The attack method of the SmugX campaign includes attackers using HTML smuggling to target victims.
Check Point Research’s (CPR) cyber threat intelligence researchers have discovered a disturbing attack trend. According to CPR’s report published on July 3, 2023, Chinese threat actors have become increasingly interested in targeting European governments, embassies, and foreign local policy-making entities. Eastern Europe is among their preferred targets, with prime targets being Slovakia, the Czech Republic, and Hungary.
This newly discovered campaign is dubbed SmugX. Researchers claim that this campaign has been active since December 2022, but they believe that it is an extension of a previously discovered campaign linked to Mustang Panda and RedDelta. Interestingly, both groups are Chinese.
As far as the attack method is concerned, research revealed that in SmugX, attackers are using HTML smuggling to target European embassies. In this method, the modular PlugX malware implant is smuggled (hidden) inside HTML documents.
Hackers use this technique to trick web security systems and evade antivirus mechanisms or security defences. HTML smuggling exploits HTML features to conceal malicious data documents from automated content filters, including them as JavaScript blobs that reassemble on the targeted device.
It is worth noting that PluxX is a commonly used tool for HTML smuggling. Multiple Chinese threat actors have used this malware previously, such as the group that targeted the Vatican in 2020 or the one that targeted the Indonesian Intelligence Service in 2021. The malware was also used to target users in Mongolia, Ghana, Papua New Guinea, Nigeria, and Zimbabwe in a USB drive-based campaign.
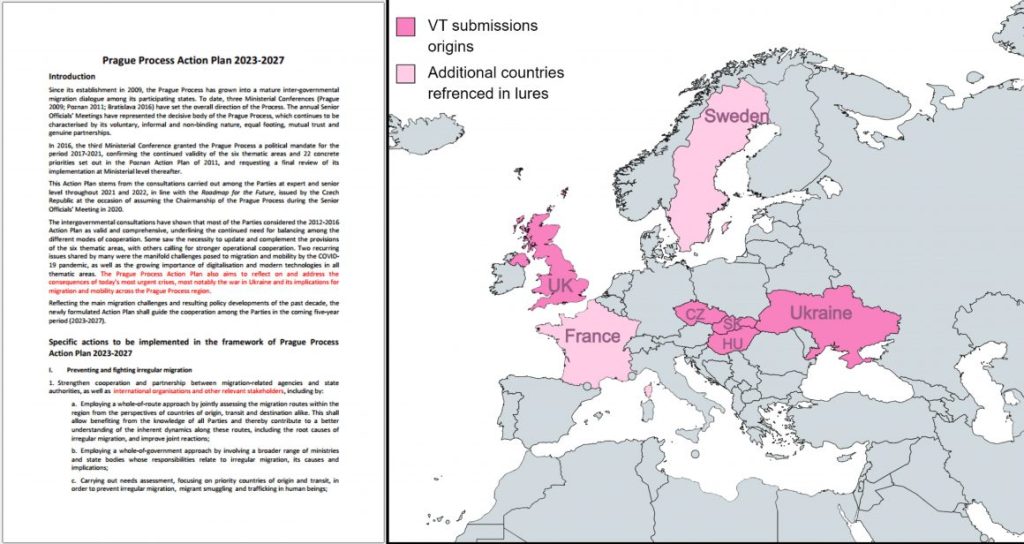
CPR researchers agree that SmugX’s primary objective is to obtain sensitive data on the foreign policies of the targeted countries. This analysis is based on the lure samples posted to the malware repository on VirusTotal. The filenames of these samples were self-explanatory.
Researchers wrote that the names strongly suggested that the attackers wanted to target diplomats and government entities, whereas the content contained mainly diplomatic-related content related to China. The attack utilizes several .docx and .pdf files containing diplomatic content.
CPR researchers obtained a letter from the Serbian embassy in Budapest, a document revealing the Swedish Presidency of the Council of the European Union’s priorities, and an invitation from the Hungarian foreign ministry for a diplomatic conference.
The researchers also discovered an article about the two Chinese human rights lawyers who had received a ten-year sentence. Here are the titles of these documents:
- 202305 Indicative Planning RELEX
- Draft Prague Process Action Plan_SOM_EN
- 2262_3_PrepCom_Proposal_next_meeting_26_April
- Comments FRANCE – EU-CELAC Summit – 4th May
- China jails two human rights lawyers for Subversion
“While none of the techniques observed in this campaign is new or unique, the combination of the different tactics, and the variety of infection chains resulting in low detection rates, enabled the threat actors to stay under the radar for quite a while,” CPR researchers noted.
CPR is still investigating and monitoring SmugX activities and will share new details soon. Please continue to visit this platform for the latest updates on SmugX.
RELATED ARTICLES
- Killnet Hits European Parliament Website with DDoS Attack
- Research sector hit in new phishing attack using Google Drive
- Fake WHO Emails on COVID-19 Drop Nerbian RAT Across Europe
- European Spyware Vendor Offering Android & iOS Device Exploits
- Zimbra email platform flaw exploited to steal European govt emails
