Two security firms (FireEye and Mandiant), have found a group of hackers (Fin5) who specialize in credit card stealing and have till date stolen 150,000 credit cards data from many unnamed casinos.
Surprisingly, the hackers had the access to the databases of the casinos for the one complete year without being identified. The firms revealed this threat in recent “Cyber Defence Summit”.
According to the firms, most of the casinos targeted are from the region of North America and Europe and said to have targeted 12 casinos till now.
The group, Fin5, was discovered the by the firms when the researchers had an interview with some of the representatives of the group. It was found that the group has been using: “a very flat network, single domain, with very limited access controls for access to payment systems” said Mr. Jean-Georges (Representative of one of the security firms).
This discovery made security firms wonder how were they able to squeeze into the systems with such basic stuff and found out that the casino servers were vulnerable due to low investments on the security of the database.
Further, searching on the casino’s security systems the researchers found that even a basic firewall on the payment systems would have stopped this from happening or at the least had made it tough for the hackers.
Mr. Vengerik (Representative of one of the firms) rate dFin5 as professional hackers because they make their own code which helps them to access to a computer system and if they use the stolen credentials with that they can easily get hold of few more credentials by work through the active directory.
The researcher was very impressed by the way the group was working and said,
“One of the unique things about FIN5 is that in every intrusion we responded to where FIN5 has been active, legitimate access was identified. They had valid user credentials to remotely log into the network. No sexy zero-days, no remote exploits, not even spear phishing. They had credentials from somewhere.”
Moving on the tools they use for breaching the systems, they use backdoor that is very rarely used named as “Tornhull” which allowed to have far greater access into the systems. With that, they use “VPN-Flipside” which further strengthens their attacks.
The group uses GET2 Penetrator which is a brute force scanning tool that searches for remote login information and hard-coded credential.
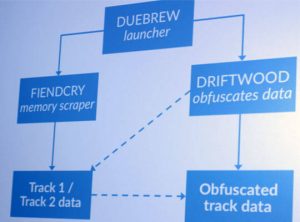
They also infect servers with RawPOS malware, which is very powerful and comes with several useful components. Like Duebrew which allows attackers to maintain persistence on the system. Within RawPOS, there is Driftwood which encodes the data stolen like in this case the credit card information.
Lastly, they use Fiendcry which is used for scraping memory.
You must be wondering why any of casinos were not named? Well, the firms never revealed this information may be due to their contract with the casinos.
But, the most surprising thing is that these hacks are not reported for years, even this one was reported about a year after it happened. Which is really surprising because by these casinos are allowing hackers to make further inroads into their database.
In 2014, the Las Vegas Sands casino faced a massive cyber attack in which Iranian hackers were found targeting the casino’s servers, wiping hard drives and shutting down its email servers.
