The operation is not limited to websites – MagBo is home to a number of cybercrime-related activities including selling of compromised servers.
Just like xDedic was shut down in 2019 after making headlines for selling access to hacked RDP endpoints and over 85,000 credentials, it seems that another service will soon be coming under the radar of law enforcement authorities. It’s none other than MagBo, the infamous online marketplace created exclusively to carry out cybercrime activities.
According to the latest report from threat intelligence firm KELA, MagBo is offering access to over 43,000 hacked servers and some of these belong to state and local governments, ministries, financial institutions, and health care facilities.
See: Dark web marketplace found selling access to airport’s security system
For hackers, governmental servers are of the highest profit as they are being sold for $10,000/piece while small business websites can be bought for a couple of cents only.
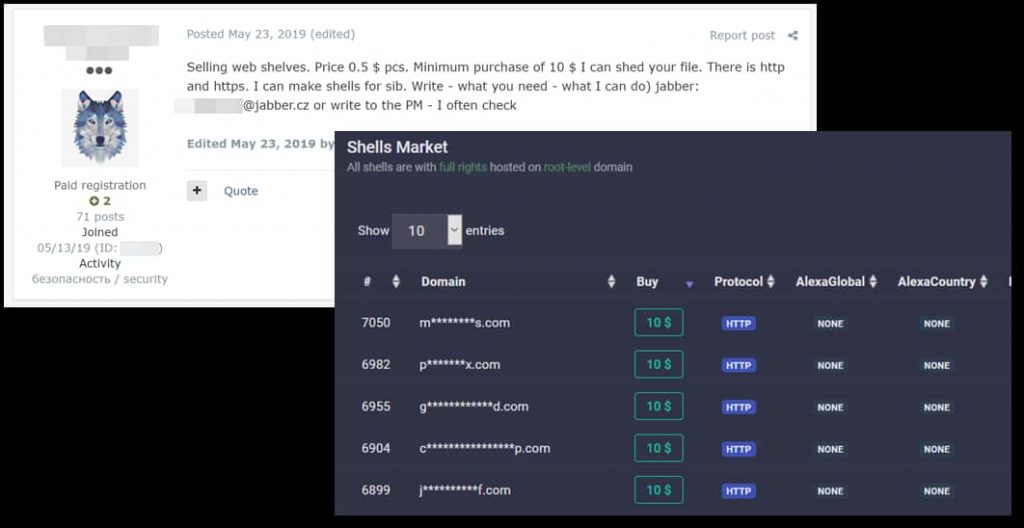
MagBo is a notorious online marketplace where hackers can buy or sell hacked servers. It has grown rapidly since its establishment in 2018.
According to researchers, in only two years it has grown over 14-times from its original size and is selling access to 43,000 hacked websites, which is a giant leap from the 3,000 listed hacked sites the company featured in September 2018. It is receiving up to 400 new additions with 200 transactions per day.

According to the company’s blog post,
One reason for this might be the operation model – MagBo is a decentralized platform serving multiple threat actors who can upload their wares. KELA’s data shows 190 different threat actors currently have active listings on the market.
KLEA also identified that there are active listings on the market from 190 different cybercriminals and quite possibly MagBo has earned over $750,000 in revenue since 2018 only through selling hacked servers.
Those buying credentials from MagBo use it to run black hat SEO campaigns while some may target e-commerce sites, intranets, and web-cleaning platforms with ransomware.
A majority of the servers sold via MagBo are accessed through web-shells, some can be accessed remotely through compromised CMS and FTP credentials, while there are servers that are accessed through compromised SSH hosting panels. The number of servers offering SQL access is relatively low.
KLEA claims that many websites on MagBo are running an outdated WordPress version or plugins, and since these weren’t updated timely, they became easy prey for hackers.
If you own a business website or planning to start a blog, here are two guides (1 & 2) detailing how to protect both from hackers and other malicious elements. Stay safe online!
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.
