A security researcher has raveled some fantastic results over the percentage of vulnerable networks and devices around the world. His technique as a hacker was pretty straightforward and was a big time a matter of concern for all the people around the world. Let’s then see what the researcher found through his researches and how was he able produce such results.
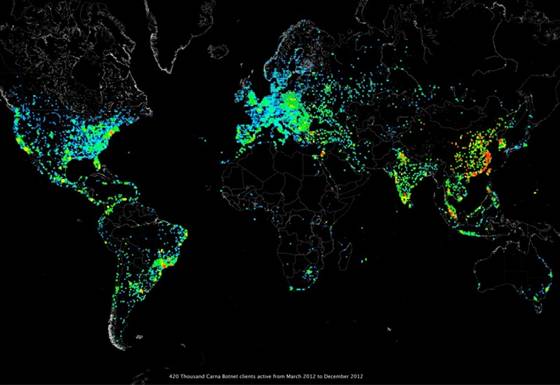
A map showing the locations of the botnet’s hundreds of thousands of infected devices.
Though, all these research was illegal it was carried out with nice intentions. The researcher in this scanned all the Ip addresses that were linked to the devices that were open for modifications. Through, this scanning, the researcher gained access to a number of devices all the compromised devices allowed him to gain to access to more IP addresses.
This way he was able to gain access to botnets of more then 420,000 devices in a single day. Most of the devices were really easy top got hold off the researcher found most the devices password and username: ‘default’ and admin’. Though, all these devices were simple devices they aren’t much worth of. These included printer and appliances, which were connected to the internet.
Working together these devices can trace ip addresses within an hour time. For researcher, it was a case in which robbing of one of one allowed him to find knobs of all the doors related to it. He himself admitted this as an illegal act in these words:
“This is most definitely illegal,” Roel Schouwenberg, senior researcher at Kaspersky Lab, told NBC News in an email. “Even if the intentions are good, which we have no way of verifying. unauthorized access remains unauthorized access.” Even if the compromised devices were thermostats or modems, “it doesn’t matter if it involves a regular desktop computer or a router.”
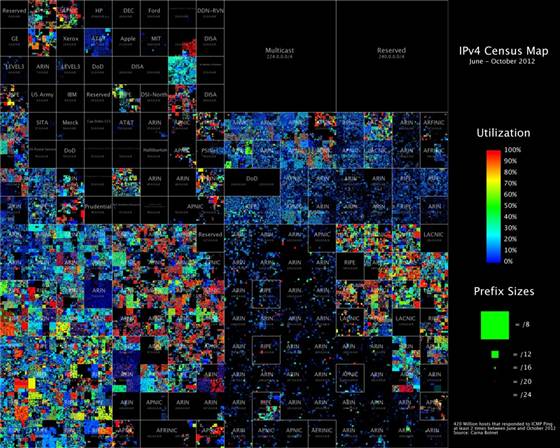
A map of the Internet, showing machines that responded to pings in various colors, while secure or unresponsive addresses are black.
But, researcher at the same time admitted he hasn’t caused damage to any of the data he found from the compromised devices all the botnet were safe and were easily removable. As a proof he showed one of the devices compromised by malicious software. He helped it by some code to be protected from such softwares. He also has build a massive database on all the IP addresses he traced out, the size of the data is bigger then the largest hard drive available in the market i.e. 9 terabytes.
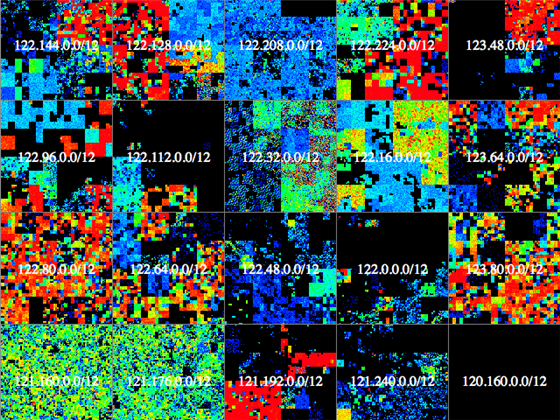
A close-up of data relating to a range of IP addresses scanned by Carna.
The main reason behind all this for the researcher was to give awareness to the people regarding the importance of strong login details in the internet world. Lastly, it determines how easily hackers can compromise the devices and steal significant data over the internet.
Source of Images and News: NBC News.