Whenever your computer, smartphone device or any other Internet-capable gadget is connected to the Internet, there is always a risk of security threats. This is the reason why hacking has now become the norm.
The privately funded organizations, as well as the government agencies, are using various cyber spy technologies and tools so that they can discover the maximum eavesdropping possibilities while acquiring all the possible spying intelligence.
Getting hold of the hidden secretive data can be a challenging task for spying agencies because computer experts have specifically designed some computers in such a way that they remain offline and get no access to the internet.
This technique of protecting sophisticated data is known as air-gapping. In this technique, the computer systems are isolated from the Internet access, and not even connected or linked with other systems on the network.
This is an important step taken by the authorities as the digital data stored in these computers are highly secretive and must have to be protected from illicit access. That’s exactly how banking systems, classified military networks, payment networks, and the critical control system for large industries are protected!
But the recent exploration performed by the popular security corporation reveals that your computer and mobile phones can still get hacked even if they aren’t connected to the internet. So here are some of the ways through which your computer and mobile phone can be hacked – even if they are not connected to the online world!
1. Electromagnetic Radiation Spying
Every operation device that requires power once plugged into a power line will release electromagnetic radiation, and that radiation can be used to intercept information by various technologies verified by both the U.S. and the USSR (at the time it existed).
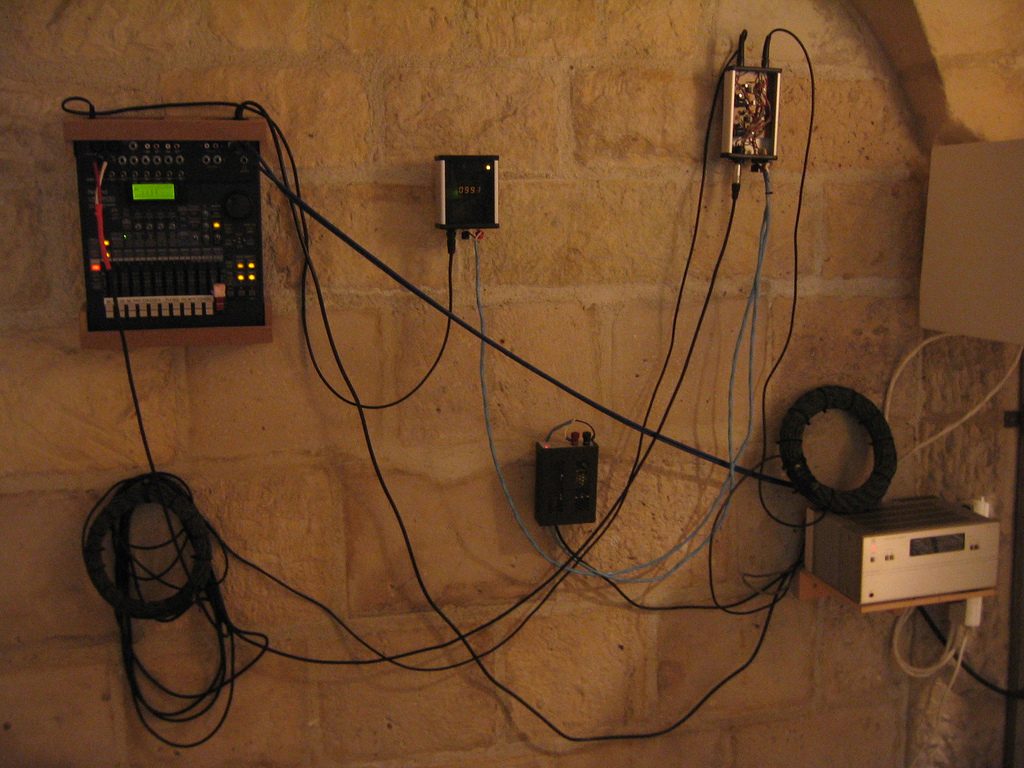
These radiations can easily be used to remotely record keystrokes. According to the Kaspersky Lab:
“Keystrokes can be remotely tracked with high accuracy at the 67-feet (20-meter) distance by using a homemade device that analyzes the radio spectrum and costs around $5,000. It is interesting to note that the attack is equally effective against common cheap USB keyboards, expensive wireless keyboards with a signal encryption, and built-in notebook keyboards. All of the devices work on the same principle and generate electromagnetic noise. The difference is stipulated by the signal power, which depends upon the length of the data transmission wire.”
2. Power Consumption Scrutiny
Since we were discussing electromagnetic radiations and electricity, certain researchers prove that it is possible to gather activity of any electronic gadget based on the amount of power it is drawing.
Using equipment known as Load Monitoring System, one can easily monitor the transformations in current and voltage so that they can understand the power consumption activity. Equipment like this is being used by electricity providers to better understand the load and power consumption of specific areas and to find out what exactly is causing all the changes in energy usage.
But what researchers found out is that Japan is using Non-Intrusive Appliances Load Monitoring System (NIALMS) which is working through a Neutral Network (NN), and this system is specifically designed for residential consumers so that they can find out what device is being used by the consumer.

