Ragnar Locker ransomware gang has attacked multiple firms recently, but now it has taken extortion to the next level.
The infamous Ragnar Locker ransomware gang is now running Facebook advertisements to pressurize its victims into paying a ransom.
The gang attacked an Italian liquor firm Davide Campari-Milano S.p.A, also known as Campari Group, and stole 2 TB of encrypted data before encrypting their network. In exchange for the decryption key, they demanded a $15 million ransom.
The Ragnar Locker ransomware group has come up with a unique strategy to pressurize its victims into paying the ransom. The group is creating Facebook ads to promote their latest attack on Campari Group. The ad campaign was identified on November 9.
This group has been making headlines in recent months for targeting firms with a ransomware attack. However, this time their modus operandi is different as it is using Facebook Inc. accounts for running ads so that Campari pays the ransom.
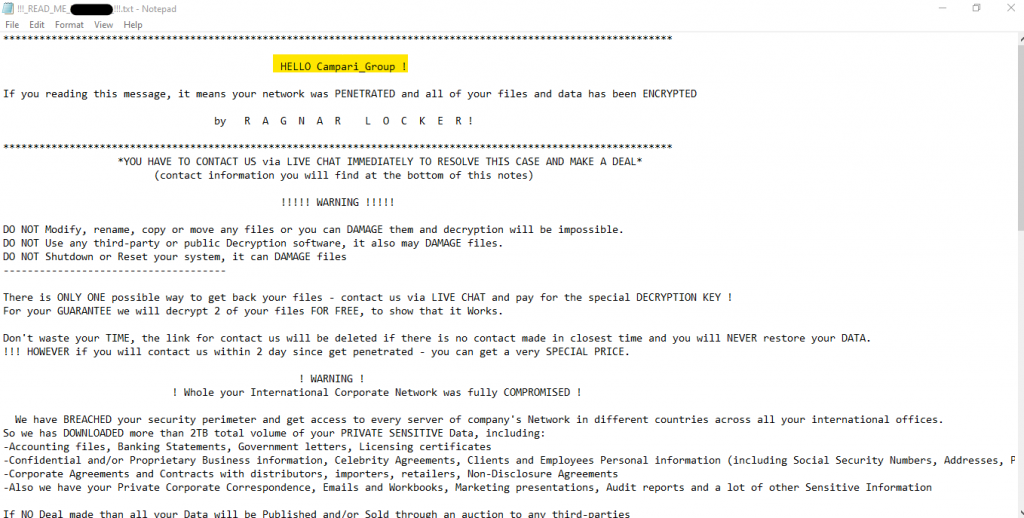
On Nov 3, Campari Group acknowledged that its computer systems were targeted with a malware attack. On Nov 6, the Italian drink maker issued another statement revealing that there is a possibility that some private and business data was stolen. To which the ransomware gang responded by posting ads on Facebook accounts. The ad read:
“This is ridiculous and looks like a big fat lie. We can confirm that confidential data was stolen and we talking about a huge volume of data.”
The ad further revealed that the gang offloaded 2 TB of information. They gave Campari Group time until 6 p.m. EST for negotiating the ransom payment in exchange for preventing the stolen data from getting published online.
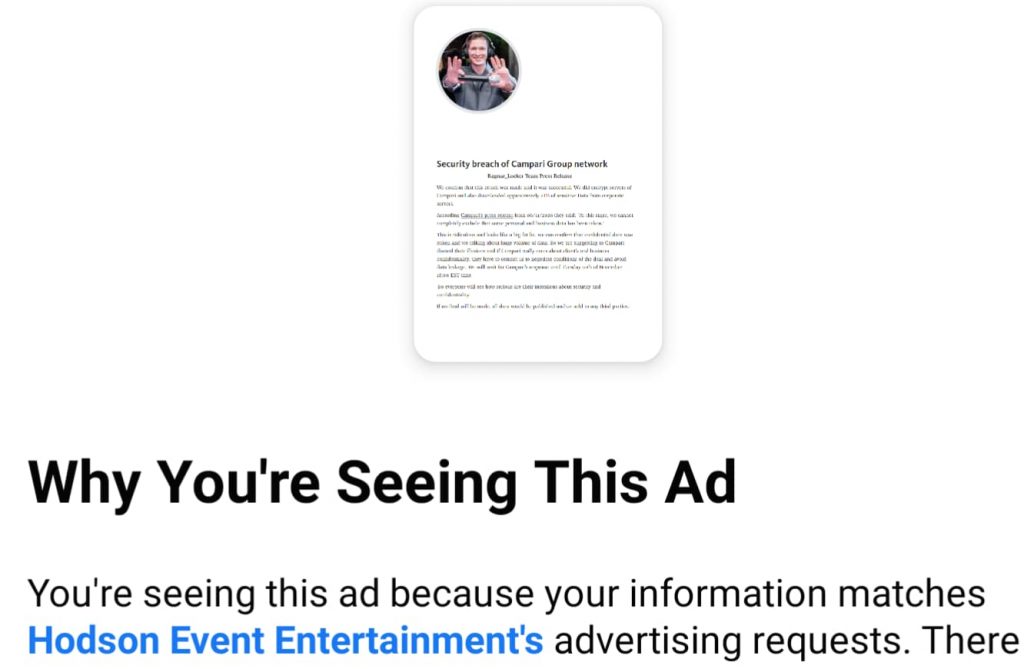
The Facebook advertisements were paid for by Hodson Event Entertainment. The account through which the ad blitz was posted was linked to Chris Hodson.
According to journalist Brian Krebs who initially reported the incident, Hodson is a Chicago-based deejay. When contacted by Krebs, Hodson claimed that his Facebook account was hacked and the attackers budgeted $500 for this campaign.
“I thought I had two-step verification turned on for all my accounts, but now it looks like the only one I didn’t have it set for was Facebook,” Hodson stated.
Hodson reviewed his Facebook account and learned that the campaign reached around 7,150 users on Facebook, generated 770 clicks, which cost 21 cents per result. However, instead of the attackers, Facebook billed Hodson $35 for the campaign’s first part.
The social network detected the fraudulent nature of the ads later and didn’t bill Hodson the entire amount of the campaign, which could have been $159.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.