Valve, the developer of Counter Strike 2, is expected to address the rumours surrounding the new CS2 exploit. Meanwhile, be cautious and watch out for suspicious links from unknown senders.
A recently uncovered CS2 exploit (apparently an XSS vulnerability) has raised concerns within the gaming community, posing a potential threat to player security. This exploit reportedly utilizes HTML code blocks in-game to display GIFs, placing gamers at risk.
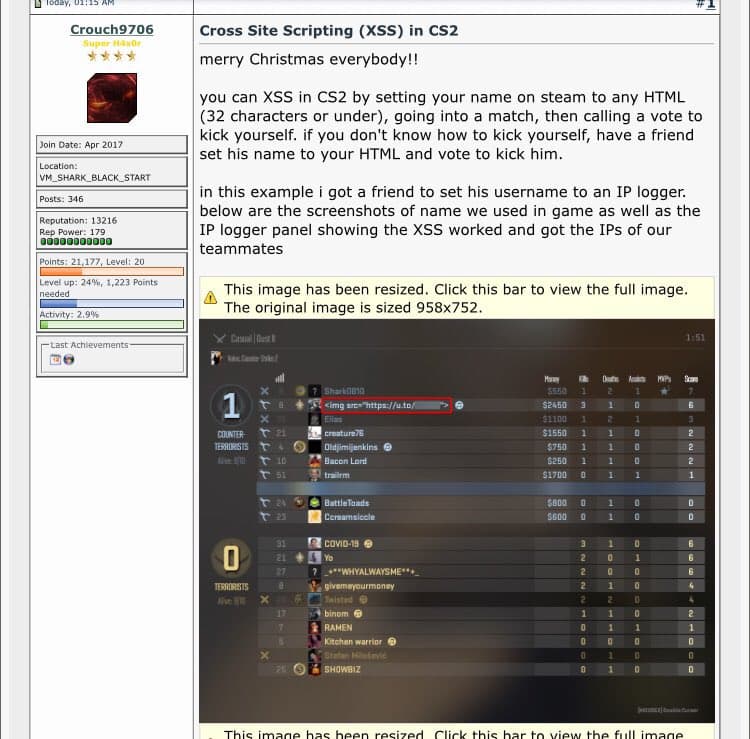
The implications extend to a broad spectrum of players, even those less inclined to frequent online play. Initially discovered by players experimenting with their Steam ID, the exploit allowed them to showcase NSFW GIFs to other players through the in-game kick menu.
Notable figures in the gaming community, including Ozzny, a CS2 creator with over 23,000 YouTube subscribers, have confirmed that those exploiting the glitch can access player IP addresses.
With concerns escalating about the exploit’s potential for executing code on gamers’ PCs, Ozzny and other experts strongly advise refraining from CS2 gameplay until the exploit is rectified.
HUGE SECURITY EXPLOIT IN CS2 RIGHT NOW⚠️
— Ozzny (@Ozzny_CS2) December 11, 2023
This image has been going around reddit for the last few hours (very explicit, blurred for obvious reasons). People were saying it's fake, but it isn't.
Apparently, there is a security exploit with Steam names inside CS2, which allows… pic.twitter.com/lcQqsAB5Ba
“Apparently, there is a security exploit with Steam names inside CS2, which allows people to change visual stuff inside the game with a simple HTML code linking an image. But this is not it you can also get the IPs of EVERYONE in the server using this method with the assistance of an IP Logger. (Not going to show much or explain how for obvious reasons, but it is very easy),” tweeted Ozzny.
In a Twitch video, Jason Thor Hall, an American cybersecurity researcher and game developer, highlighted the XSS vulnerability, urging gamers to refrain from CS2 until Valve, the developer, addresses the issue.
If you don't want to just take my word from it, here's an actual expert's opinion validating this issue:
— Ozzny (@Ozzny_CS2) December 11, 2023
(📽️ @PirateSoftware) pic.twitter.com/zm67088kMj
While the feasibility of code execution remains uncertain, the perceived risk is substantial, prompting a cautious approach. Gamers are strongly encouraged to suspend CS2 play until the exploit is patched, or clearance from Vavle is issued. The is expected to swiftly address the situation, with a fix expected shortly.
As a precautionary measure, users encountering a player with an in-game username resembling an HTML block are advised to exercise caution and avoid interaction. The safety of Steam accounts hinges on this vigilance. Updates will be provided as the situation develops.
If playing becomes unavoidable, it is crucial to remain vigilant against potential dangers, such as refraining from clicking on suspicious links or opening attachments from unknown senders.
What exactly is an XXS vulnerability
Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications. It allows a malicious user to inject client-side scripts into a web page viewed by other users.
The malicious code can then be used to steal user data, hijack user sessions, or redirect users to malicious websites. Here is a simplified explanation of how XSS works:
- A user visits a web page that contains an XSS vulnerability.
- The vulnerable web page accepts input from the user, such as a comment or a forum post.
- The user’s input is not properly sanitized or validated before being displayed on the web page.
- The malicious code is injected into the web page and executed in the user’s browser.
There is a discussion about this ongoing issue on Steam Community. Stay tuned for further updates as this story unfolds.