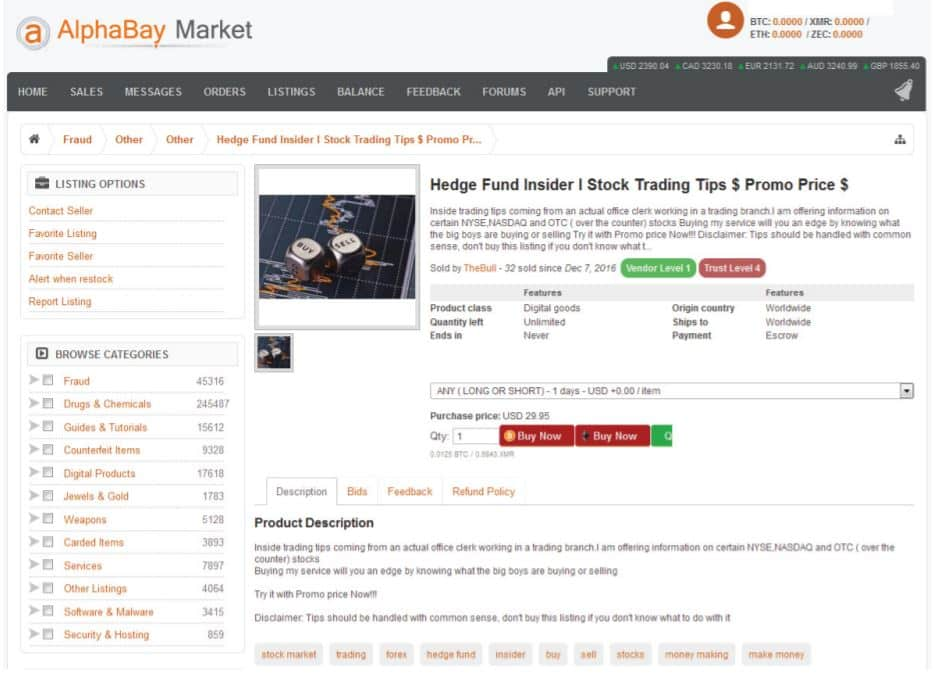
The accused is a Greek national who used AlphaBay marketplace with the alias “The Bull” on the dark web for insider trading information.
The Securities and Exchange Commission charged a 30-year-old Greek national, Apostolos Trovias, for securities fraud and money laundering.
The SEC states that Trovias, who used the screen name The Bull, is an imposter who provided stock advice to buyers pretending to be an office clerk from a trading branch. Allegedly, he offered stock advice through weekly and monthly subscriptions and also as one-time transactions.
The Bull used encrypted messaging services for sharing info
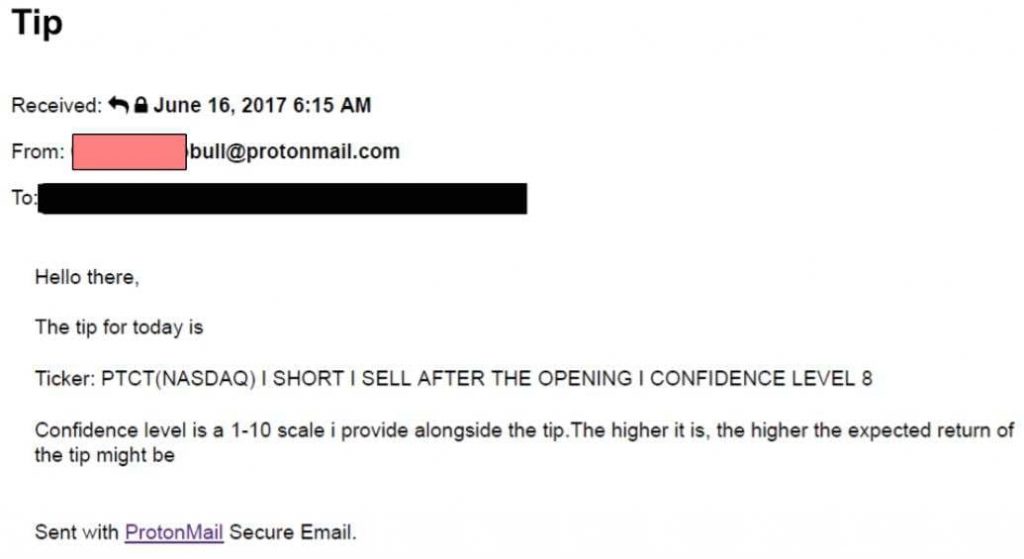
Reportedly, Apostolos Trovias used encrypted messaging services apart from the Dark Web to offer, solicit, and sell stock trading tips.
According to the United States Attorney for the Southern District of New York, Audrey Strauss, and Assistant Director-in-Charge of the New York Field Office of the Federal Bureau of Investigation, William Sweeney Jr., the accused also sold pre-release earnings and deal-related information on public firms as well.
SEE: SpaceX employee admits security fraud, insider trading on dark web
The allegations were revealed in the Indictment and Complaints that were unsealed today in a Manhattan federal court.
“Apostolos Trovias attempted to hide his insider trading scheme behind anonymizing software, screennames, and bitcoin payments,” Strauss said.
Sweeney Jr. stated that using the veils of the Dark Web and an encrypted messaging service,
“Trovias created a business model in which he sold—for profit—proprietary information from other companies, stock trading tips, pre-release earnings, and other inside information, as we allege.”
Trovias’s Scheme Exposed
According to the SEC, Trovias obtained and monetized confidential non-public business information, which included selling misappropriated stock tips according to confidential customer trading information, and selling pre-release earnings reports and deal information gathered from publicly traded firms.
According to SEC documents seen by Hackread.com. Trovias also created an online marketplace to link individuals misappropriating Inside Information to people for a commission.
In December 2016, The Bull registered for AlphaBay Market on the Dark Web, and after it was seized, he started offering stock tips about certain securities issuers on monthly and weekly subscriptions basis. From June 2017 to February 2020, he sold Inside Information directly to buyers using encrypted email and messaging services to exclusively communicated with the purchasers.
Reportedly, he sold securities issuers information for nearly $5,000 in bitcoin. In 2020, he also designed and activated a website, Inside Information Auction Site, to further facilitate the sale of non-public information for stock trading and charged for membership.
The Charges
the Athens-native is charged with one count of securities fraud and money laundering each. The charges carry a maximum penalty of 25 years in jail.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.