The cybersecurity researchers at Kaspersky have unveiled alarming statistics about the expanding cybercrime economy on the dark web.
Key Findings:
- DDoS Demand Soars: Kaspersky’s analysts discovered over 700 dark web ads for DDoS attack services in H1 2023, highlighting the escalating demand among hackers.
- Cost of DDoS Services: Rates for DDoS attack services on the dark web ranged from $20 per day to $10,000 per month, with an average cost of $63.50 per day or $1,350 per month.
- IoT Malware Evolution: Fierce competition among cybercriminals has driven the development of IoT malware, with features designed to thwart rival malware, including firewall rules and process terminations.
- Brute-Force Attacks Prevalent: Brute-forcing weak passwords remains the primary method for compromising IoT devices, with 97.91% of attacks focusing on Telnet, compared to 2.09% on SSH.
- Global Attack Landscape: While China, India, and the United States were the primary targets of IoT attacks, China, Pakistan, and Russia emerged as the most active attackers, highlighting the global reach of cyber threats.
The Internet of Things (IoT) landscape is under siege, with a growing underground economy centered around IoT-related services, particularly for Distributed Denial of Service (DDoS) attacks, according to a recent report by cybersecurity firm Kaspersky.
The study delves into the evolving threats targeting the IoT sector, shedding light on the modus operandi of cybercriminals and the alarming prevalence of malware types.
IoT devices are poised to surpass a staggering 29 billion by 2030, making them an attractive target for cybercriminals. Kaspersky’s research presents crucial insights into dark web activities, prevalent malware strains, and the tactics employed by hackers.
While DDoS protection and mitigation services are utilizing all available resources to secure their clients’ infrastructure; DDoS attacks orchestrated through IoT botnets are experiencing a surge in demand within the cybercriminal community. Kaspersky’s Digital Footprint Intelligence service analysts unearthed over 700 ads for DDoS attack services on various dark web forums in the first half of 2023.
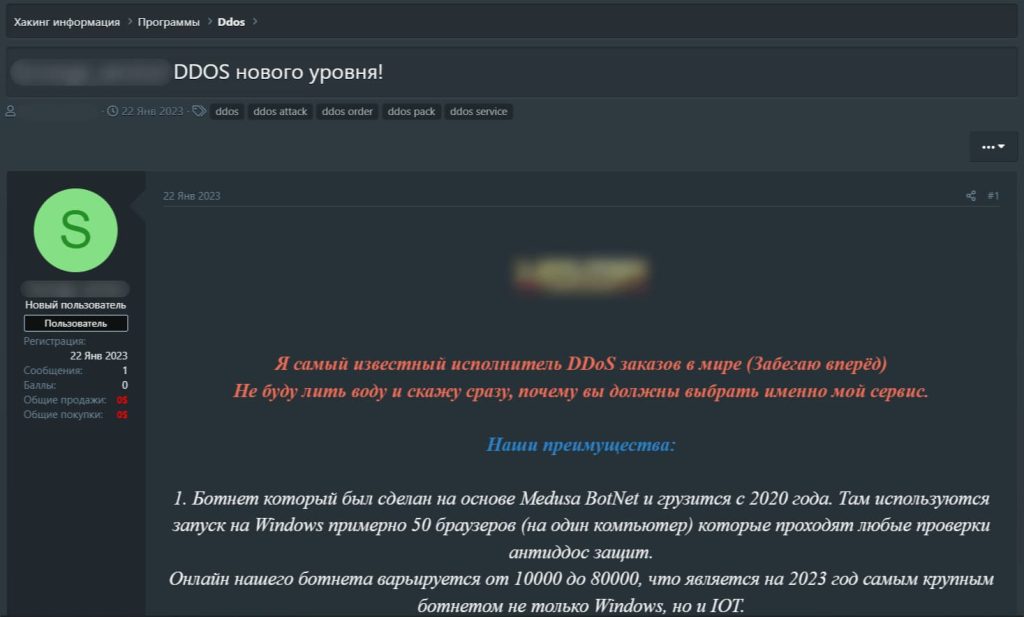
The cost of these services varies depending on factors such as DDoS protection, CAPTCHA, and JavaScript verification on the victim’s side, ranging from $20 per day to $10,000 per month. On average, these illicit services were offered at a rate of $63.50 per day or $1,350 per month.
Furthermore, the dark web marketplace isn’t just limited to DDoS services. It offers zero-day exploits for vulnerabilities in IoT devices, bundled with infrastructure and supporting utilities.
IoT malware, which comes in various families, has a history rooted in the 2016 Mirai malware. Fierce competition among cybercriminals has prompted the development of features designed to outwit rival malware. These strategies include the implementation of firewall rules, disabling remote device management, and terminating processes linked to competing malware.
The primary method employed by cybercriminals to compromise IoT devices remains brute-forcing weak passwords, followed closely by exploiting vulnerabilities in network services. Brute-force attacks primarily target Telnet, a widely used unencrypted protocol. Hackers crack passwords to gain unauthorized access, allowing them to execute arbitrary commands and deploy malware. While SSH, a more secure protocol, is also susceptible, it poses a greater resource challenge for attackers.
In the first half of 2023, Kaspersky’s honeypots recorded that a staggering 97.91% of password brute-force attempts focused on Telnet, with a mere 2.09% directed at SSH. The majority of these attacks were concentrated in China, India, and the United States, while China, Pakistan, and Russia emerged as the most active attackers.
Exploiting vulnerabilities in IoT web interfaces is another avenue for attacks on IoT devices. Cybercriminals execute malicious commands through these vulnerabilities, leading to severe consequences such as the proliferation of malware like Mirai.
Yaroslav Shmelev, a security expert at Kaspersky, issued a stern warning: “Kaspersky urges vendors to prioritize cybersecurity in both consumer and industrial IoT devices. We believe that they must make changing default passwords on IoT devices mandatory and consistently release patches to fix vulnerabilities.”
“In a nutshell, the IoT world is filled with cyber dangers, including DDoS attacks, ransomware, and security issues in both smart home and industrial devices. Kaspersky’s report stresses the need for a responsible approach to IoT security, obliging vendors to enhance product security from the get-go and proactively protect users,” Yaroslav added.
To provide further insights, the Kaspersky report details several types of IoT malware, including DDoS botnets, ransomware, miners, DNS changers, and proxy bots. Each of these malicious programs serves distinct purposes, adding to the complexity of IoT security challenges.
In conclusion, Kaspersky’s research paints a harsh picture of the IoT threat landscape for 2023. As the number of IoT devices continues to skyrocket, cybersecurity becomes paramount. Cybercriminals are relentless in their pursuit, and only a concerted effort by both manufacturers and consumers can safeguard the future of the IoT.
By conducting regular security audits, monitoring network traffic, and following best practices, stakeholders can take meaningful steps to secure this rapidly evolving ecosystem.
