We have read stories regarding how email is heavily used for phishing scams by sending out fake emails that eventually lead the user into clicking a malicious link. We have grown so used to the fact that now, we seem to think email is the primary way to attack for spammers. However, here you will see how this reality has a totally different side to it.
URL Padding
Most of you may be familiar with the term ‘URL padding.’ This is the technique that has been observed by researchers at PhishLabs as being used by a majority of the spammers to target mobile users in particular.
Why mobile users you ask? Well, the simple answer to this question is that spammers have realized how careless users can get when it comes to accessing their mobile phones as compared to the case of accessing your emails on a laptop or PC.
So, let us begin with what URL padding is. Essentially, URL padding is the technique by which spammers can hide a malicious address by masquerading it in a legitimate looking domain name and hence tricking users into giving out their credentials.
How does it work?
To understand how URL padding works and why mobile phones have been the target, we first need to understand what URL padding looks like.
The following example has been provided by PhishLabs:
hxxp://m.facebook.com----------------validate----step1.rickytaylkcom/sign_in.html
As you may see, the initial address is a legitimate Facebook domain. However, the real address of this link is ‘rickytaylkcom.’ This implies that clicking this link will not lead you to Facebook but this fake address.
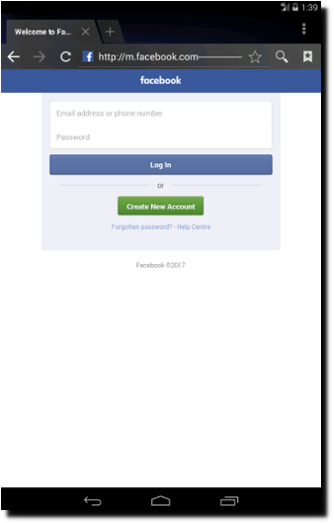
Now, if the link is sent through email, the user can easily figure out by hovering the link that the link is fake.
With a mobile phone, however, this is not the case as the browser address bar is much smaller and does not allow for the entire address to be visible. Hence, the only thing visible will be the part which shows the Facebook address. Hyphens will pad the rest.
As such, an unsuspecting user will visit the link thinking that it will redirect him/her to Facebook. However, once the link is loaded, a fake-looking page will appear that will look exactly like the login page of Facebook.
This acts as a further illusion since the user will, without much thought, enter his/her username and password, thereby revealing his/her credentials.
Why is it effective?
Researchers at PhishLabs stated that the method works well since people are more inclined to visit websites like Facebook rather than instinctively on mobiles, and do not pay much attention to things like the URL.
As such, this is indeed a well-thought-out technique that leverages upon a very specific behavior of mobile users.
According to the experts, the spam links are likely being sent through SMS messages or as notifications since links can be hidden more effectively through these channels. That is, in an email one can view the entire link by just hovering the cursor over it.
Unfortunately, this is not the case with an SMS.
The Ulterior Motive
PhishLabs has a conjecture. The researchers believe that the real motive behind these scams is to use victim’s accounts for further phishing scams. After all, attackers can scam way more easily by directly sending messages through a person’s private account.
Furthermore, since users have a single username and password, getting credentials of one social media account, may allow the attackers to infiltrate other accounts.
How to protect yourself?
There are no hi-tech methods to make yourself immune to such attacks. It is a known side-effect of being on social media and it cannot be avoided.
However, one can restrain from accessing links sent via unknown SMS messages as Facebook does not send notifications to users through a text message.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.
