Currently, the primary target of the new Roaming Mantis malware is users in South Korea, but Kaspersky cybersecurity researchers suspect its scope will be expanded soon.
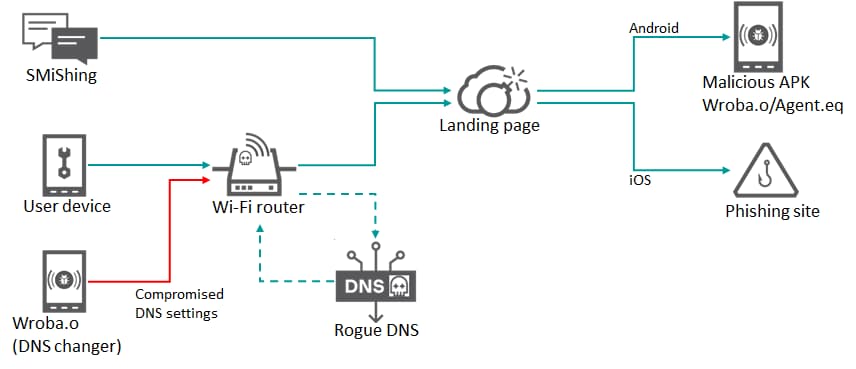
According to a report from Kaspersky Labs, the infamous Roaming Mantis attack campaign, aka Shaoye has resurfaced with a brand-new scheme. As previously reported by Hackread.com, Roaming Mantis operators use DNS changer functionality to abuse compromised public WiFi routers.
The objective is to infect a large number of Android smartphones with Wroba.o mobile malware (also called Agent.eq, Moqhao, XLoader). The prominent target of this campaign is users in South Korea. However, Kaspersky cybersecurity researchers suspect its scope to be expanded soon.
Threat Analysis
Researchers explained that the Roaming Mantis attackers are delivering a revamped version of their patent mobile malware Wroba for infiltrating WiFi routers and hijacking Domain Name System/DNS.
This malicious new attack is designed to specifically target South Korean WiFi routers manufactured by one of the leading network equipment vendors in South Korea.
The campaign recently introduced a DNS changer functionality in its mobile malware. DNS changer is a malicious attack technique that forces a device connected to an infected WiFi router to be directed to an attacker-controlled server instead of a genuine DNS server.
The victim is asked to download malware that steals credentials or hijacks the device on this malicious landing page. Around 508 malicious APK downloads were observed by Kaspersky in December 2022.
How does the Attack Works?
The new DNS changer functionality first detects the router’s IP address to check its model and compromises the targeted devices by overwriting the DNS settings. Some compromised devices leverage WiFi routers to take users to a fake landing page through DNS hijacking to redirect targets to bogus sites.
Regardless of which method is used, the invasion allows the attackers to deploy mobile malware that carries out a range of malicious activities. Kaspersky researcher Suguru Ishimaru stated that this new functionality could manage all device communications via the infected router, like redirecting to malicious hosts and disabling security product updates.
About Roaming Mantis
For your information, Roaming Mantis is a financially motivated, long-running cybercrime campaign in which attackers target Android smartphones and infect them with malware to steal banking credentials and sensitive data. The campaign was first observed in April 2018 by Kaspersky when it used DNS hijacking to infect Android smartphones and hijack data.
It used malicious APK (Android package) files to gain control of infected Android devices and steal data. However, a phishing option is available for iOS devices and PCs equipped with cryptocurrency mining features. From Asian targets, the cyber crooks running this campaign expanded their range to France and Germany in 2022.
How to stay Protected?
You can protect your internet connection from the infection by referring to your router’s user manual to verify whether your DNS settings have been tampered with or contact your ISP. Update your default login/password for the router’s admin web interface and regularly update its firmware from the official source. Check browser and web addresses before visiting to make sure they are legitimate, and before entering data, check the address.
RELATED NEWS
- Facebook removes accounts for iOS, Android malware
- Shazam Flaw exposed Android and iOS users’ location
- Android sends more data to Google than iOS to Apple
- Spyware Vendor Offer Android and iOS Device Exploits
- How to identify malware on your phone with these signs