It is currently unclear whether a single actor is responsible for the Soul framework, but it is confirmed that it is attributed to a Chinese group.
The cybersecurity researchers at Check Point have shared their findings of a campaign discovered in late 2020 in which the initial infection vector is the same as previously associated with a Chinese APT group dubbed Sharp Panda.
In their latest campaign, government entities in Southeast Asia have been the target. Researchers state that Sharp Panda has been involved in multiple campaigns targeting Southeast Asian countries including Vietnam, Thailand, and Indonesia.
Chinese Espionage Group Drop SoulSearcher Loader
The group has changed their tactics in this campaign, as instead of using VictoryDll, they are using the new version of SoulSearcher loader to load the Soul modular framework. This framework was previously observed in another spying campaign targeting ICT, defense, and healthcare sectors in Southeast Asia.
It is currently unclear whether a single actor is responsible for the Soul framework, but it is confirmed that it is attributed to a Chinese group. In this ongoing surveillance operation, Sharp Panda specifically targeted Southeast Asian government entities using spear-phishing emails through which they gained initial access to their targets’ networks.
Email Analysis
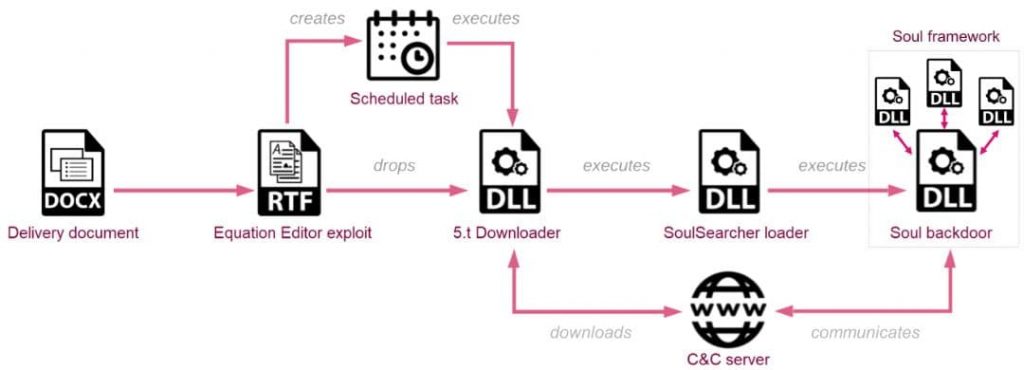
According to Check Point researchers, these emails contain a Word document with government-themed lures. The attackers leveraged a remote template for downloading and executing a malicious RTF document equipped with the RoyalRoad kit.
Once it has invaded the network, it initiates a string of in-memory loaders, comprising a custom DLL downloader the researchers named “5.t Downloader,” and another 2nd-stage loader that delivers the final payload.
The final payload previously seen in Sharp Panda campaigns was VictoryDll, which enabled remote access and data theft. In this campaign, the attackers targeted a government entity with a geo-fenced C2 server that delivered a new version of the SoulSearcher loader, which can download, decrypt, and load different modules of the Soul modular backdoor in memory.
How Does the Attack Work?
In a blog post, researchers wrote that, the downloader is dropped by RoyalRoad RTF as res6.a onto the disk and executed by a scheduled task with rundll32.exe, Start A, the functionality of which is consistent with previous Sharp Panda activities. The C2 servers of the attackers return payloads to requests from the IP addresses of their target locations due to being geofenced.
Contrary to the attackers’ previous tactics of sending encrypted data using RC4 with base64 encoding, in the new campaign the payload request is issued to the same PHP path with the host parameter specified and both MD5- hashed and in clear-text. The new version is a simpler version of string encryption, with a loop XORing an encrypted character.
What Data is Stolen?
The downloader collects sensitive device data such as the OS name, hostname, version, username, system type (32- or 64-bit), MAC addresses of the networking adapters, and antivirus software information. If the device is promising enough, the server contains the next stage executable in an encrypted format and its MDS checksum.
