LummaC2 v4.0, an advanced malware, steals data and evades detection by employing trigonometry to distinguish human users from automated analysis tools.
Security assessment platform provider Outpost24’s threat intelligence team KrakenLabs has uncovered a new technique that malware developers are using to evade detection in sandbox environments.
This technique involves using trigonometry to analyze cursor movements and detect human behaviour, thus enabling the malware to distinguish between real users and automated analysis tools.
In the company’s blog post, researchers noted that an information stealer, LummaC2 v4.0, uses this new anti-sandbox technique to avoid detonation if it doesn’t detect human mouse activity.
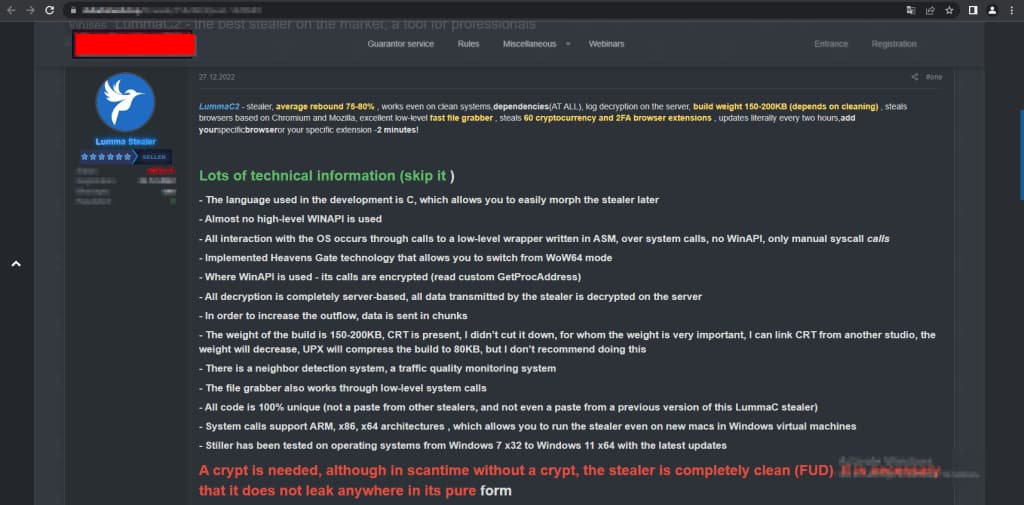
LummaC2 v4.0 is written in C language. This infostealer has undergone significant updates since it was released in December 2022, including the implementation of Control Flow Flattening obfuscation (which makes code difficult to understand/analyze), strings encryption using XOR instead of adding junk strings (to make it harder to reverse engineer the malware or understand its functionality), and the anti-sandbox technique (that delays the malware’s execution until detecting mouse activity).
LummaC2 v4.0 also supports dynamic configuration files extracted from its C2 server to receive instructions on adapting to different situations. It uses a crypter for all builds, which adds a new layer of protection to the malware. These changes indicate that malware developers are focusing on evading detection and analysis.
Researchers identified that LummaC2 v4.0 stealer uses trigonometry to assess cursor movements to detect human behaviour before activation. This is a novel anti-sandbox technique in which the malware captures the cursor’s initial position using the GetCursorPos() function and waits for 300 milliseconds to check for cursor movements.
If the position changes, the malware captures five additional positions with a delay of 50 milliseconds between each capture. It then ensures that each captured position is different from its preceding one.
This prevents the malware from activating itself in sandbox environments as these mimic static cursor positions. Trigonometric calculations allow the malware to analyze the captured cursor positions and detect patterns of human behaviour, etc.
Moreover, the threat actor selling LummaC2 v4.0 discourages distributing unaltered malware samples to maintain control over its usage and avoid widespread detection.
Anti-analysis techniques have become a persistent threat to cybersecurity, and this novel anti-sandbox technique poses a significant challenge for security analysis tools because it targets the limitations of automated mouse emulation.
Organizations should implement robust sandboxing solutions and employ advanced analysis techniques to detect/analyze obfuscated malware like LummaC2 v4.0 effectively.