It is no surprise that hackers often create clones of popular websites to scam users. Now, investigative security journalist Brian Krebs has revealed that there is a fake version of popular encrypted messages web service Privnote.com was caught redirecting user’s cryptocurrency to scammers.
This reminds us of scam in which fake version of Tor browser was caught stealing Bitcoin from dark web users. In the latest one, however, it has been revealed that unsuspecting users of the original website Privnote.com were lured to an identical version of the original site titled Privnotes (dot) com.
See: Fake govt-issued COVID-19 contact tracing apps spread spyware
The only difference is that instead of offering encrypted, self-destructive messaging service, as the genuine website does, the fake site read and edited all the messages.
Krebs collaborated with security expert Allison Nixon to dig deep into the matter, and identified that the fake website was created to steal cryptocurrency payment requests sent through the original platform.
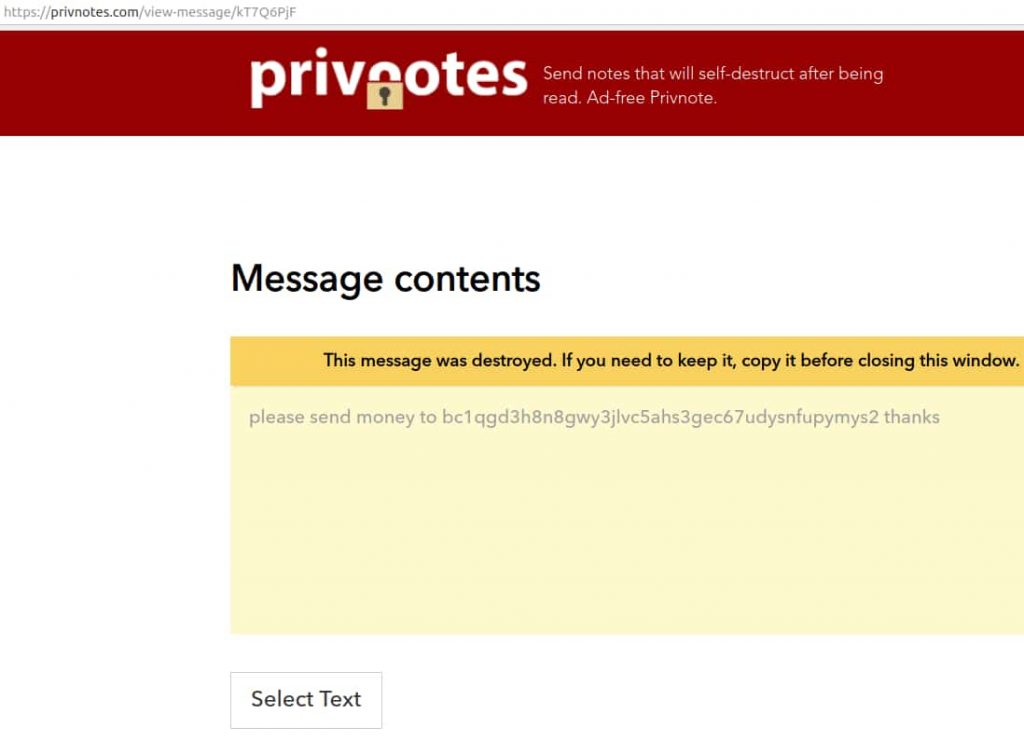
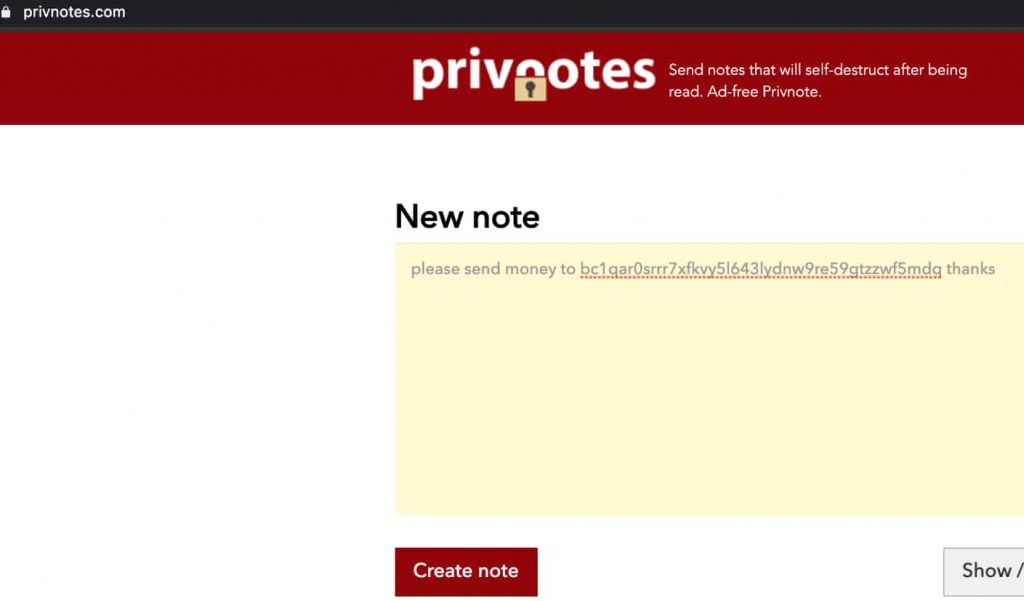
The website contained a script that looked for messages containing Bitcoin addresses and modified the original address with the scammer’s address. Hence, the funds arrived at the scammer’s address instead of their legitimate destination.
To avoid detection, the first four characters of the modified Bitcoin address were kept similar to the original one. Furthermore, the fake version of Privnote.com modified the Bitcoin address only if the original address was accessed from a different IP than that of the sender.
This means if the internet address of the receiver and sender was the same, the funds could not be transferred to the scammer.
Krebs noted that Privnote.com owners informed him earlier this year that a cloned version of their site had surfaced on the web that was trapping the services’ regular users. He mentioned that the scammers have created an identical website address, which is why those searching for Privnote.com will most likely end up at Privnotes.com given the stark similarity of the addresses.
“Privnotes.com is confusingly similar in name and appearance to the real thing, and comes up second in Google search results for the term “privnote.” Also, anyone who mistakenly types “privnotes” into Google search may see at the top of the results a misleading paid ad for “Privnote” that actually leads to privnotes.com” wrote Krebs in a blog post.
Hackread.com tested the fake website using Incognito session and VPNs and discovered that the scammers had retracted the malicious behavior of the website for now. Also, at the time of publishing this article, the fake version of the site was offline and unreachable.
It is worth noting that in February 2020, scammers had cloned ProtonVPN’s website to spread password stealer malware. In August 2019, a fake version of the NordVPN website was caught stealing financial information of users after spreading banking trojan.
Nonetheless, Krebs claims that this is a very sophisticated scam that does serve as a reminder to website developers and users the repercussions of sharing sensitive financial data via a note sharing service.
Exclusive: Scammers using fake WHO Bitcoin wallet to steal donation
Moreover, web developers must squat similar domain names and their many variants before the scammers. Meanwhile, if you are interested, Hackread.com wrote a detailed guide on why typosquatting protection from coronavirus-themed registered domains is a must.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.