For now, SYS01 stealer is targeting Facebook accounts of employees working for manufacturing companies, critical government infrastructures, and other sensitive industries.
The cybersecurity researchers at Morphisec have revealed details of an advanced information-stealing malware campaign which they began tracking in November 2022. They dubbed the malware SYS01 Stealer.
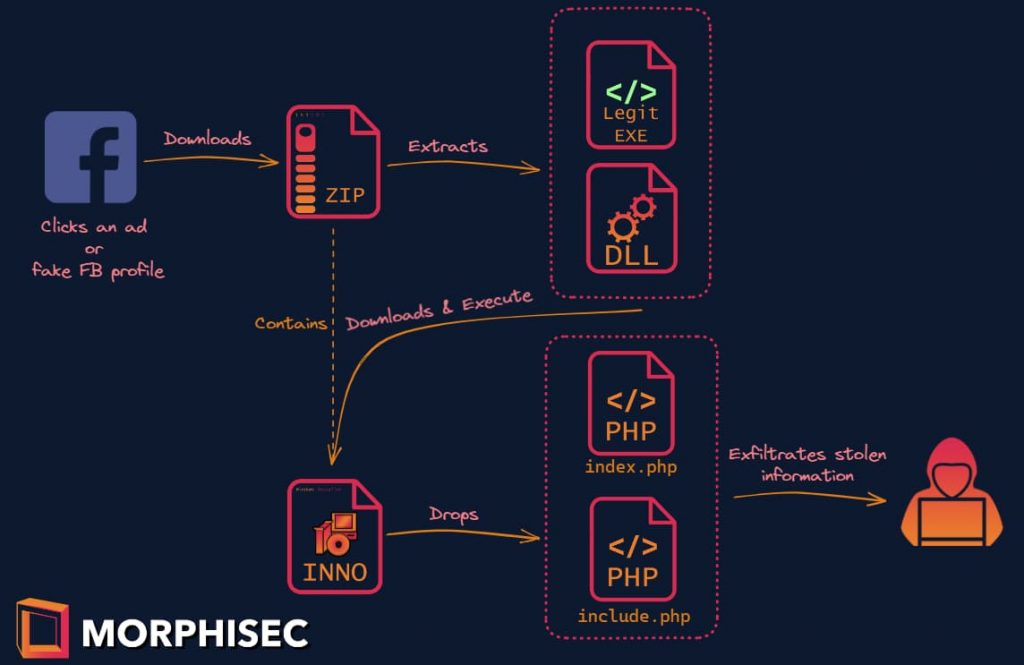
Researchers noted that SYS01 Stealer has been targeting critical government infrastructure and manufacturing firms’ employees. The attackers are targeting Facebook business accounts of their targets through Google ads and fake Facebook profiles, which promote games, cracked software, and adult content to compel their victims into downloading a malicious ZIP file.
The malicious use of Google Ads should not come as a surprise, since crooks have been abusing Google’s Ad Ecosystem for some years now. Just a couple of weeks ago, Google Ads were found to be spreading malware in fake messenger and browser apps.
The malware is executed on the target’s machine through DLL side-loading. The campaign was first noticed in May 2022, when it was attributed to Zscaler’s Ducktail operation, which was later rendered incorrect.
Detailed analysis
In a blog post, Morphisec researchers wrote that the archive has a legitimate application as a loader, which is vulnerable to DLL side-loading, and a malicious library, which drops the Inno-Setup installer through side-loading. In turn, the final payload is deployed as a PHP application, which actually contains malicious scripts that perform data exfiltration. Archive persistence is ensured through a PHP script.
It performs this task by setting a scheduled task. The main stealer script supports numerous other tasks, including letting the attacker check whether the victim is logged in and has a Facebook account.
Furthermore, this script also supports the downloading and execution of files from a certain URL and can upload files to the C2 server. It may also execute commands.
What’s the Objective?
This campaign is designed to steal sensitive details from the victims’ devices, such as cookies, login data, and personal and business Facebook account information. The attacker has included Rust, PHP, Python, and advanced PHP encoders to advance the delivery chain, which has helped them evade security vendors successfully for the past five months.
SYS01 Similarities with other Infostealer?
Morphisec analysis revealed that SYS01 uses the same loading techniques and lures as the S1deload infostealer (PDF) discovered by Bitdefender. However, it is worth noting that the final payload isn’t the same.
You can stay protected from SYS01 stealer by implementing a zero-trust policy and restricting users’ rights to download and install programs. Since this campaign is based on social engineering, users should be aware of the tricks adversaries can use against them.
Protect Yourself
If you are an employee at a government or critical infrastructure organization, you should watch out for malware attacks, especially on social media sites. Here are some steps on how to do so:
- Be wary of unsolicited messages, friend requests, and links from unknown sources on social media platforms like Facebook.
- Verify the identity of the sender before clicking on any links or downloading any attachments.
- Install and update anti-virus software and firewalls on your device and make sure they are up-to-date with the latest security patches.
- Use strong and unique passwords for your social media accounts and avoid reusing passwords across different accounts.
- Enable two-factor authentication (2FA) to provide an extra layer of protection for your accounts.
- Avoid using public Wi-Fi networks, especially when accessing sensitive information or logging into social media accounts.
- Regularly back up important data to an external hard drive or cloud storage service.
- Report any suspicious activity, messages or links to your organization’s IT department immediately.
- Stay informed about the latest malware and cyber security trends by attending regular training sessions and seminars.
- Follow your organization’s security policies and procedures, including those for social media use.
