Scarred Manticore is targeting high-profile organizations focusing keenly on telecommunication, military, and government entities apart from financial institutions, IT service providers, and NGOs.
Check Point Research (CPR) and Sygnia’s Incident Response Team have uncovered a new Iranian espionage campaign they have tied to the notorious Scarred Manticore threat group.
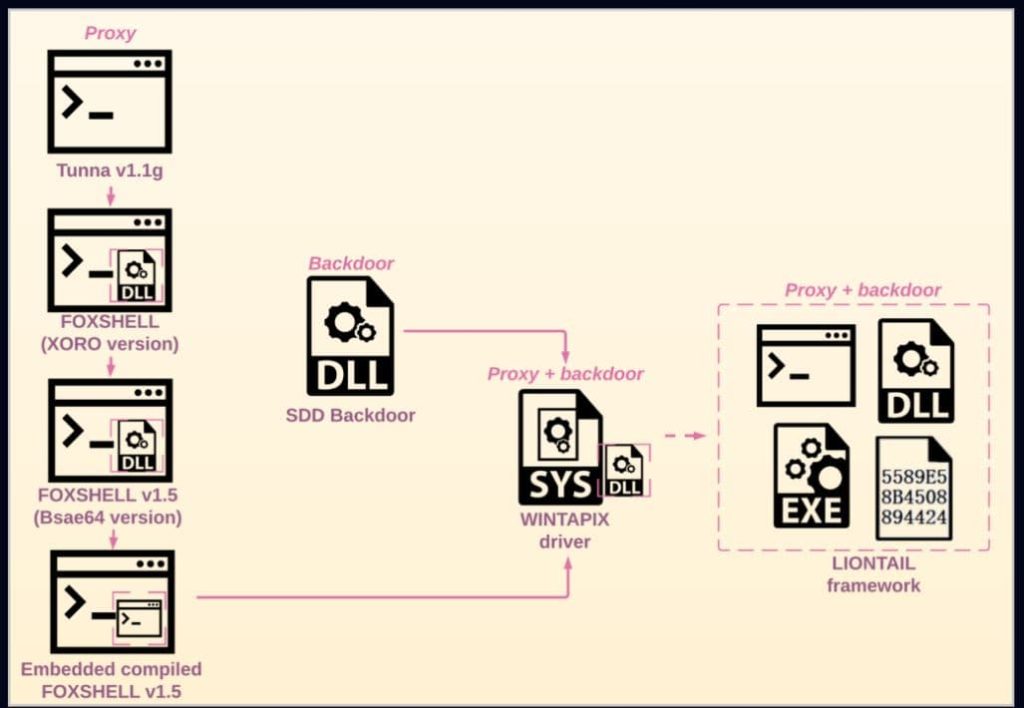
In its technical report titled “From Albanian to the Middle East: The Scarred Manticore is Listening,” it is revealed that the group is using a previously undocumented malware framework called LIONTAIL. This malware uses custom loaders and memory-resident shellcode payloads to blend its malicious functionalities into legitimate network traffic.
Researchers believe that the primary goal behind this campaign is espionage. This threat actor is among the Iranian actors involved in destructive cyberattacks against the Albanian government infrastructure at the behest of MOIS (Ministry of Intelligence & Security) back in July 2022. CPR claims that this threat group has been active since at least 2019, prefers gaining covert access, and persistently pursues data extraction.
Further probing revealed that Scarred Manticore is targeting high-profile organizations in the Middle East in this ongoing espionage campaign, focusing keenly on telecommunication, military, and government entities apart from financial institutions, IT service providers, and NGOs.
Though the LIONTAIL framework appears unique with no code overlaps with any known malware family detected thus far, the other tools used in the attacks overlap with previously reported attacks. Some of these attacks are linked to the OilRig or OilRig-affiliated clusters but there’s insufficient evidence to link the Scarred Manticore group with OilRig.
Since 2019, this group has been using a custom toolset to compromise internet-exposed Windows servers in the Middle East. In this particular campaign, CPR has uncovered, that the victims are located in Saudi Arabia, the UAE, Kuwait, Jordan, Iraq, Oman, and Israel.
The geographic regions targeted in this campaign and Scarred Manticore’s previous activities sharply align with Iranian interests and with the typical victim profile targeted by MOIS-sponsored groups in espionage operations.
Scarred Manticore’s toolset has evolved considerably over time as from open-source web-based proxies, they gradually switched to powerful tools combining open-source and custom components. The Tunna-based web shell is one of the group’s earliest tools, an open-source tool used to tunnel TCP communications over HTTP to let attackers connect to any service on the remote host, even those blocked by firewalls.
This actor now uses a range of IIS-based backdoors to target Windows servers, including custom web shells, custom DLL backdoors, and driver-based implants. The custom malware framework LIONTAIL, which CPR dubbed ‘digital chameleon,’ can establish persistence on compromised systems and steal sensitive data without being detected. It uses custom loaders and special codes to remain in the computer’s memory and hijacks the HTTP.sys driver to become a part of the regular network activity.
The evolution in Scarred Manticore’s tools and capabilities demonstrates the progress Iranian threat actors have undergone within the past few years because the techniques used in recent campaigns are far more sophisticated than previous ones tied to Iran.
RELATED ARTICLES
- Iran-linked hackers hit Israeli, US and EU defence tech firm
- GhostSec Claim Breaching Iranian Govt Surveillance Software Tool
- Iranian Hackers Posed as Israelis in Targeted LinkedIn Phishing Attack
- Iranian Stalkerware ‘Spyhide’ Steals Data from 60,000 Android Devices
- Ransom fail: Iranian hackers leak trove of Israeli LGBTQ dating app data
- Log4Shell – Iranian Hackers Accessed Domain Controller of US Federal Network