In the same way, some medical researchers have created a computer program to detect network vulnerabilities in their computer networking systems. This monitoring program analyses the power consumption to detect if there’s any malware has been injected into the network.
3. Smartphone’s Accelerometer as a Key Logger
Your smartphone’s accelerometer, a sensor used to track the tilting motion of your smartphone, can be used as a keylogger to record keystrokes of any computer, according to the research performed by Patrick Traynor, Assistant Professor of Computer Science at Georgia Tech.
“The researchers developed a method to accurately translate the vibrations from typing on a keyboard picked up by the device’s accelerometer when placed on a desk near a PC The method is 80 percent accurate with a 58,000-word dictionary. Even that accuracy, though, requires thoroughly modern equipment.”

Computer hackers can use methods like these to eavesdrop user’s keystrokes, but the actual threat is pretty low because of the poor accuracy level.
4. Traveling on a Subway? You Are Being Tracked By the Hackers
Hackers can track the movements of millions of travelers traveling on a subway around the world, according to the researchers of Nanjing University. Hackers can break into the smartphone’s built-in motion detection technology i.e. accelerometer and can detect all the bumps and duration of a trip between stations.

“The ability to track subway riders represents a significant cybersecurity threat to the tens of millions of people who use public transportation every day. There are more than 5.5 million daily New York City subway passengers, and over half of those people are carrying smartphones, thus exposing themselves to tracking.”
According to the researchers, every subway station in the world possesses a unique fingerprint and every time a train runs between two stations, that specific fingerprint can be recorded by the smartphone’s accelerometer, possibly providing hackers with access to critical information like which subway station any specific person has traveled to.
5. Computer Keyboards Are Vulnerable
Voltmeters and a ray of the laser can be used to sniff computer keystrokes, according to the researchers Andrea Barisani and Daniele Bianco who found this exploit and demonstrated this technique at a Black Hat security conference held in Las Vegas.
“The only thing you need for successful attacks are either the electrical grid or a distant line of sight, no expensive piece of equipment is required,” – Barisani and Bianco while describing their hacks.

When you are using your computer keyboard, every key input generates a voltage signal, and those signals can be captured by hackers using a voltmeter. Since the computer keyboards have an unshielded wire so those signals leak into the ground wire of the computer’s main power cable. The voltmeter captures the bit streams and voltage fluctuations generated by keyboards and finds out what keys you are hitting.
The second hacking method is a laser. The hacker points a ray of the laser at a shiny object located on your computer table or a shiny part of your laptop, then the hacker aligns the receiver to record the vibrations being caused by each keystroke, which is reflected through the light beam.
According to the Network World:
“The equipment to carry out the power-line attack could cost as little as $500, and the laser attack gear costs about $100 if the attacker already owns a laptop with a sound card. Carrying out the attacks took about a week.”
6. Radio Signals and Mobile Phones Can Intercept Confidential Data
Keyboard interception, in most cases, isn’t very useful because of the obvious reasons. One can never use keyboard keystrokes to gain access to the data stored within the computer system.
However, according to the Kaspersky Lab, some external methods can be used to infect the computer with malware that isn’t even connected to the internet. That is exactly how the famous Stuxnet worm infected the targeted computer which was placed within the uranium enriched infrastructure. Once the computer was infected, the malware worked in a similar way just like some internal spy, leaking confidential data through a certain physical medium.
On the other hand, Israeli researchers have developed an eavesdropping software that modulates electromagnetic radio signals released by different computer hardware. These signals are so strong that it can be received by a simple FM receiver of your mobile phone.
A computer that stores confidential data are usually placed inside a well-shielded room and are completely isolated from the external networks, these precautionary steps are taken to eliminate any possible data leakage. But hackers can use software like these, despite all the isolation, to access the protected data.
7. Heat Generated By Your Computer
The Israeli researcher team from Ben Gurion University has revealed that how hackers can steal data from your computer by only using heat emissions. They have found a way to eavesdrop on the air-gapped computer using the computer’s built-in thermal sensors and heat discharge.
This unusual method will allow hackers to secretly spy onto the security keys and passwords stored on the protected computer and then transmit the data to the computer, which is connected to the Internet, located in the close proximity, and is in the control of the hacker.
Additionally, the same computer which is connected to the Internet can be used to transfer malicious programs to the air-gapped computer using a thermal method. It is obvious that this means of eavesdropping is very sluggish and cannot be used to transfer a large amount of data, but no doubt, it is effective.
Kaspersky Labs, while explaining the working of this hacking method:
“The malware reads classified data and periodically changes the system temperature by adjusting the load level and producing a modulated heat signal. The second computer reads and decodes it and sends the classified data over the Internet.”
8. Data Can Be Accessed Through Thick, Solid Steel Obstructions
Your computer stored within a well-isolated chamber does not provide assurance against complete data leakage protection because ultrasound technology can easily allow sensitive data to pass-through.
Tristan Lawry, a doctoral candidate in Electrical and Computer Engineering, has developed spy equipment which can transfer data at high rates even through thick, solid steel obstructions. And, what’s more, interesting about this equipment apart from transferring data is that it can also transmit power.
This spying kit is a secretive technology, actually being used by the British Intelligence services, but has been reinvented by the graduate of the American-based university.
According to the Kaspersky Lab:
“ spy equipment is represented in two compact units. One unit is inconspicuously placed inside of the classified room, while the other is placed somewhere outside of it. The data transfer rate through steel for ultrasound reaches up to 12 MB/s.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.

