Last week we reported hackers are developing Android malware every 17 seconds, making it one of the most vulnerable OS ever.
Now a spoofed copy of the popular app named as “BatteryBot Pro” requested unnecessary permissions from the user during installation in an attempt to get full control over the user’s Android device, a researcher found out.
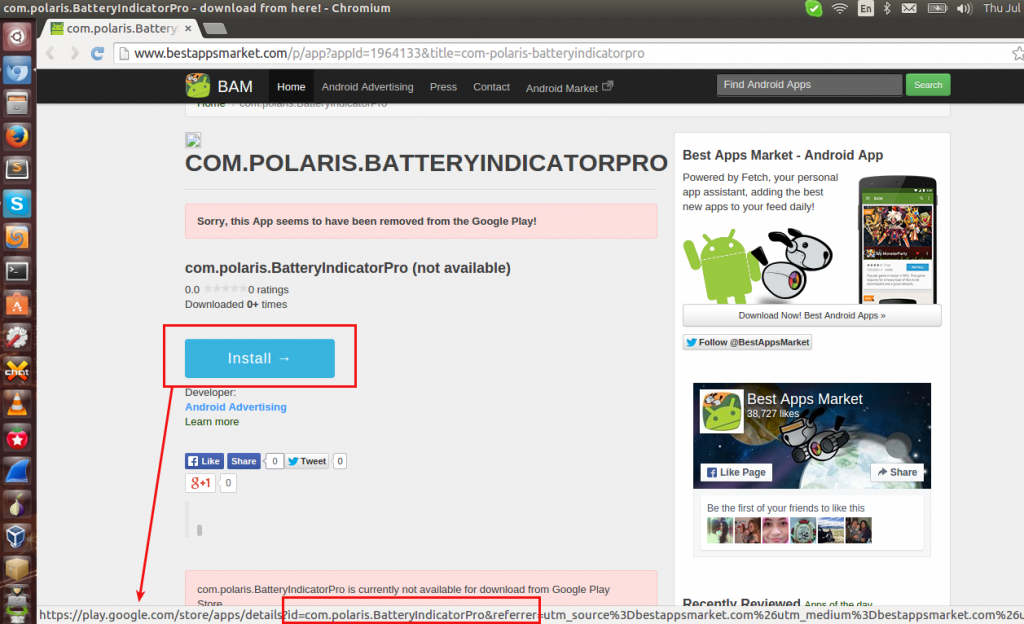
The app is alleged to imitate the functionalities of the authentic app and possess hidden ad-fraud activity, the app has recently been removed by Google from their official Android Play Store.
Report reveals 1 in every 5 Android Apps is Malware
For those of you who don’t know, BatteryBot Pro is a genuine battery monitoring app that already exists in the Android app store which offers its users to check detailed information related to their smartphone’s battery like its temperature, voltage, health, current information in mA, and other useful data.
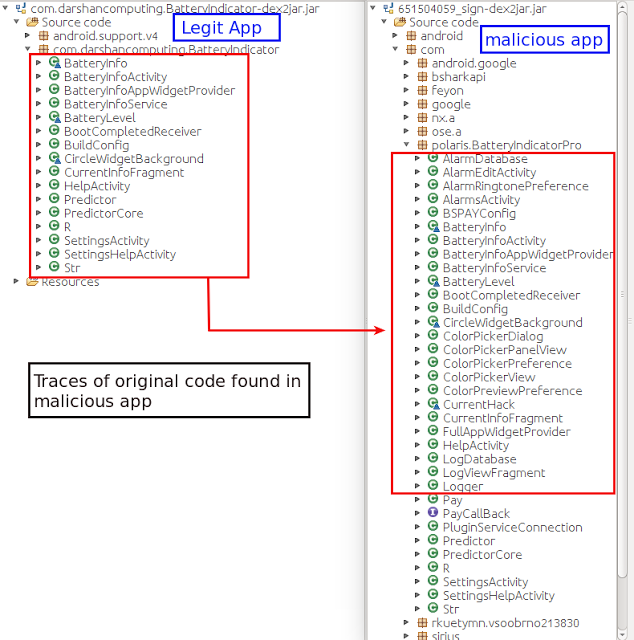
An unknown hacker decided to copy the original app’s functionalities while implementing irremovable malware, but thanks to a researcher named Shivang Desai who reported the app to Google and spoiled the developer’s vision of hacking Android devices.
The package of this app was named “com.polaris.BatteryIndicatorPro.”
The developers behind this app were trying to infect enough devices so that they can generate profit through ad click fraud and premium short messaging service (SMS) fraud. Apart from that, the app is precisely designed to download and install additional malicious Android APKs without the user’s permission. In addition to the hidden downloading of apps, the malware app also displays pop-up advertisements to the user.
“This malware was not only built with the purpose of displaying ads, it was also designed with more evil intentions,” Desai said.
Installation of Malware App
When installing the malicious app, it requested lots of more permissions as compared to the original app, some were normal but other were troublesome which included the permission to access the Internet, mount and unmount file system, send SMS messages, disable keyguard, get user account information, download without notification, and initiate outgoing calls.
After installation of the malicious app, the researcher found out that the malicious app “demanded administrative access,” which indicates that the objective of developer is “to obtain full control access of the victim’s device.”
Execution of Click Fraud and Ad Fraud Activities
But once the permission is granted by the victim, the malware app will provide exactly the same functionality of the original BatteryBot Pro app but continues to execute malicious activity in the background.
Apart from the execution of malicious activity the app also tried to download various advertisement libraries which carry a click fraud campaign, the security researcher found out.
“Some of these URLs were hard coded in the app and some were sent by the remote server.” – Shivang Desai, Zscaler Security Researcher.
Flashlight Apps Stealing Personal Information Stored On Your SmartphoneThe malware app also tried to pull some personal information from the device, including cell phone operator, availability of SIM card, IMEI number, language, cell phone model, location and available device memory.
Then depending on the collected parameters, the malware app begins to receive the list of advertisements to be displayed on the device along with the URL from where the ads will be fetched.
Unable to Uninstall Malware App
Apart from the execution of click fraud and ad fraud activities, the app is explicitly designed so that it once installed can never be uninstalled again, at least by the novice user. The app run with administrative rights so that the user cannot remove it.
According to the researcher who tried to uninstall this malicious app,
“While in some of the scenarios we were able to manually delete the app, the malware authors have taken care of ensure persistence. The malware silently installs an app with a package name of com.nb.superuser, which runs as a different thread and resides on the device even if the app is forcefully deleted.”
Don’t download apps from 3rd party
“A few traces of command execution were also seen in the app but were not fully implemented,” said Shivang Desai, the researcher at Zscaler. “Perhaps the developer is working on an upgraded version of the malware with proper ‘command-execution’ functionality,” Desai further added.
Report typos and corrections to [email protected]
Zscaler
