Dubbed Firestarter by researchers; the Android malware campaign is exploiting the Kashmir issue between India and Pakistan but its target remains the Pakistani government, noted Cisco Talos researchers.
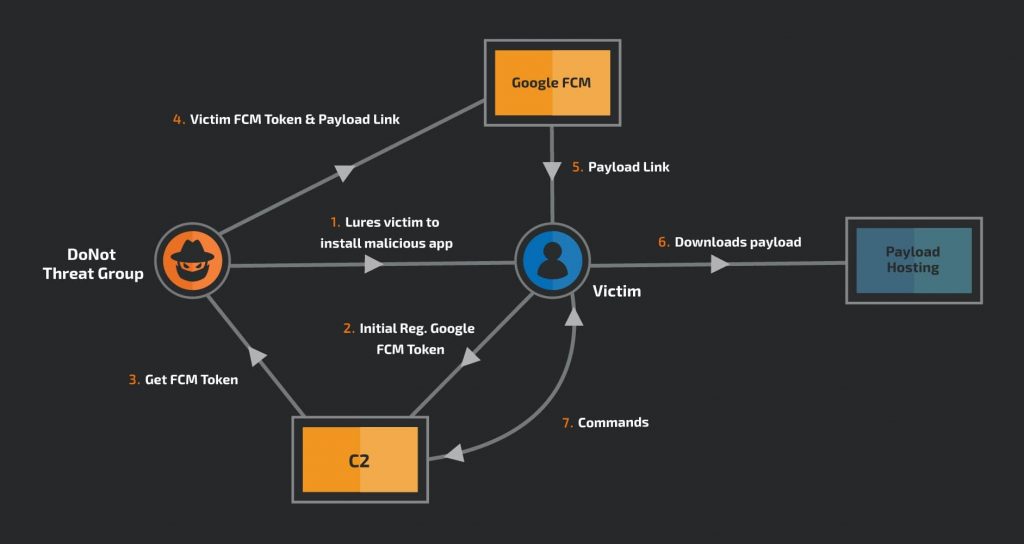
Cisco Talos researchers have discovered that the APT threat group DoNot exploits Google’s Cloud Messaging service to spread android malware and bypass detection. The malware is dubbed Firestarter, which is being spread via the Firebase Cloud Messaging (FCM).
FCM is a cross-platform cloud service designed for Android, Web, and iOS applications. The service is owned by Google’s subsidiary Firebase.
DoNot is using the FCM as a communication mechanism to connect with its C&C (command-and-control) servers for the primary purpose of evading detection.
See: Google Firebase misconfiguration exposes data of 20k+ Android users
Researchers noted in their blog that DoNot is “experimenting with new techniques to keep a foothold on their victim machines,” and the Firestarter loader is substantiating these experiments, which proves how dangerous this group is and how passionately they want their operations to succeed.
The primary focus of team DoNot remains on Pakistan and India. It mainly targets Pakistani government officials and non-profit organizations from the disputed Kashmir valley.
According to a blog post by the Cisco Talos research team, the apps used in this attack have filenames titled Kashmir_Voice_v4.8.apk or kashmir_sample.apk, which depicts their interest in the India, Pakistan, and Kashmir crisis.
Users are urged to install a malicious app that purports to be a chat medium on their mobiles through direct messages using social engineering. When the app is downloaded and installed, users are notified that chats are loading, and later they learn that the app isn’t supported therefore, the app will be uninstalled.
After the uninstallation message appears, the app’s icon is removed from the mobile’s user interface, but the app continues to appear in the phone’s application listing.
In the background, the app downloads a payload after communicating with its C&C server through FCM. Since the final payload isn’t embedded in the malicious application, it becomes impossible for the analysts to dissect it.
Cisco Talos researchers wrote that this approach makes detection difficult as “the application is a loader with a fake user interface that manipulates the target after installing it.”
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.