The largest DDoS attack on the Internet has occurred, following the exploitation of a new zero-day vulnerability by hackers.
- Google, Cloudflare, and AWS have confirmed that unknown adversaries exploited a new zero-day vulnerability called HTTP/2 Rapid Reset to launch digital history’s largest-ever record DDoS attack.
- The attack peaked at 398 million RPS, which is 7 times higher than the previous largest DDoS attack recorded by Google.
- AWS and Cloudflare had previously recorded DDoS attacks peaking at 200 million RPS.
- The zero-day flaw lets adversaries send specially designed HTTP/2 requests to a target server, triggering an extensive response, which is further amplified by sending it to vulnerable IoT devices or misconfigured servers.
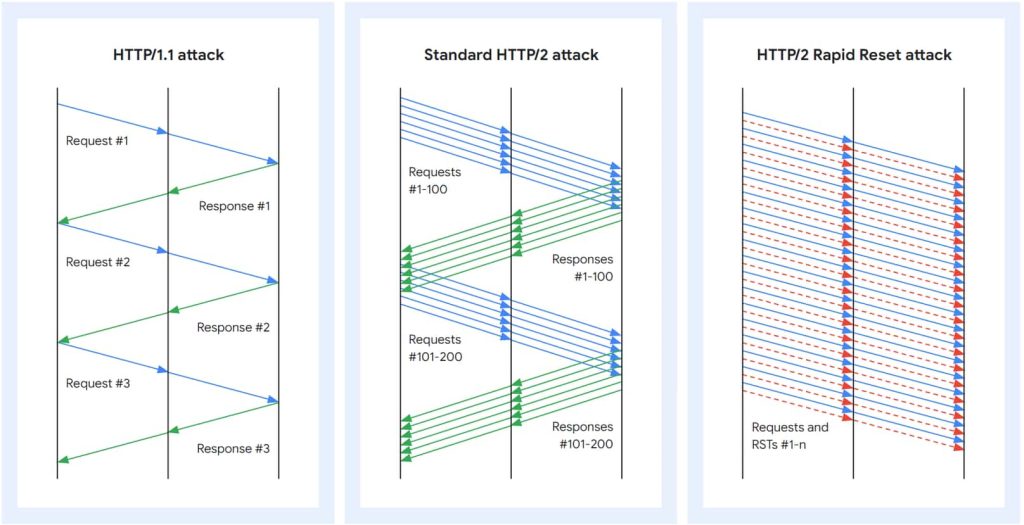
- This novel technique is based on stream multiplexing.
- In this case, threat actors sent amplified traffic to diverse targets, including financial entities, gaming corporations, and government agencies, causing significant damage to several of them.
Three of the world’s leading tech firms, Google, Amazon Web Services (AWS), and Cloudflare, have jointly disclosed a new 0-day flaw exploited by unknown threat actors to launch the largest Distributed Denial of Service attack (DDoS attack) recorded to date.
Dubbed HTTP/2 Rapid Reset, the vulnerability lets attacker send specially designed HTTP/2 requests to their target server and trigger a large-scale response. They can further amplify this response by sending the same request to as many vulnerable IoT devices and misconfigured servers as they want. The vulnerability is tracked as CVE-2023-44487 and has been assigned a CVSS score of 7.5 out of 10, rated High Severity.
The largest ever DDoS attack resulting from HTTP/2 Rapid Reset’s exploitation peaked at 398 million requests per second (RPS), seven times higher than the previous largest attack recorded by Google.
Cloudflare and AWS had previously recorded DDoS attacks peaking at slightly over 200 million RPS. Cloudflare claims to have mitigated over 1,100 other attacks, peaking at 10 million RPS until August 2023, and 184 of them were greater than the company’s previously reported DDoS record of 71 million RPS. These are still startling revelations compared to last year when the highest recorded DDoS attack peaked at 46 million RPS.
A wide range of targets have been identified, including financial institutions, government agencies, and gaming companies. The attack caused massive damage to many of these targets, but most were able to mitigate them through filtering, rate limiting, and other techniques.
In its blog post, Google noted that this is a ‘hyper volumetric novel attack that relies on stream multiplexing. The attack exploits a weakness in the HTTP2 protocol, which lets clients identify the server a previous stream has to cancel by sending an RST_STREAM frame. It is worth noting that the protocol doesn’t require client-server coordination for this cancellation, and the client performs it unilaterally.
The attack is dubbed Rapid Reset because when the RST_STREAM frame is sent from one endpoint right after sending a request frame, the other endpoint starts working and rapidly resets the request. The request gets cancelled later, but the HTTP/2 connection remains open.
This is a concerning issue because HTTP/2 protocol is a critical element of around 0% of all web apps and facilitates interaction between a browser and a website. It is responsible for determining the quality and speed of how visitors interact with websites.
Exploitation of such a critical protocol indicates that DDoS attack remains a potent and growing threat. Organizations must take necessary steps such as promptly patching systems, upgrading their security mechanisms, and using rate limiting and filtering or at least having an incident response plan to deal with DDoS attacks.