Thousands of WordPress websites have been hacked as hackers exploit a vulnerability in the tagDiv Composer front-end page builder plugin.
- The vulnerability is tracked as CVE-2023-3169.
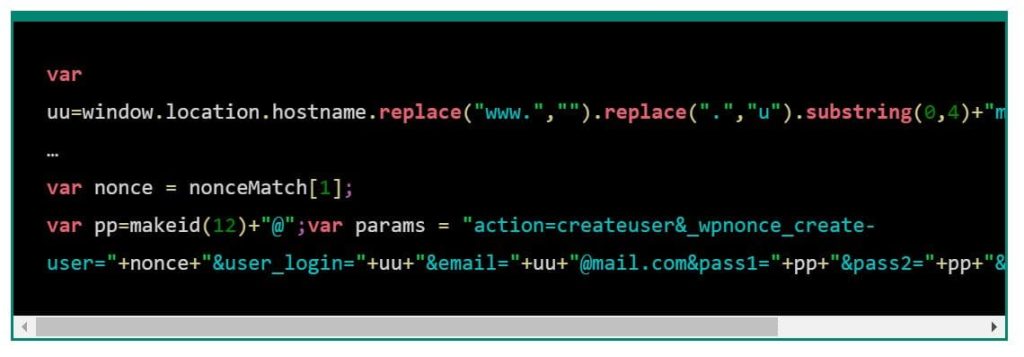
- It lets attackers inject malicious code into a particular location in the site’s database and propagate the code to every public page of the targeted area.
- Balada malware campaign reportedly exploits a recently patched vulnerability in Newspaper and Newsmag premium themes’ key component tagDiv Composer front-end page builder plugin.
- After obtaining initial access, attackers can upload backdoors, add malicious plugins, and create admin accounts to gain persistent access.
- This vulnerability was fixed in the plugin’s version 4.2.
Web developers using WordPress themes Newspaper and Newsmag must remain cautious as a recently patched vulnerability is being exploited to gain full control of a website. The vulnerable plugin is tagDiv Composer, an essential component of the Newspaper and Newsmag themes. These themes are available via the Theme Forest and Envato marketplaces, boasting over 155,000 downloads.
Vietnamese researcher Truoc Phan detected it first. It is tracked as CVE-2023-3169 and carries a severity rating of 7.1 out of 10, which is Medium. It was partially fixed in version 4.1 of tagDiv Composer and fully patched in version 4.2.
According to security firm Sucuri’s researcher Denis Sinegubko, threat actors exploit this cross-site scripting (XSS) vulnerability to inject malicious code in webpages, redirecting visitors to scam or compromised websites.
These sites offer fake tech support, push notification scams, and fraudulent lottery wins to lure users. Push notification scams force users into subscribing by displaying fake captcha dialogues.
The most concerning aspect of this research is that threat actors have already compromised thousands of WordPress websites. On NIST’s National Vulnerability database, it is reported that the tagDiv Composer WordPress plugin versions before 4.2 didn’t have authorization in a REST route and didn’t validate or escape some parameters when outputting them back.
This allows unauthenticated users to conduct Stored Cross-Site Scripting attacks. Exploiting this flaw, an attacker can inject malicious code into a website.
It is worth noting that this vulnerability originated in a malware campaign dubbed Balada by Sucuri. The company has been tracking it since 2017, when it was first detected, and estimates that since 2017, the malware has compromised over one million websites.
In September 2023, Balada injections were seen on more than 17,000 websites and 40,000 users. Over 9,000 of the newly detected infections resulted from injections facilitated by CVE-2023-3169.
Balada group prefers to gain persistent control over compromised websites by injecting scripts that create accounts with administrator rights. When real admins detect it, they remove the redirection but keep the fake admin accounts. The threat actor uses the admin privileges to create a new set of malicious redirect scripts.
Commenting on this story is Chris Hauk, Consumer Privacy Advocate at Pixel Privacy said, “Unfortunately, plugins and themes are favourite targets of hackers looking to exploit weaknesses in the WordPress ecosystem.”
Chris warned that “This flaw was only recently patched in the tagDiv Composer plugin, so there are likely still thousands upon thousands of WordPress sites using the old version of the plugin. WordPress admin should immediately update their plugins and templates to protect against this hack,” he advised.
It is necessary for any web developer or website administrator using WordPress themes Newspaper and Newsmag to inspect the site and event logs to detect signs of infection. Apart from removing malicious scripts, they must check for newly added admin accounts and backdoor code. Those still using the old version must immediately switch to TagDiv version 4.2 to prevent infection.
RELATED ARTICLES
- How To Secure WordPress Website From Cyber Attacks?
- Zero-Day Exploit Threatens 200,000 WordPress Websites
- 5 WordPress Security Solutions with Free SSL Certificates
- Flaws in 2 famous WordPress plugins put millions of sites at risk
- Hackers using hacked WordPress & Joomla sites to drop malware