A bug bounty hunter has received $50,000 from Microsoft for identifying and reporting vulnerability that would involve brute-forcing the 7-digit security code sent to a user to verify identity and access their account.
Independent security researcher and white-hat hacker Laxman Muthiyah reported a vulnerability to Microsoft that could brute-force the 7-digit security code sent to a user’s mobile number or email address to validate identity and reset the password to get access to the account.
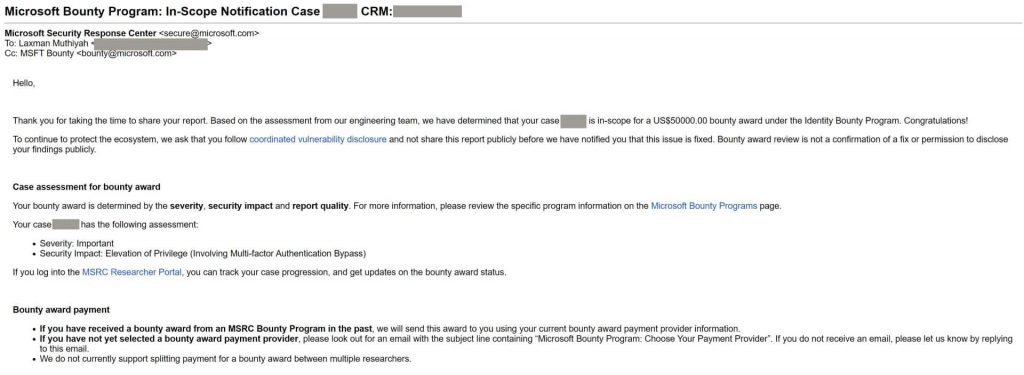
Microsoft has awarded Muthiyah a $50,000 reward under its bug bounty program for reporting the flaw that could allow a threat actor to hijack just about any Microsoft account.
Muthiyah is no stranger to identifying critical bugs. In 2019 he identified a bug that could allow anyone to carry out brute-force attacks for hacking Instagram accounts and was rewarded $30,000.
In 2015, Muthiyah identified a flaw that could allow him to delete all photos from anyone’s Facebook account.
The recent flaw is another account takeover scenario, which allows privilege escalation stemming from an authentication bypass used to verify the code sent as the account recovery process.
Bug Fixed in 2020
Microsoft fixed the bug in November 2020, much before the details were shared publicly by Muthiyah in his blog post published on Tuesday. His tests showed that out of the 1000 codes sent, just 122 got through, and the others were blocked with 1211 error code.
Despite the encryption barriers and rate-limiting checks in place to automatically prevent an attacker from submitting the 10 million code combinations automatically, Muthiyah could crack the encryption function that cloaked the security code and sent out multiple concurrent requests.
“I realized that they are blacklisting the IP address if all the requests we send don’t hit the server at the same time. A few milliseconds delay between the requests allowed the server to detect the attack and block it,” Muthiyah wrote in his blog post.
Attack Works on Accounts Not Secured by 2FA
Muthiyah claims that he could get around the rate-limiting constraint and change the password to hijack an account, but this attack only worked on accounts that weren’t secured by two-factor authentication (2FA). However, he also mentioned that it could be extended to defeat the two protection layers and modify the account’s password.
“Putting all together, an attacker has to send all the possibilities of 6 and 7 digit security codes that would be around 11 million request attempts and it has to be sent concurrently to change the password of any Microsoft account (including those with 2FA enabled).”
“It is not at all an easy process to send such a large number of concurrent requests, that would require a lot of computing resources as well as 1000s of IP address to complete the attack successfully,” Muthiyah concluded.
Did you enjoy reading this article? Don’t forget to like our page on Facebook and follow us on Twitter!