PrivaTegrity communication network provides secure communication platform and Anonymity — Maybe better than Tor.
A new anonymous communication network by the name of PrivaTegrity has been launched by renowned encryption specialist David Chaum. The network achieves same connection speed as Tor but provides better protection against cryptanalysis techniques.
According to the encryption specialist, PrivaTegrity addresses as well as fixes some of the standing issues faced by The Onion Router, or Tor as it is commonly called. The issues that PrivaTegrity solves are both technical and legal.
PrivaTegrity uses the concept of Mix Network. Mix Network was used in David Chaum’s paper “cMix: Anonymization by High-Performance Scalable Mixing”. In this paper, Chaum modifies the concept of Mix Network to form his own concept, called cMix. His breakthrough cryptography protocol is now supposedly the thing that researchers will look to use in order to build their own PrivaTegrity networks.
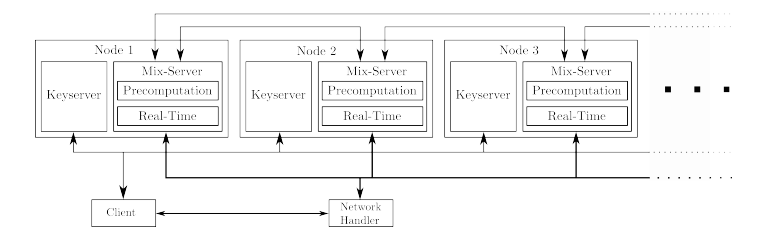
Chaum’s paper also addresses many issues that regular users as well as the government, had with the Mix Network. He believes that the use of cMix to make personal PrivaTegrity networks for organizations will become a good alternative to using Tor.
The way cMix works and why it is better is explained in Chaum’s paper. The basic idea behind it is this. First, the sender of the message establishes connections with a few trusted servers and shares a series of keys with them. When the message is initially sent by a sender, it is multiplied with all of the encryption keys.
When the message then passes through each subsequent server it is divided by that particular server’s key. The message is also multiplied by a random number upon being divided by a server’s key. Server’s buffer stores the message in a randomized way.
When retrieval and decryption are required, each server retrieves the message, divides it with the random number and then multiplies it with its key to get part of the message. Upon the message receiving on the recipient’s system, his or her keys are used to divide it and then decrypt the message.
PrivaTegrity solves the issue of tagging in Tor, which is a malicious user tagging an input node with its output location in a Tor network. The only way cMix can be breached is if a user compromises all the details, which is, according to Chaum, very rare.
EPrint chaum.comm00osfoto/Shutterstock
