The OracleIV botnet malware employs various tactics, with a primary focus on executing DDoS attacks through UDP and SSL-based floods.
Cybersecurity researchers at Cado Security Labs have exposed a novel (Distributed Denial of Service) DDoS botnet malware dubbed OracleIV targeting publicly exposed Docker Engine API instances.
The findings were part of an investigation into a malicious campaign exploiting misconfigurations in Docker containers to deliver Python malware, compiled as an ELF executable.
Lately, Docker Engine APIs have been frequent targets of cybercriminals since the method has gained popularity due to the increasing adoption of microservice-driven architectures. Attackers exploit the unintentional exposure of the Docker Engine API, often scanning for vulnerable instances to deliver payloads with nefarious objectives.
In the case of the new OracleIV DDoS botnet malware, the attackers initiate access with an HTTP POST request to Docker’s API, specifically the /images/create endpoint. This triggers a docker pull command, fetching a specified image from Dockerhub. Once the malicious image is retrieved, a container is launched to carry out the attacker’s objectives.
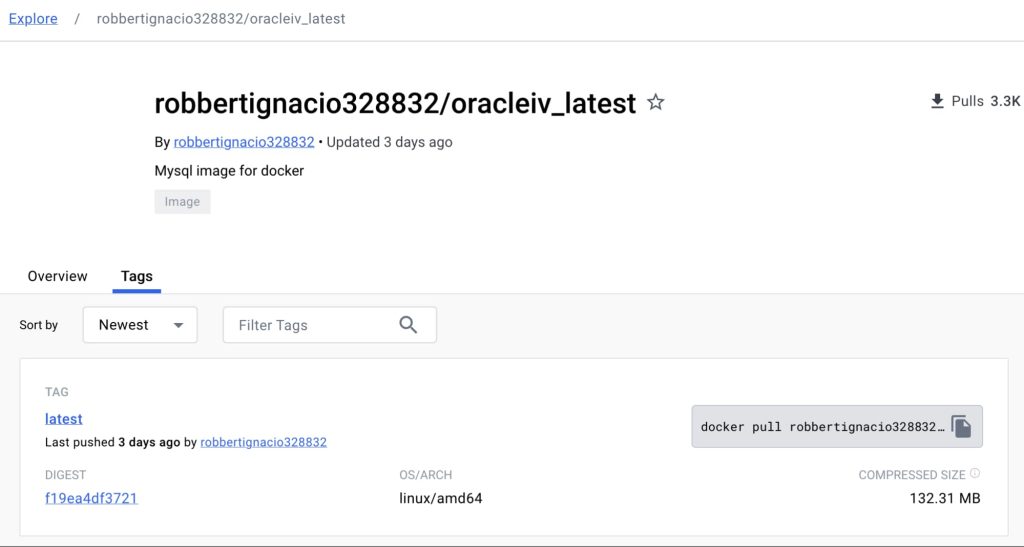
Cado Security researchers uncovered a live Dockerhub page for an image named “oracleiv_latest” uploaded by the user “robbertignacio328832.” The image, seemingly harmless as a “Mysql image for docker,” included a malicious payload named “oracle.sh,” an ELF executable acting as a DDoS bot agent. Further analysis revealed additional commands to retrieve XMRig and a miner configuration file.
Static analysis of the executable exposed a 64-bit ELF compiled with Cython, confirming the OracleIV malware’s Python code origin. The malware code, succinct yet potent, contains various functions dedicated to different DDoS methods.
“This image was still live at the time of writing and had over 3,000 pulls,” researchers explained in a blog post. Additionally, it seems to be undergoing frequent updates, with the latest modifications pushed just three days prior to the publication of Cado’s blog.
The bot connects to a Command and Control server (C2), performing basic authentication with a hardcoded password. Cado Security Labs monitored the botnet’s activity, witnessing DDoS attacks on various targets, primarily using UDP and SSL-based floods.
The C2 commands for initiating DDoS attacks follow a specific format, specifying attack type, target IP/domain, attack duration, rate, and target port. The botnet’s capabilities include UDP floods, SSL-based attacks, SYN floods, slowloris-style attacks, and protocol-specific floods targeting the FiveM server and Valve source engine.
While OracleIV is not a supply chain attack, it highlights the ongoing threat of misconfigured Docker Engine API deployments. The portability of containerization enables attackers to execute malicious payloads consistently across Docker hosts.
Although Cado Security has reported the malicious user to Docker, users are urged to conduct periodic assessments of pulled images from Dockerhub, emphasizing the need for vigilance against malicious code.
In conclusion, the OracleIV campaign highlights the importance of securing internet-facing services and implementing strong network defences. Users of Docker and similar services are encouraged to regularly review their exposure and take necessary precautions against potential cybersecurity threats.
RELATED ARTICLES
- SSH Remains Most Targeted Service in Cado’s Cloud Threat Report
- Change your password: Docker suffers breach; 190k users affected
- Hackers Exploit Adobe ColdFusion Vulnerabilities to Deploy Malware
- Cryptomining and Malware Flourish on Misconfigured Kubernetes Clusters
- ShellTorch Attack Exposes Millions of PyTorch Systems to RCE Vulnerabilities