ESET warns that Deadglyph is a highly sophisticated backdoor that is mixed with different programming languages to add an extra layer of complexity.
The Middle East has once again found itself in the crosshairs of a new cybersecurity threat. Recent findings by experts at ESET Research have unveiled a highly sophisticated and previously unknown cyber-espionage tool they’ve dubbed “Deadglyph.”
This discovery is a significant development in the world of cybersecurity, as it’s the first time this secretive threat has been publicly analyzed. Even more concerning, Deadglyph has been traced back to the Stealth Falcon APT group, notorious for its cyber-espionage campaigns in the Middle East.
What is Deadglyph?
Deadglyph gets its name from distinctive artifacts found within the malicious software. These artifacts, such as “0xDEADB001,” and the use of homoglyph attacks (where similar-looking characters replace regular ones) indicate a high level of sophistication behind its design. It’s important to note that this isn’t your typical cyber threat; it’s a highly advanced and covert tool.
Unusual Architecture Raises Concerns
One of the standout features of Deadglyph is its unique architecture. Unlike most malware that relies on a single programming language, Deadglyph uses a combination of two: an x64 binary and a .NET assembly. This is quite unusual and suggests that the creators went to great lengths to make it harder to analyze. Mixing different programming languages also adds an extra layer of complexity.
What sets Deadglyph apart is that it doesn’t come with pre-set commands like traditional malware. Instead, it fetches its instructions from a remote server, giving it a flexible and adaptable nature.
The Stealth Falcon APT Group
The experts at ESET Research have connected Deadglyph to the Stealth Falcon APT group. This group has been active since 2012 and is believed to have ties to the United Arab Emirates. Its primary targets include political activists, journalists, and dissidents in the Middle East. The group’s activities were first exposed by Citizen Lab in 2016.
There are suggestions that Stealth Falcon and another group called Project Raven are one and the same, as they seem to have overlapping targets and tactics. The revelation of Deadglyph adds another layer of complexity to this enigmatic group’s toolkit.
Breaking Down Deadglyph’s Operation
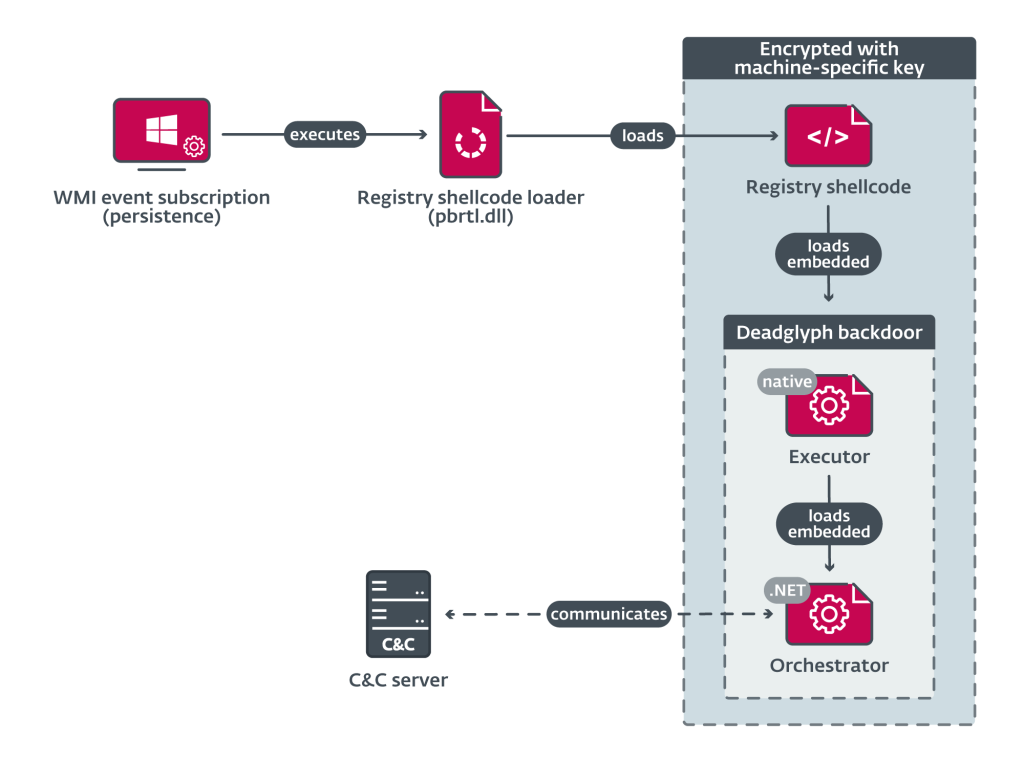
Deadglyph’s operation is a complex chain of events. It starts with a registry shellcode loader that’s used to load shellcode from the Windows registry. This shellcode, in turn, loads the main part of Deadglyph, known as the Executor. What’s unique is that only the initial loader exists as a file on the victim’s computer; the rest remains encrypted within a registry entry.
While the exact method of infection isn’t clear, it’s suspected that an installer component plays a role in getting the malicious code onto a victim’s system.
The Role of the Orchestrator
The Orchestrator, written in .NET, is the central component of Deadglyph. Its primary job is to communicate with a remote server and execute commands, often with the help of the Executor. The Orchestrator is highly obfuscated, making it even more challenging to analyze. In essence, it acts as the control center for Deadglyph’s operations.
Communication and Commands
According to ESET’s report, Deadglyph uses two embedded modules, Timer and Network, for communication with its remote server. These modules are obfuscated as well. The Timer module executes tasks at set intervals, while the Network module handles communication with the server. Deadglyph also has the ability to uninstall itself if it loses contact with the server for an extended period.
Modules: The Heart of Deadglyph
Deadglyph’s core capabilities are delivered through additional modules obtained from the server. ESET researchers managed to obtain three such modules, shedding light on Deadglyph’s potential. However, it’s believed that there could be as many as fourteen modules in total, each adding unique functionality.
- Process Creator (Module 0x69): This module can execute specific commands as new processes and provide the results back to Deadglyph’s control center.
- Info Collector (Module 0x6C): This module gathers extensive information about the infected system, including operating system details, installed software, network adapters, and more.
- File Reader (Module 0x64): This module reads specified files and shares their contents, with an option to delete the files afterward.
Multistage Shellcode Downloader Chain
While investigating Deadglyph, ESET researchers stumbled upon a complex multistage shellcode downloader chain. This chain is believed to be used in the installation process of Deadglyph and shares similarities with the main threat.
The chain involves multiple stages, starting with a CPL file designed to download shellcode. This shellcode is then injected into a host process, ultimately leading to the loading of a .NET assembly that serves as a shellcode downloader.
In Conclusion: A Disturbingly Complex Threat
The discovery of Deadglyph shines a spotlight on the ever-evolving tactics of APT groups, particularly those targeting the Middle East. Its intricate architecture, dynamic modules, and counter-detection mechanisms make it a formidable digital threat. Organizations and individuals in the region need to remain vigilant and ensure their cybersecurity measures are up to the task of defending against such advanced threats.
RELATED ARTICLES
Chinese APT Flax Typhoon uses legit tools for cyber espionage
Chinese APT Slid Fake Signal, Telegram Apps onto Official App Stores