Update – September 26th, 2023 – Sony has confirmed to Hackread.com that the company is aware of the claims made by the RANSOMEDVC ransomware group and is currently investigating them. The company has no further comment at this time.
It is essential to note that these claims by the RANSOMEDVC ransomware gang remain unverified at this point.
The infamous RANSOMEDVC ransomware group claimed to have successfully breached Sony Group Corporation, the Japanese multinational conglomerate giant. This claim was made through listings on both its clearnet and dark web platforms, where the group declared its complete infiltration of all Sony systems.
The ransomware group proclaimed that it had “successfully compromised all of Sony’s systems.” Distinct from the typical ransomware approach of locking the victim’s system, disrupting IT operations, and demanding a ransom for the decryption key, the RANSOMEDVC ransomware group has taken a different method. Instead of ransom demands, the group has declared its intention to monetize the stolen data, citing Sony’s alleged reluctance to comply with their demands.
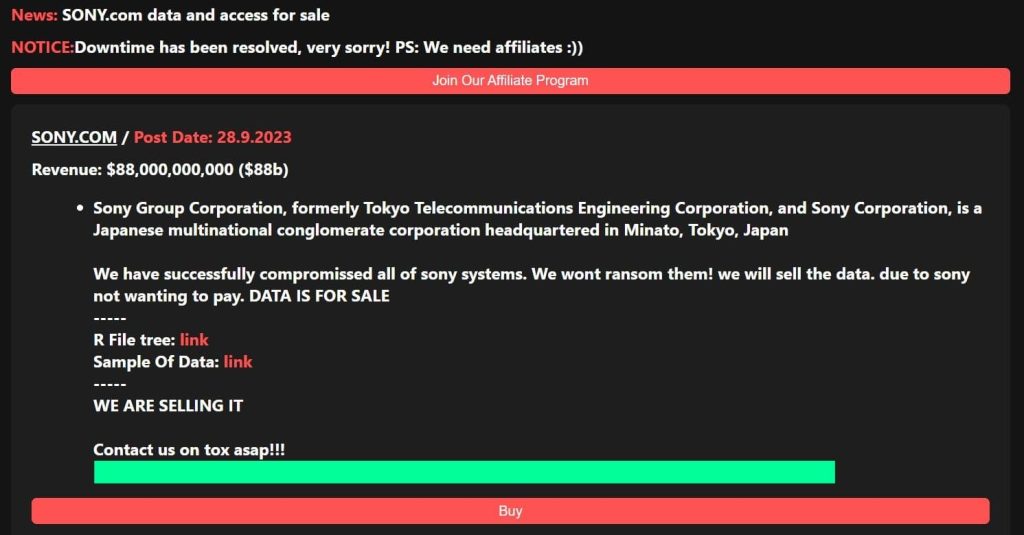
An analysis of the sample data published by RANSOMEDVC on its websites reveals limited insights. Among the leaked files are a PowerPoint Presentation purportedly from Sony’s Quality Assurance Division, internal screenshots displaying what seems to be a Sony workstation, Java files, and more.
It is essential to note that these claims by the RANSOMEDVC ransomware gang remain unverified at this point. Hackread.com has initiated contact with Sony to request an official statement regarding these allegations.
For context, the RANSOMEDVC ransomware group has been operational since at least 2023. They have gained fame for their aggressive tactics, which involve threatening victims with the release of sensitive data if the ransom demands are not met.
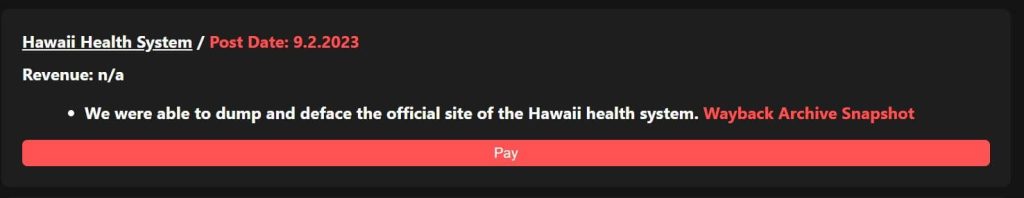
Notably, the RANSOMEDVC gang has been linked to several high-profile cyberattacks, including an assault on the Hawaiian government’s website in September 2023. Their targets span diverse sectors, encompassing healthcare, finance, and technology.
The claims made by the RANSOMEDVC ransomware group come mere days following a joint advisory from the FBI and CISA concerning the threats posed by another group known as Snatch Ransomware. This underscores the escalating and widespread nature of the ransomware threat.
On the contrary, Sony has proven to be a lucrative target for cybercriminals due to its worldwide popularity and a user base spanning the globe. Sony has previously fallen victim to a significant and wide-ranging data breach, during which hackers exposed the salary information and personal data of Sony Group’s executives and employees.
In February 2021, the U.S. authorities charged three North Korean hackers in connection with a series of cyberattacks, including their involvement in the hack of Sony Pictures.
Nevertheless, the emergence of the RANSOMEDVC gang underscores the pervasive threat of ransomware to organizations of all sizes. As such, it is imperative for businesses to establish comprehensive cybersecurity strategies to shield themselves from such attacks.