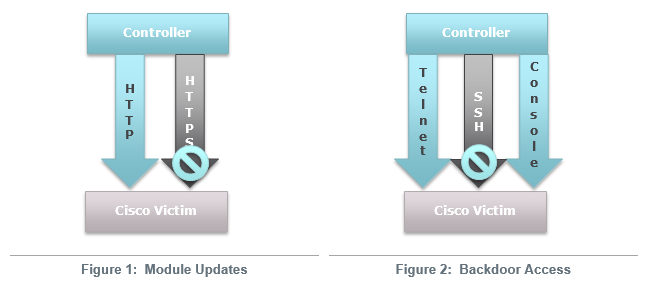
The functional modules that are loaded by the hacker can be enabled through the HTTP protocol, which has not been secured nor used a precisely developed TCP packets sent to the routers interface. These TCP packets use a modified sequence and consistent acknowledgment numbers.
The modules loaded into the router can self-manifest themselves as a self-governing executable code within the router’s IOS image that offer a very similar functionality as the backdoor password. These backdoor passwords allow hackers to gain access to the router through the Telnet and console.
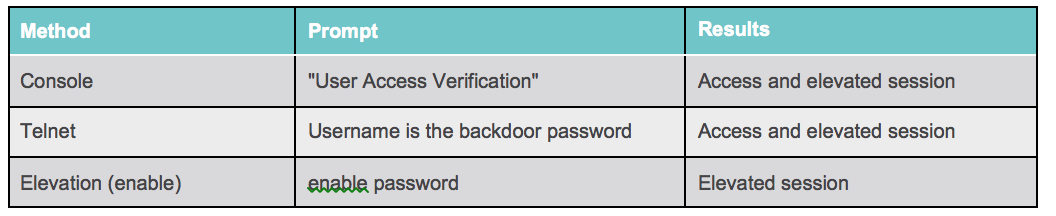
You can see in the illustration embedded below about how attackers can gain access over to the Cisco routers.
Another serious security concern this firmware attack possess is that it exists within a modified Cisco IOS image file. This continues to maintain its presence even after the router is rebooted, albeit the modules remotely loaded by the hacker will no longer exist on the router because it is stored in the volatile memory which will not be available after a reboot.
FireEye