Previously, threat actors took over misconfigured databases to demand ransom, but now there has been a change in their tactics.
Hijacked S3 buckets or hosting sources have become a real threat, as adversaries can exploit them for “data theft and intrusion,” according to Checkmarx researcher and software engineer Guy Nachshon in his blog post published on June 15th.
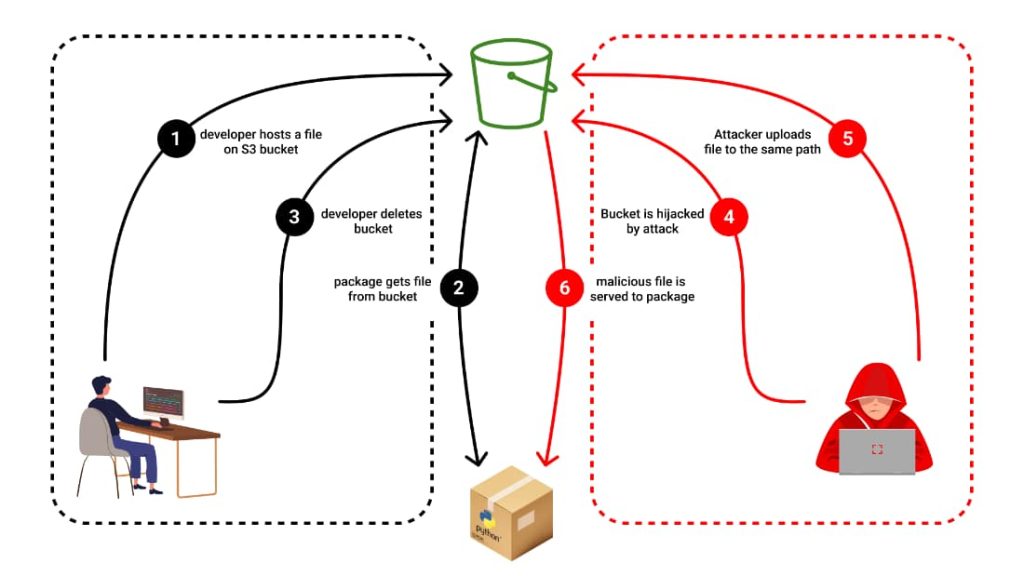
Nachshon observed a unique software supply chain attack that relied on the abandonment of an active AWS S3 bucket. The attacker has not been identified, but their modus operandi has been exposed.
According to Nachshon, threat actors can seize abandoned S3 buckets to launch malicious binaries and steal login credentials, local hostname, and machine environment variables from the device and exfiltrate the information to the attacker.
The issue was observed in an NPM package called “Bignum,” which, until version 0.13.0, relied on an AWS S3 bucket to download an add-on’s pre-built binary version called node-pre-gyp. The binary file is downloaded during the installation phase if it is hosted on an S3 bucket. However, the problem occurs when it doesn’t reach the bucket, and the software starts searching for the binary locally.
“If a package references a file from a domain on the cloud (there are multiple package managers that work only by doing that), if the maintainer has deserted the domain or did not complete his payments, an attacker can just take over his domain, and no one will know – resulting in an infected package.”
The abandoned S3 bucket was still being used in existing software as a distribution point, which the attacker noticed. They created a new S3 bucket with the same name and replaced the binary package with a malicious one that could steal and transfer user data to an external location while keeping the attacker’s identity hidden.
Since the distribution source of the binary package is an abandoned and eventually deleted S3 bucket, supply chain attackers can exploit them to target open-source repositories and packages without changing the module or modifying a single line of code.
“While this specific risk was mitigated, a quick glance through the open-source ecosystem reveals that dozens of packages are vulnerable to this same attack,” Checkmarx’s report read.
This attack can affect the distribution of software binaries, IP addresses, domain names, disused subdomains, and even externally referenced JavaScript libraries. Moreover, users who have downloaded Bignum may have also downloaded these binaries, putting their device data at risk.
What’s even more worrying is that this technique can be applied to any trusted distribution location after it has been abandoned. Threat actors can take control of the address or location of the abandoned source and use it to distribute malicious payloads.
Many developers rely on third-party, open-source software packages and components to create apps. Most of these packages depend on external components, which in turn rely on third parties. This makes for a complicated situation.
Organizations must periodically inspect their software dependencies, sub-dependencies, repositories, and hosting resources. Vetting and documenting them is essential for the constant monitoring of assets.
