DoubleLocker Android Ransomware Encrypts Data and Changes PIN to Permanently Lock Your Phone.
ESET’s security researchers have identified a new kind of ransomware, which infects Android devices by using a technique that so far was used by Trojans. It not only encrypts your mobile phone but also modified its PIN.
The ransomware has been named DoubleLocker because it performs a two-way action to lock the phone, that is, it encrypts all the files and changes the PIN as well so that victims run out of options and give in to the ransom demands of hackers. The ransomware is being distributed as a fake update of Adobe Flash while compromised websites are being used to spread it.
When DoubleLocker is downloaded on your device, the fake Adobe Flash app requests for Google Play Services activation because it needs to exploit the phone’s accessibility services. This particular option is present for disable people so that they could easily use their phones.
It must be noted that the tactic of abusing accessibility services was used previously by Android data-stealing Trojans and it is the very first time that some cybercriminals have employed this approach on ransomware.
DoubleLocker then starts exploiting the permissions by retrieving Windows content, enabling advanced web accessibility for installation of scripts and monitoring the text that the victim types. When permissions are granted, the ransomware is installed as the default Home app. This means when the user will visit Home screen the next time the ransom note will be there.
According to ESET’s malware researcher Lukáš Štefanko, the default Home app is a launcher and is present to enhance the persistence of the malware. The user believes the malware to be default Android launcher, which is the software that controls the appearance of the device, as well as the way apps and widgets, are launched. It also is responsible for creating invisible shortcuts to self-activate when the victim clicks on Home button, and this is how the device gets locked. It happens every time the victim tries to use the mobile’s Home screen.
“Thanks to using the accessibility service, the user doesn’t know that they launched malware by hitting Home,” said Štefanko.
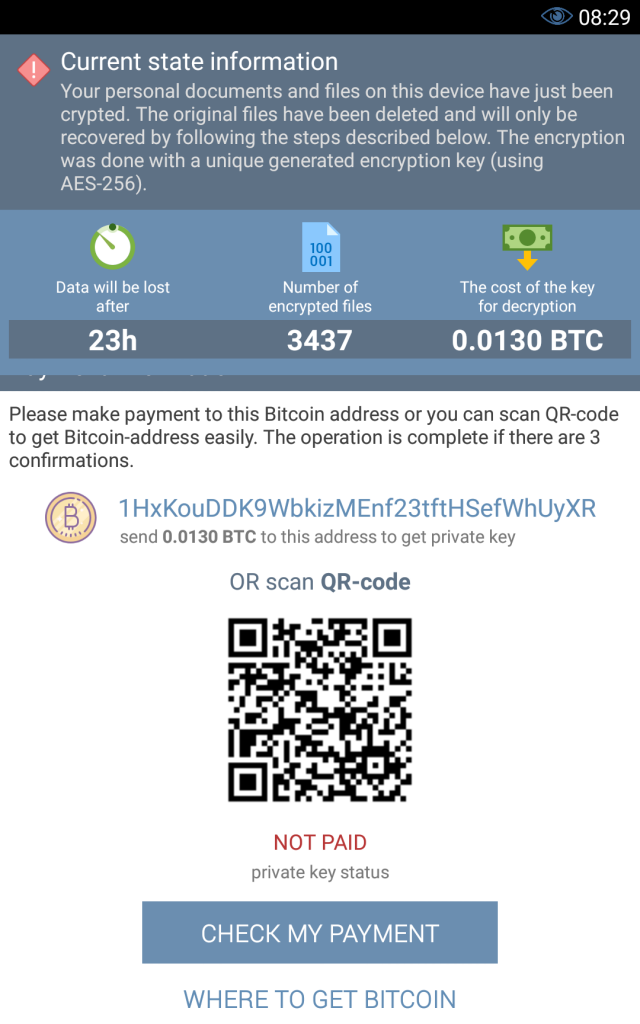
The two ways in which DoubleLocker attempts to lock the phone include encryption of the files stored on the device and changing the PIN of the device. It encrypts data using the AES encryption algorithm through “.cryeye” extension. The encryption is highly effective, and without the decryption key, it becomes impossible to unlock the files.
On the other hand, the PIN is changed effectively by setting it to a random number, which even the attackers do not store. This means, recovering access to the device is not possible. The PIN is then reset after the ransom has been paid and the device is unlocked. Attackers give 24 hours deadline to the victims for payment of ransom.
It is worth noting that hackers are demanding 0.0130 bitcoins (approx. $73) as ransom, which is a comparatively low figure if we observe what other ransomware schemes are demanding. However, it is quite possible that hackers have set the ransom amount low deliberately so that victims easily pay the ransom to regain access to their device.
The only option victims have if they don’t want to pay ransom amount, is to run factory reset. This will fully format the phone, and all the data that is not backed up will be permanently deleted. The chances that the rooted phone can successfully get past the PIN without needing to be reset are not bright. It can only happen if the device had to debug mode on before the installation of ransomware. In that case, it is possible to remove the system file through accessing Android Debug Bridge (ADB) as this is where the PIN is stored. This would allow the user to reset the device manually.
However, we suggest that it is better to avoid installing apps and software from third-party websites and only choose reliable, authentic platforms. DoubleLocker is a dangerous threat to all Android devices since it doesn’t need a rooted phone to run its code and it can effectively affect the phone rendering it useless unless the victim pays the ransom.
