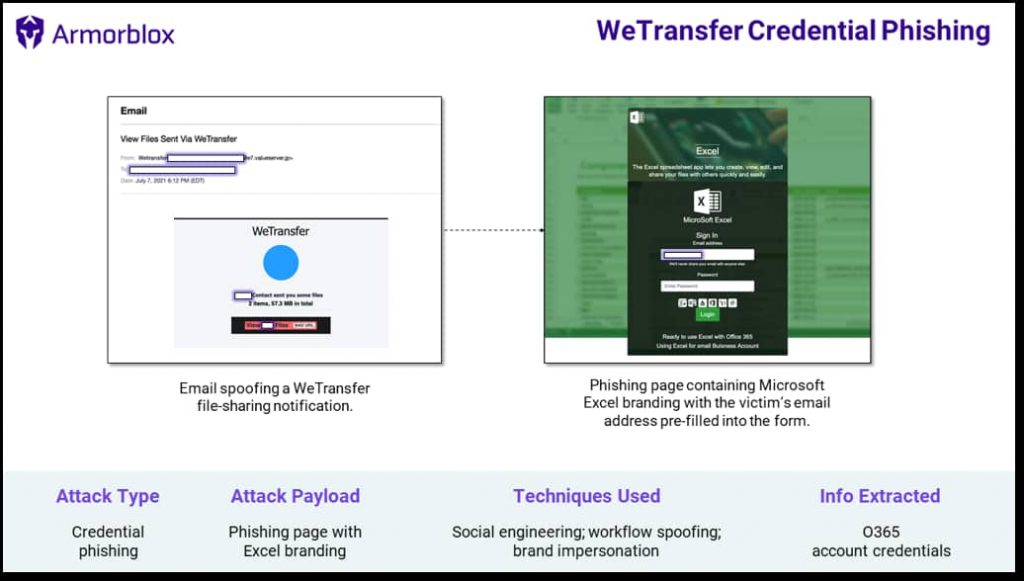
The phishing email claims that WeTransfer has shared two files with the victim, and there’s a link to view them.
According to a report from Armorblox, cybercriminals are spoofing the WeTransfer file hosting system to carry out credential phishing attacks in which spoofed email leads to a phishing page featuring Microsoft Excel branding.
The primary aim of this attack is to retrieve the victims’ Office 365 email credentials. It is worth noting that WeTransfer is used for sharing files that are too large to be sent via email.
About the Attack
The phishing email appears to be sent by WeTransfer as it bears the sender name Wetransfer and has the title View Files Sent Via WeTransfer. The similarity is enough to come across as a genuine WeTransfer email and can easily deceive unsuspecting users. The email body also makes several references to the target organization to appear legitimate.
SEE: ‘Zoom account suspended’ phishing scam steals Office 365 credentials
The email body reveals that WeTransfer has shared two files with the victim, and there’s a link to view them. When the victim clicks on View Files, the link leads them to a phishing page supposedly of Microsoft Excel.
Furthermore, it features a blurred-out spreadsheet as the background, and a form is displayed in the foreground that requires the victim to enter login credentials. It already contains the victim’s email address to create a sense of legitimacy around the entire process.
The email sender domain is a web hosting services provider called ‘valueserverjp.’ This domain is based in Japan. Last year, Infosec analyst Laur Telliskivi reported about the same domain being used in phishing attacks.
Techniques Used in the Attack
A range of techniques has been used to evade conventional email security filters and lure unsuspecting users. This includes social engineering, as the email title, content, and sender name have been designed to create a sense of “trust and urgency in the victims,” wrote Armorblox’s Mark Royall in a blog post.
Another technique used in this campaign is brand impersonation. The email’s HTML styling is eerily similar to WeTransfer, and the phishing page has been designed to appear as Microsoft Excel’s legitimate login page. The only thing that makes it appear fishy is that Microsoft is spelled as MicroSoft.
How to Stay Safe?
Be very mindful of minor inconsistencies in the sender’s name, email address, and domain name. Pay attention to the language used within the email. Don’t forget to implement multi-factor authentication (MFA) on all personal and business accounts. And never use the same password for accessing different accounts.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.

Wetransfer has added email verification to protect phishing but i think they have to add more control for phishing. Sendgb is file transfer service like wetransfer and they have more control for phishing.